标签:show 时区 jin 服务 serve 数据 ntp服务 check timezone
故障类型:楼栋某几间房间出现网络慢的情况
网关交换机型号:Ruijie 10G Routing Switch(S5750-24GT/12SFP) By Ruijie Network
日志:
*Sep 12 04:10:39: %ARPGUARD-4-DOS_DETECTED: ARP DoS attack was detected.
*Sep 12 04:11:01: %ARPGUARD-4-PORT_ATTACKED: ARP DoS attack was detected on port Gi0/6.
*Sep 12 04:11:25: %ARPGUARD-4-DOS_DETECTED: ARP DoS attack was detected.
*Sep 12 04:12:56: %ARPGUARD-4-DOS_DETECTED: ARP DoS attack was detected.
*Sep 12 04:14:51: %ARPGUARD-4-DOS_DETECTED: ARP DoS attack was detected.
查看Gi0/6口接入交换机
型号:Ruijie Gigabit Security & Intelligence Access Switch (S2628G-E) By Ruijie Networks
日志:
*Sep 12 04:35:54: %NFPP_DHCPV6_GUARD-4-PORT_ATTACKED: DHCPv6 DoS attack was detected on port Fa0/11.(2018-9-12 4:30:12)
*Sep 12 04:36:24: %NFPP_DHCPV6_GUARD-4-DOS_DETECTED: Host<IP=N/A,MAC=00e0.705d.1ef0,port=Fa0/11,VLAN=4011> was detected.(2018-9-12 4:31:43)
*Sep 12 04:36:54: %NFPP_DHCPV6_GUARD-4-PORT_ATTACKED: DHCPv6 DoS attack was detected on port Fa0/11.(2018-9-12 4:31:43)
*Sep 12 04:37:24: %NFPP_DHCPV6_GUARD-4-DOS_DETECTED: Host<IP=N/A,MAC=3497.f6b7.d88e,port=Fa0/11,VLAN=4011> was detected.(2018-9-12 4:32:54)
*Sep 12 04:37:54: %NFPP_DHCPV6_GUARD-4-PORT_ATTACKED: DHCPv6 DoS attack was detected on port Fa0/11.(2018-9-12 4:32:54)
*Sep 12 04:38:24: %NFPP_DHCPV6_GUARD-4-DOS_DETECTED: Host<IP=N/A,MAC=a81e.840c.0ba8,port=Fa0/11,VLAN=4011> was detected.(2018-9-12 4:33:18)
*Sep 12 04:38:54: %NFPP_DHCPV6_GUARD-4-DOS_DETECTED: Host<IP=N/A,MAC=408d.5ca2.f75e,port=Fa0/11,VLAN=4011> was detected.(2018-9-12 4:33:18)
*Sep 12 04:39:24: %NFPP_DHCPV6_GUARD-4-DOS_DETECTED: Host<IP=N/A,MAC=00e0.705e.0ea9,port=Fa0/11,VLAN=4011> was detected.(2018-9-12 4:33:19)
*Sep 12 04:39:54: %NFPP_DHCPV6_GUARD-4-DOS_DETECTED: Host<IP=N/A,MAC=d017.c2cf.5586,port=Fa0/11,VLAN=4011> was detected.(2018-9-12 4:33:41)
*Sep 12 04:40:24: %NFPP_DHCPV6_GUARD-4-DOS_DETECTED: Host<IP=N/A,MAC=fc45.963e.cab9,port=Fa0/11,VLAN=4011> was detected.(2018-9-12 4:34:25)
*Sep 12 04:40:54: %NFPP_DHCPV6_GUARD-4-DOS_DETECTED: Host<IP=N/A,MAC=28d2.44f9.c5f1,port=Fa0/11,VLAN=4011> was detected.(2018-9-12 4:35:10)
*Sep 12 04:41:24: %NFPP_DHCPV6_GUARD-4-PORT_ATTACKED: DHCPv6 DoS attack was detected on port Fa0/11.(2018-9-12 4:35:11)
*Sep 12 04:41:54: %NFPP_DHCPV6_GUARD-4-DOS_DETECTED: Host<IP=N/A,MAC=d8cb.8ac4.62c4,port=Fa0/11,VLAN=4011> was detected.(2018-9-12 4:35:59)
*Sep 12 04:42:24: %NFPP_DHCPV6_GUARD-4-DOS_DETECTED: Host<IP=N/A,MAC=4ccc.6a7e.5a85,port=Fa0/11,VLAN=4011> was detected.(2018-9-12 4:35:59)
*Sep 12 04:42:54: %NFPP_DHCPV6_GUARD-4-DOS_DETECTED: Host<IP=N/A,MAC=3497.f611.bd11,port=Fa0/11,VLAN=4011> was detected.(2018-9-12 4:35:59)
*Sep 12 04:43:24: %NFPP_DHCPV6_GUARD-4-PORT_ATTACKED: DHCPv6 DoS attack was detected on port Fa0/11.(2018-9-12 4:36:44)
*Sep 12 04:43:54: %NFPP_DHCPV6_GUARD-4-DOS_DETECTED: Host<IP=N/A,MAC=1c1b.0d11.c890,port=Fa0/11,VLAN=4011> was detected.(2018-9-12 4:37:8)
*Sep 12 04:44:24: %NFPP_DHCPV6_GUARD-4-DOS_DETECTED: Host<IP=N/A,MAC=1c6f.658e.2fb3,port=Fa0/11,VLAN=4011> was detected.(2018-9-12 4:37:8)
*Sep 12 04:44:54: %NFPP_DHCPV6_GUARD-4-DOS_DETECTED: Host<IP=N/A,MAC=00e0.4c70.439e,port=Fa0/11,VLAN=4011> was detected.(2018-9-12 4:38:14)
*Sep 12 04:45:24: %NFPP_DHCPV6_GUARD-4-PORT_ATTACKED: DHCPv6 DoS attack was detected on port Fa0/11.(2018-9-12 4:38:15)
*Sep 12 04:45:54: %NFPP_DHCPV6_GUARD-4-DOS_DETECTED: Host<IP=N/A,MAC=408d.5cd3.7a61,port=Fa0/11,VLAN=4011> was detected.(2018-9-12 4:39:29)
*Sep 12 04:46:24: %NFPP_DHCPV6_GUARD-4-PORT_ATTACKED: DHCPv6 DoS attack was detected on port Fa0/11.(2018-9-12 4:39:29)
*Sep 12 04:46:54: %NFPP_DHCPV6_GUARD-4-DOS_DETECTED: Host<IP=N/A,MAC=f832.e475.a81f,port=Fa0/11,VLAN=4011> was detected.(2018-9-12 4:41:22)
*Sep 12 04:47:24: %NFPP_DHCPV6_GUARD-4-PORT_ATTACKED: DHCPv6 DoS attack was detected on port Fa0/11.(2018-9-12 4:41:23)
*Sep 12 04:47:54: %NFPP_DHCPV6_GUARD-4-DOS_DETECTED: Host<IP=N/A,MAC=fc45.963e.cab9,port=Fa0/11,VLAN=4011> was detected.(2018-9-12 4:41:48)
*Sep 12 04:48:24: %NFPP_DHCPV6_GUARD-4-PORT_ATTACKED: DHCPv6 DoS attack was detected on port Fa0/11.(2018-9-12 4:41:49)
*Sep 12 04:48:54: %NFPP_DHCPV6_GUARD-4-DOS_DETECTED: Host<IP=N/A,MAC=b888.e3a8.9287,port=Fa0/11,VLAN=4011> was detected.(2018-9-12 4:43:46)
*Sep 12 04:49:24: %NFPP_DHCPV6_GUARD-4-PORT_ATTACKED: DHCPv6 DoS attack was detected on port Fa0/11.(2018-9-12 4:43:46)
*Sep 12 04:49:54: %NFPP_DHCPV6_GUARD-4-DOS_DETECTED: Host<IP=N/A,MAC=1c1b.0d11.c890,port=Fa0/11,VLAN=4011> was detected.(2018-9-12 4:44:8)
*Sep 12 04:50:24: %NFPP_DHCPV6_GUARD-4-DOS_DETECTED: Host<IP=N/A,MAC=fc45.963e.c9f1,port=Fa0/11,VLAN=4011> was detected.(2018-9-12 4:44:32)
1个端口下怎么可能会有这么多mac地址?
时间不对,先设置下时间:
进入config模式,
配置ntp服务器地址:ntp server ip
配置时区:clock timezone beijing 8
连接用户的接口开启IP Source Guard功能
Ruijie(config)#interface range fastEthernet 0/1-24
Ruijie(config-if-range)#ip verify source port-security
开启源IP+MAC的报文检测,将DHCP Snooping形成的snooping表写入地址绑定数据库中,请正确配置ip verfiy soure port-security, 不要使用ip verify source(仅绑定IP),部分产品存在限制,只绑定IP的情况下可能出现异常。
Ruijie(config-if-range)#arp-check
开启该功能后,对于接口收到的ARP报文会检测ARP报文字段里面的Sender IP及Sender MAC,与地址绑定库中的IP及MAC进行匹配,如果匹配将放行,否则丢弃该ARP报文
查看IP地址绑定表
S08CT# show ip dhcp snooping binding
开了这些之后发现攻击还是存在:
*Sep 11 20:45:40: %NFPP_DHCPV6_GUARD-4-DOS_DETECTED: Host<IP=N/A,MAC=2047.476e.7ab7,port=Fa0/11,VLAN=4011> was detected.(2018-9-11 20:43:42)
*Sep 11 20:46:10: %NFPP_DHCPV6_GUARD-4-PORT_ATTACKED: DHCPv6 DoS attack was detected on port Fa0/11.(2018-9-11 20:43:42)
*Sep 11 20:46:40: %NFPP_DHCPV6_GUARD-4-DOS_DETECTED: Host<IP=N/A,MAC=3497.f6d0.4dac,port=Fa0/11,VLAN=4011> was detected.(2018-9-11 20:43:48)
*Sep 11 20:47:10: %NFPP_DHCPV6_GUARD-4-DOS_DETECTED: Host<IP=N/A,MAC=1803.7394.c867,port=Fa0/11,VLAN=4011> was detected.(2018-9-11 20:43:48)
*Sep 11 20:47:40: %NFPP_DHCPV6_GUARD-4-DOS_DETECTED: Host<IP=N/A,MAC=c8d3.ffdd.ce75,port=Fa0/11,VLAN=4011> was detected.(2018-9-11 20:43:48)
*Sep 11 20:48:10: %NFPP_DHCPV6_GUARD-4-DOS_DETECTED: Host<IP=N/A,MAC=00e0.705d.1ef0,port=Fa0/11,VLAN=4011> was detected.(2018-9-11 20:44:4)
*Sep 11 20:48:40: %NFPP_DHCPV6_GUARD-4-DOS_DETECTED: Host<IP=N/A,MAC=e0d5.5e57.7540,port=Fa0/11,VLAN=4011> was detected.(2018-9-11 20:44:12)
*Sep 11 20:49:10: %NFPP_DHCPV6_GUARD-4-DOS_DETECTED: Host<IP=N/A,MAC=9c5c.8e75.c986,port=Fa0/11,VLAN=4011> was detected.(2018-9-11 20:44:53)
*Sep 11 20:49:40: %NFPP_DHCPV6_GUARD-4-DOS_DETECTED: Host<IP=N/A,MAC=507b.9d65.d915,port=Fa0/11,VLAN=4011> was detected.(2018-9-11 20:44:53)
*Sep 11 20:50:10: %NFPP_DHCPV6_GUARD-4-DOS_DETECTED: Host<IP=N/A,MAC=3497.f6b7.d88e,port=Fa0/11,VLAN=4011> was detected.(2018-9-11 20:44:56)
*Sep 11 20:50:40: %NFPP_DHCPV6_GUARD-4-DOS_DETECTED: Host<IP=N/A,MAC=1c1b.0d06.b23d,port=Fa0/11,VLAN=4011> was detected.(2018-9-11 20:45:15)
*Sep 11 20:51:10: %NFPP_DHCPV6_GUARD-4-PORT_ATTACKED: DHCPv6 DoS attack was detected on port Fa0/11.(2018-9-11 20:45:15)
*Sep 11 20:51:40: %NFPP_DHCPV6_GUARD-4-DOS_DETECTED: Host<IP=N/A,MAC=a81e.840c.0ba8,port=Fa0/11,VLAN=4011> was detected.(2018-9-11 20:45:19)
查看交换机nfpp dhcpv6-gurad 功能是否打开:
S08CT#show nfpp dhcpv6-guard summary
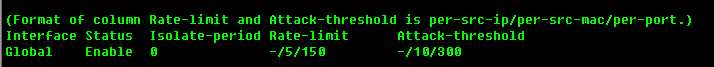
status是enable的,也就是说是开启的
在接入端口上开启
nfpp dhcpv6-guard enable
配置nfpp
进入config模式
进入nfpp模式
S08CT(config-nfpp)#dhcpv6-guard rate-limit per-port 5
每个端口每秒超过5个dhcp包就丢弃
标签:show 时区 jin 服务 serve 数据 ntp服务 check timezone
原文地址:https://www.cnblogs.com/sparrow32/p/9630538.html