标签:
Centos7 install Openstack - (第二节)添加认证服务(Keystone)
我的blog地址:http://www.cnblogs.com/caoguo
根据openstack官方文档配置
官方文档地址: http://docs.openstack.org/juno/install-guide/install/yum/content/#
0x01.认证服务安装与配置(控制节点)
[root@controller ~]# mysql -uroot -p MariaDB [(none)]> CREATE DATABASE keystone; MariaDB [(none)]> GRANT ALL PRIVILEGES ON keystone.* TO ‘keystone‘@‘localhost‘ -> IDENTIFIED BY ‘KEYSTONE_DBPASS‘; MariaDB [(none)]> GRANT ALL PRIVILEGES ON keystone.* TO ‘keystone‘@‘%‘ -> IDENTIFIED BY ‘KEYSTONE_DBPASS‘; MariaDB [(none)]> flush privileges;
[root@controller ~]# openssl rand -hex 10 cdda1486bf623ac74d53 [root@controller ~]# yum install -y openstack-keystone python-keystoneclient [root@controller ~]# cp -rf /etc/keystone/keystone.conf /etc/keystone/keystone.conf.old
[root@controller ~]# vi /etc/keystone/keystone.conf #增加一下配置就可以了 [DEFAULT] admin_token = cdda1486bf623ac74d53 verbose = True [database] connection = mysql://keystone:KEYSTONE_DBPASS@controller/keystone [token] provider = keystone.token.providers.uuid.Provider driver = keystone.token.persistence.backends.sql.Token [revoke] driver = keystone.contrib.revoke.backends.sql.Revoke
[root@controller ~]# keystone-manage pki_setup --keystone-user keystone --keystone-group keystone [root@controller ~]# chown -R keystone:keystone /var/log/keystone [root@controller ~]# chown -R keystone:keystone /etc/keystone/ssl [root@controller ~]# chmod -R o-rwx /etc/keystone/ssl [root@controller ~]# su -s /bin/sh -c "keystone-manage db_sync" keystone [root@controller ~]# systemctl enable openstack-keystone.service [root@controller ~]# systemctl start openstack-keystone.service
0x02. Create tenants, users, and roles(控制节点)
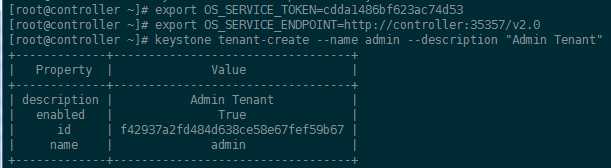
[root@controller ~]# export OS_SERVICE_TOKEN=cdda1486bf623ac74d53 [root@controller ~]# export OS_SERVICE_ENDPOINT=http://controller:35357/v2.0
2-1. Create an administrative tenant, user, and role for administrative operations in your environment:
a. Create the admin tenant:(创建租户admin)
[root@controller ~]# keystone tenant-create --name admin --description "Admin Tenant" +-------------+----------------------------------+ | Property | Value | +-------------+----------------------------------+ | description | Admin Tenant | | enabled | True | | id | f42937a2fd484d638ce58e67fef59b67 | | name | admin | +-------------+----------------------------------+
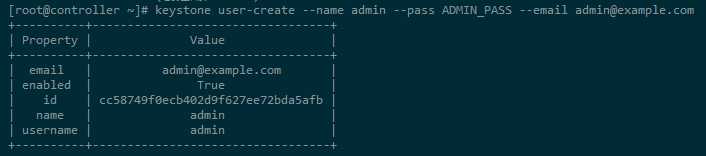
b. Create the admin user:(创建用户admin)
[root@controller ~]# keystone user-create --name admin --pass ADMIN_PASS --email admin@example.com
+----------+----------------------------------+
| Property | Value |
+----------+----------------------------------+
| email | admin@example.com |
| enabled | True |
| id | cc58749f0ecb402d9f627ee72bda5afb |
| name | admin |
| username | admin |
+----------+----------------------------------+
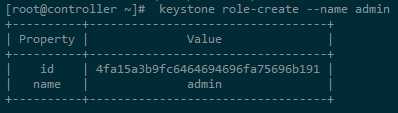
c. Create the admin role:(创建角色admin)
[root@controller ~]# keystone role-create --name admin
+----------+----------------------------------+
| Property | Value |
+----------+----------------------------------+
| id | 4fa15a3b9fc6464694696fa75696b191 |
| name | admin |
+----------+----------------------------------+
d. Add the admin role to the admin tenant and user:(添加用户到租户以及角色中)
[root@controller ~]# keystone user-role-add --user admin --tenant admin --role admin
2-2. Create a demo tenant and user for typical operations in your environment:
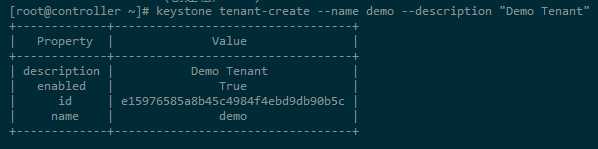
a. Create the demo tenant:(创建租户demo)
[root@controller ~]# keystone tenant-create --name demo --description "Demo Tenant" +-------------+----------------------------------+ | Property | Value | +-------------+----------------------------------+ | description | Demo Tenant | | enabled | True | | id | e15976585a8b45c4984f4ebd9db90b5c | | name | demo | +-------------+----------------------------------+
b. Create the demo user under the demo tenant:(添加demo用户到租户demo中)
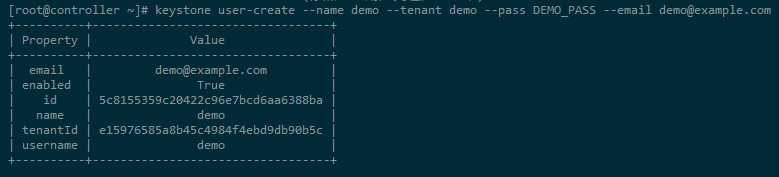
[root@controller ~]# keystone user-create --name demo --tenant demo --pass DEMO_PASS --email demo@example.com
+----------+----------------------------------+
| Property | Value |
+----------+----------------------------------+
| email | demo@example.com |
| enabled | True |
| id | 5c8155359c20422c96e7bcd6aa6388ba |
| name | demo |
| tenantId | e15976585a8b45c4984f4ebd9db90b5c |
| username | demo |
+----------+----------------------------------+
2-3.OpenStack services also require a tenant, user, and role to interact with other services.
Each service typically requires creating one or more unique users with the admin role
under the service tenant
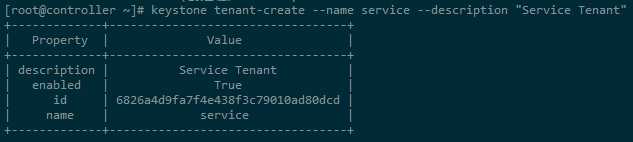
a. Create the service tenant:(创建租户service)
[root@controller ~]# keystone tenant-create --name service --description "Service Tenant" +-------------+----------------------------------+ | Property | Value | +-------------+----------------------------------+ | description | Service Tenant | | enabled | True | | id | 6826a4d9fa7f4e438f3c79010ad80dcd | | name | service | +-------------+----------------------------------+
0x03. Create the service entity and API endpoint(控制节点)
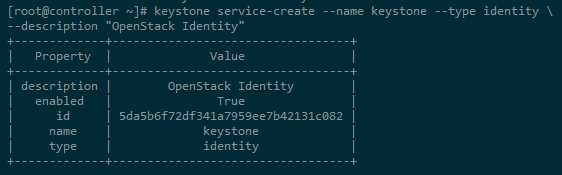
3-1. Create the service entity for the Identity service:
[root@controller ~]# keystone service-create --name keystone --type identity --description "OpenStack Identity" +-------------+----------------------------------+ | Property | Value | +-------------+----------------------------------+ | description | OpenStack Identity | | enabled | True | | id | 5da5b6f72df341a7959ee7b42131c082 | | name | keystone | | type | identity | +-------------+----------------------------------+
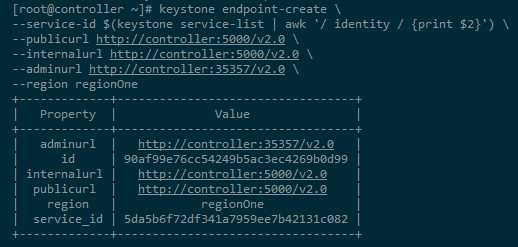
3-2. Create the Identity service API endpoints:
[root@controller ~]# keystone endpoint-create --service-id $(keystone service-list | awk ‘/ identity / {print $2}‘) --publicurl http://controller:5000/v2.0 \ --internalurl http://controller:5000/v2.0 \ --adminurl http://controller:35357/v2.0 \ --region regionOne +-------------+----------------------------------+ | Property | Value | +-------------+----------------------------------+ | adminurl | http://controller:35357/v2.0 | | id | 90af99e76cc54249b5ac3ec4269b0d99 | | internalurl | http://controller:5000/v2.0 | | publicurl | http://controller:5000/v2.0 | | region | regionOne | | service_id | 5da5b6f72df341a7959ee7b42131c082 | +-------------+----------------------------------+
0x04. 确认以上操作(控制节点)
4-1. 销毁变量
[root@controller ~]# unset OS_SERVICE_TOKEN OS_SERVICE_ENDPOINT
4-2. 验证token
[root@controller ~]# keystone --os-tenant-name admin --os-username admin --os-password ADMIN_PASS --os-auth-url http://controller:35357/v2.0 token-get +-----------+----------------------------------+ | Property | Value | +-----------+----------------------------------+ | expires | 2015-11-01T09:43:34Z | | id | 6ce0cc1d7cf94cd39f66f8cad8d78da1 | | tenant_id | f42937a2fd484d638ce58e67fef59b67 | | user_id | cc58749f0ecb402d9f627ee72bda5afb | +-----------+----------------------------------+
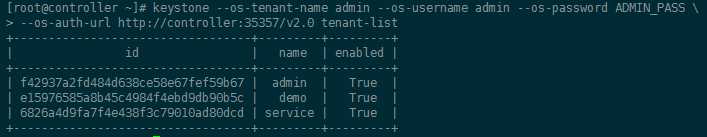
4-3.租户列表
[root@controller ~]# keystone --os-tenant-name admin --os-username admin --os-password ADMIN_PASS --os-auth-url http://controller:35357/v2.0 tenant-list +----------------------------------+---------+---------+ | id | name | enabled | +----------------------------------+---------+---------+ | f42937a2fd484d638ce58e67fef59b67 | admin | True | | e15976585a8b45c4984f4ebd9db90b5c | demo | True | | 6826a4d9fa7f4e438f3c79010ad80dcd | service | True | +----------------------------------+---------+---------+
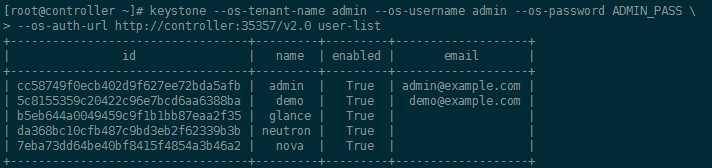
4-4. 用户列表
[root@controller ~]# keystone --os-tenant-name admin --os-username admin --os-password ADMIN_PASS --os-auth-url http://controller:35357/v2.0 user-list +----------------------------------+-------+---------+------------------+ | id | name | enabled | email | +----------------------------------+-------+---------+------------------+ | cc58749f0ecb402d9f627ee72bda5afb | admin | True | admin@example.com | | 5c8155359c20422c96e7bcd6aa6388ba | demo | True | demo@example.com | +----------------------------------+-------+---------+------------------+
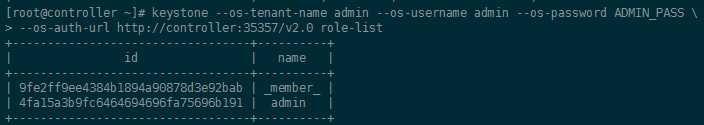
4-5. 角色列表
[root@controller ~]# keystone --os-tenant-name admin --os-username admin --os-password ADMIN_PASS --os-auth-url http://controller:35357/v2.0 role-list +----------------------------------+----------+ | id | name | +----------------------------------+----------+ | 9fe2ff9ee4384b1894a90878d3e92bab | _member_ | | 4fa15a3b9fc6464694696fa75696b191 | admin | +----------------------------------+----------+
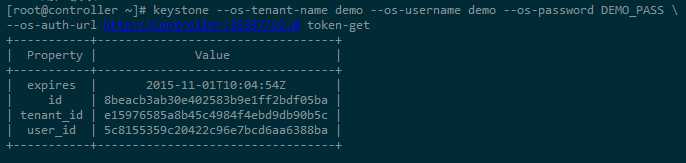
4-6. demo用户获取token
[root@controller ~]# keystone --os-tenant-name demo --os-username demo --os-password DEMO_PASS --os-auth-url http://controller:35357/v2.0 token-get +-----------+----------------------------------+ | Property | Value | +-----------+----------------------------------+ | expires | 2015-11-01T10:04:54Z | | id | 8beacb3ab30e402583b9e1ff2bdf05ba | | tenant_id | e15976585a8b45c4984f4ebd9db90b5c | | user_id | 5c8155359c20422c96e7bcd6aa6388ba | +-----------+----------------------------------+
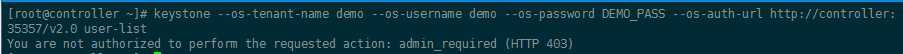
4-7. 尝试无权限访问
[root@controller ~]# keystone --os-tenant-name demo --os-username demo --os-password DEMO_PASS > --os-auth-url http://controller:35357/v2.0 user-list You are not authorized to perform the requested action: admin_required (HTTP 403)
0x05. Create OpenStack client environment scripts(控制节点)
5-1. 添加admin的环境变量
[root@controller ~]# vi admin-openrc.s export OS_TENANT_NAME=admin export OS_USERNAME=admin export OS_PASSWORD=ADMIN_PASS export OS_AUTH_URL=http://controller:35357/v2.0
5-2. 添加demo用户的环境变量
[root@controller ~]# vi demo-openrc.sh export OS_TENANT_NAME=demo export OS_USERNAME=demo export OS_PASSWORD=DEMO_PASS export OS_AUTH_URL=http://controller:5000/v2.0
Centos7 Openstack - (第二节)添加认证服务(Keystone)
标签:
原文地址:http://www.cnblogs.com/caoguo/p/4934414.html