标签:选择 size ide sig 防火墙 特性 单向加密 closure lis
墨菲定律墨菲定律:一种心理学效应,是由爱德华·墨菲(Edward A. Murphy)提出的,原话:如果有两种或两种以上的方式去做某件事情,而其中一种选择方式将导致灾难,则必定有人会做出这种选择
主要内容:
任何事都没有表面看起来那么简单
所有的事都会比你预计的时间长
会出错的事总会出错
如果你担心某种情况发生,那么它就更有可能发生
1、信息安全防护的目标:
保密性 Confidentiality
完整性 Integrity
数据不能被串改,要保证数据的完整性
可用性 Usability
让系统一直处于稳定可用状态
可控制性 Controlability
系统要处于可控制的范围内
不可否认性 Non-repudiation
否定事情的正确性
2、安全防护环节:
物理安全:各种设备/主机、机房环境
系统安全:主机或设备的操作系统
应用安全:各种网络服务、应用程序
网络安全:对网络访问的控制、防火墙规则
数据安全:信息的备份与恢复、加密解密
管理安全:各种保障性的规范、流程、方法
安全×××: STRIDE
Spoofing 假冒
Tampering 篡改
Repudiation 否认
Information Disclosure 信息泄漏
Denial of Service 拒绝服务
Elevation of Privilege 提升权限
安全设计基本原则:
使用成熟的安全系统
以小人之心度输入数据
外部系统是不安全的
最小授权
减少外部接口
缺省使用安全模式
安全不是似是而非
从STRIDE思考
在入口处检查
从管理上保护好你的系统
常用安全技术
认证
授权
审计
安全通信
在通信的过程中,要保证信息的安全
密码算法和协议
对称加密
公钥加密
单向加密
认证协议
凯撒密码
加密思想是在当前字母往后移三位,比如说:LOVE,ORYH,如果最后一位是Z的话继续转圈回来从A开始继续往下走
对称加密:加密和解密使用同一个密钥
DES:Data Encryption Standard,56bits
3DES:相对于DES的三倍加密方式
AES:Advanced (128, 192, 256bits)
Blowfish,Twofish
IDEA,RC6,CAST5
特性:
1、加密、解密使用同一个密钥,效率高
2、将原始数据分割成固定大小的块,逐个进行加密
缺陷:
1、密钥过多
2、密钥分发
3、数据来源无法确认
算法的几个要求:
1、公钥可以公开
2、key
算法和密钥配合起来一块使用,密钥不公开,保证用不同的密钥结合相同算法加密出来的结果是破解不了的
公钥加密:密钥是成对出现
公钥:公开给所有人;public key
私钥:自己留存,必须保证其私密性;secret key
特点:
用公钥加密数据,只能使用与之配对的私钥解密;反之亦然
功能:
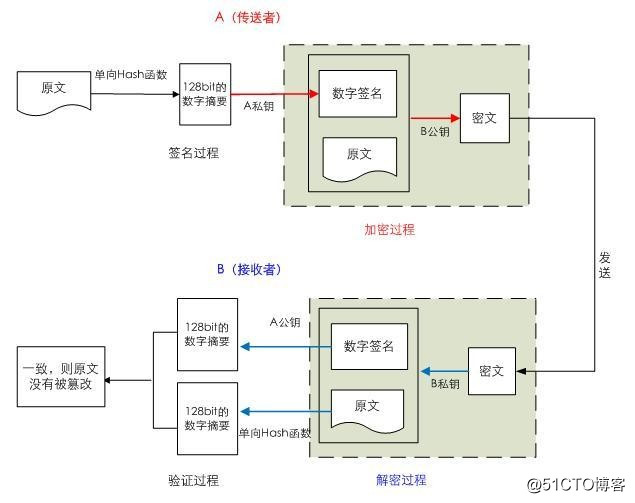
数字签名:主要在于让接收方确认发送方身份
对称密钥交换:发送方用对方的公钥加密一个对称密钥后发送给对方
数据加密:适合加密较小数据
缺点:
密钥长,加密解密效率低下
算法:
RSA(加密,数字签名)
DSA(数字签名)
ELGamal
基于一对公钥/密钥对
用密钥对中的一个加密,另一个解密
实现加密:
接收者
生成公钥/密钥对:P和S
公开公钥P,保密密钥S
发送者
使用接收者的公钥来加密消息M
将P(M)发送给接收者
接收者
使用密钥S来解密:M=S(P(M))
结合签名和加密
分离签名
将任意数据缩小成固定大小的“指纹”
任意长度输入
固定长度输出
若修改数据,指纹也会改变(“不会产生冲突”)
无法从指纹中重新生成数据(“单向”)
功能:
数据完整性
常见算法
md5: 128bits、sha1: 160bits、sha224 、sha256、sha384、sha512
常用工具
md5sum | sha1sum [ --check ] file
openssl、gpg
rpm -V
密钥交换: IKE( Internet Key Exchange )
公钥加密:
DH (Deffie-Hellman):生成会话密钥,由惠特菲尔德·迪菲(Bailey Whitfield Diffie)和马丁·赫尔曼(Martin Edward Hellman)在1976年发表
参看:https://en.wikipedia.org/wiki/Diffie%E2%80%93Hellman_key_exchange
DH:
A: g,p 协商生成公开的整数g, 大素数p
B: g,p
A:生成隐私数据 :a (a<p ),计算得出 g^a%p,发送给B
B:生成隐私数据 :b,计算得出 g^b%p,发送给A
A:计算得出 [(g^b%p)^a] %p = g^ab%p,生成为密钥
B:计算得出 [(g^a%p)^b] %p = g^ab%p,生成为密钥
文件完整性的两种实施方式
被安装的文件
MD5单向散列
rpm --verify package_name (or -V)
发行的软件包文件
GPG公钥签名
rpm --import /etc/pki/rpm-gpg/RPM-GPG-KEY-redhat*
rpm --checksig pakage_file_name (or -K)
对称加密file文件
gpg -c file
ls file.gpg
[root@node1 /data]#gpg -c fstab 在另一台主机上解密file
gpg -o file -d file.gpg
[root@node2 /app]#gpg -o f1 -d fstab.gpg 在hostB主机上用公钥加密,在hostA主机上解密
在hostA主机上生成公钥/私钥对
gpg --gen-key
在hostA主机上查看公钥
gpg --list-keys
在hostA主机上导出公钥到cobbler.pubkey
gpg -a --export -o cobbler.pubkey
从hostA主机上复制公钥文件到需加密的B主机上
scp cobbler.pubkey hostB:
在需加密数据的hostB主机上生成公钥/私钥对
gpg --list-keys
gpg --gen-key
在hostB主机上导入公钥
gpg --import cobbler.pubkey
gpg --list-keys
用从hostA主机导入的公钥,加密hostB主机的文件file,生成file.gpg
gpg -e -r cobbler file
file file.gpg
复制加密文件到hostA主机
scp fstab.gpg hostA:
在hostA主机解密文件
gpg -d file.gpg
gpg -o file -d file.gpg
删除公钥和私钥
gpg --delete-keys cobbler
gpg --delete-secret-keys cobbler
[root@node1 /data]#gpg --gen-key
gpg (GnuPG) 2.0.22; Copyright (C) 2013 Free Software Foundation, Inc.
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
gpg: keyring `/root/.gnupg/secring.gpg‘ created
Please select what kind of key you want:
(1) RSA and RSA (default)
(2) DSA and Elgamal
(3) DSA (sign only)
(4) RSA (sign only)
Your selection?
RSA keys may be between 1024 and 4096 bits long.
What keysize do you want? (2048) 1024
Requested keysize is 1024 bits
Please specify how long the key should be valid.
0 = key does not expire
<n> = key expires in n days
<n>w = key expires in n weeks
<n>m = key expires in n months
<n>y = key expires in n years
Key is valid for? (0) 0
Key does not expire at all
Is this correct? (y/N) y
GnuPG needs to construct a user ID to identify your key.
Real name: cobbler
Email address: cobbler@dklwj.com
Comment: test
You selected this USER-ID:
"cobbler (test) <cobbler@dklwj.com>"
Change (N)ame, (C)omment, (E)mail or (O)kay/(Q)uit? O
We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.
We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.
gpg: /root/.gnupg/trustdb.gpg: trustdb created
gpg: key FD4CFEF9 marked as ultimately trusted
public and secret key created and signed.
gpg: checking the trustdb
gpg: 3 marginal(s) needed, 1 complete(s) needed, PGP trust model
gpg: depth: 0 valid: 1 signed: 0 trust: 0-, 0q, 0n, 0m, 0f, 1u
pub 1024R/FD4CFEF9 2018-09-12
Key fingerprint = 3D2D 3674 D945 1271 919B 2671 9229 A6E0 FD4C FEF9
uid cobbler (test) <cobbler@dklwj.com>
sub 1024R/7CD048CE 2018-09-12
在/root/.gnupg
[root@node1 ~/.gnupg]#ll
total 28
-rw------- 1 root root 7680 Sep 12 21:13 gpg.conf
drwx------ 2 root root 6 Sep 12 21:13 private-keys-v1.d
-rw------- 1 root root 1872 Sep 12 21:42 pubring.gpg
-rw------- 1 root root 1872 Sep 12 21:42 pubring.gpg~
-rw------- 1 root root 600 Sep 12 21:42 random_seed
-rw------- 1 root root 3838 Sep 12 21:42 secring.gpg
srwxr-xr-x 1 root root 0 Sep 12 21:28 S.gpg-agent
-rw------- 1 root root 1360 Sep 12 21:42 trustdb.gpg
查看生成的公钥
[root@node1 ~/.gnupg]#gpg --list-key
/root/.gnupg/pubring.gpg
------------------------
pub 1024R/FD4CFEF9 2018-09-12
uid cobbler (test) <cobbler@dklwj.com>
sub 1024R/7CD048CE 2018-09-12
到处为易读的格式传给对方
[root@node3 ~]]#gpg -a --export -o cobbler.pubkey
导入客户端的公钥
[root@node1 ~/.gnupg]#gpg --import /data/cobbler.pubkey
gpg: key A24FC96C: public key "cobbler" imported
gpg: Total number processed: 1
gpg: imported: 1 (RSA: 1)
查看当前机器上的所有公钥
[root@node1 ~/.gnupg]#gpg --list-key
使用cobbler的公钥加密
[root@node1 /data]#gpg -e -r cobbler fstab
gpg: 98C7C0F4: There is no assurance this key belongs to the named user
pub 2048R/98C7C0F4 2018-09-12 cobbler
Primary key fingerprint: 6FB7 75D3 2534 B4F8 7E1C 4FD2 DCEF 398E A24F C96C
Subkey fingerprint: EE01 7CF1 D62D A366 7C15 D36A 0043 0625 98C7 C0F4
It is NOT certain that the key belongs to the person named
in the user ID. If you *really* know what you are doing,
you may answer the next question with yes.
Use this key anyway? (y/N) y
查看刚加密的文件
[root@node1 /data]#ll
total 16
-rw-r--r-- 1 root root 1683 Sep 12 22:23 cobbler.pubkey
-rw-r--r-- 1 root root 541 Sep 12 21:13 fstab
-rw-r--r-- 1 root root 609 Sep 12 22:32 fstab.gpg
-rw-r--r-- 1 root root 316 Sep 12 21:13 fstab.gpg.bak
把加密好的文件传给客户端然后通过客户端的私钥解密
[root@node1 /data]#scp fstab.gpg 172.20.7.53:/data
客户端解密的时候不用需要再输入密码来解密了自动解密,
[root@node3 /data]]#gpg -d fstab.gpg
gpg: encrypted with 2048-bit RSA key, ID 98C7C0F4, created 2018-09-12
"cobbler"
#
# /etc/fstab
# Created by anaconda on Wed Jul 18 20:40:37 2018
#
# Accessible filesystems, by reference, are maintained under ‘/dev/disk‘
# See man pages fstab(5), findfs(8), mount(8) and/or blkid(8) for more info
#
/dev/mapper/centos-root / xfs defaults 0 0
UUID=3d4ae911-238f-4436-82eb-5bb4660c38c7 /boot xfs defaults 0 0
/dev/mapper/centos-data /data xfs defaults 0 0
/dev/mapper/centos-swap swap swap defaults 0 0
不过-d只是在屏幕上显示出来要想解开需要加上-o 指定新文件名称
[root@node3 /data]]#gpg -o fs -d fstab.gpg
gpg: encrypted with 2048-bit RSA key, ID 98C7C0F4, created 2018-09-12
"cobbler"
查看文件
[root@node3 /data]]#ls
fs fstab.gpg lost+found
[root@node3 /data]]#cat fs
#
# /etc/fstab
# Created by anaconda on Wed Jul 18 20:40:37 2018
#
# Accessible filesystems, by reference, are maintained under ‘/dev/disk‘
# See man pages fstab(5), findfs(8), mount(8) and/or blkid(8) for more info
#
/dev/mapper/centos-root / xfs defaults 0 0
UUID=3d4ae911-238f-4436-82eb-5bb4660c38c7 /boot xfs defaults 0 0
/dev/mapper/centos-data /data xfs defaults 0 0
/dev/mapper/centos-swap swap swap defaults 0 0
现在所有的公钥都不想要了,删除它
[root@node1 /data]#gpg --delete-keys cobbler
gpg (GnuPG) 2.0.22; Copyright (C) 2013 Free Software Foundation, Inc.
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
pub 2048R/A24FC96C 2018-09-12 cobbler
Delete this key from the keyring? (y/N) y
不过在删除第二个的时候它会提示你先让你删除私钥,
[root@node1 /data]#gpg --delete-keys zabbix
gpg (GnuPG) 2.0.22; Copyright (C) 2013 Free Software Foundation, Inc.
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
gpg: there is a secret key for public key "zabbix"!
gpg: use option "--delete-secret-keys" to delete it first.
[root@node1 /data]#gpg --delete-secret-keys zabbix
gpg (GnuPG) 2.0.22; Copyright (C) 2013 Free Software Foundation, Inc.
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
sec 2048R/799524A3 2018-09-12 zabbix
Delete this key from the keyring? (y/N) y
This is a secret key! - really delete? (y/N) y
[root@node1 /data]#gpg --delete-keys zabbix
gpg (GnuPG) 2.0.22; Copyright (C) 2013 Free Software Foundation, Inc.
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
pub 2048R/799524A3 2018-09-12 zabbix
Delete this key from the keyring? (y/N) y
[root@node1 /data]#标签:选择 size ide sig 防火墙 特性 单向加密 closure lis
原文地址:http://blog.51cto.com/dklwj/2175918