标签:ptr 地址 tor seve 服务器 ndk 不能 验证 nslookup
D就是区域
N就是名字
S就是服务
1.缓存域名服务器
帮你去找域名解析,本身并不能解析
去公网找真正的域名服务器,去要域名解析,要回来以后,放到自己的缓存里它在给你,你在请求同样的数据它就有了2.主域名解析服务器
也就是他自己维护一个域名的解析记录本3.从域名解析服务器(主的备份)
4.智能解析服务器
1.正向解析记录
域名===>IP
(1)A记录就是把域名变成IP
(2)Cname别名解析2.反向解析记录
IP===>域名
(1)PTR反向解析
1.递归查询
不需要求助别人的服务叫做递归查询2.迭代查询
需求求助别人的服务叫做迭代查询
全世界13给点(.)域名服务器,那么www.baidu.com这个域名里也有点这个东西,因此LDNS先去求助点域名服务器
DNS端口号:53
rpm -qa | grep -w bind bind-chroot ===>需要安装2个软件包
vim /etc/named.conf ===>DNS主配置文件(安装完软件包就有主配置文件)
options {listen-on port 53 { 192.168.200.67; };// listen-on-v6 port 53 { ::1; };directory "/var/named";dump-file "/var/named/data/cache_dump.db";statistics-file "/var/named/data/named_stats.txt";memstatistics-file "/var/named/data/named_mem_stats.txt";allow-query { any; };recursion yes;dnssec-enable no;dnssec-validation no;// dnssec-lookaside auto;/* Path to ISC DLV key */bindkeys-file "/etc/named.iscdlv.key";managed-keys-directory "/var/named/dynamic";};logging {channel default_debug {file "data/named.run";severity dynamic;};};zone "." IN {type hint;file "named.ca";};include "/etc/named.rfc1912.zones";include "/etc/named.root.key";options {listen-on port 53 { 192.168.200.67; }; ===>监听IP地址listen-on-v6 port 53 { ::1; }; ===>注释掉,在DNS配置文件//代表注释directory "/var/named"; ===>DNS目录位置dump-file "/var/named/data/cache_dump.db"; ===>DNS数据文件位置memstatistics-file "/var/named/data/named_mem_stats.txt"; ===>DNS缓存数据文件位置allow-query { any; }; ===>允许连接我的IP地址范围,any代表允许所有人forwarders { 202.106.0.20; }; ===>告诉去找哪个域名,可写可不写recursion yes; ===>是否迭代查询dnssec-enable no; ===>改成NOdnssec-validation no; ===>改成NOdnssec-lookaside auto; ===>一些验证,注释掉zone "." IN {type hint;file "named.ca"; ===>代表去点域名找named-checkconf /etc/named.conf ===>核对不提示任何信息代表成功
etc/init.d/named start ===>启动DNS服务
netstat -antup | grep 53 ===>查询端口是否开启
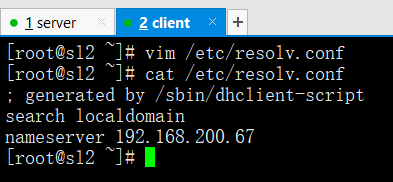
vim /etc/resolv.conf
nameserver 192.168.200.67 ===>临时修改服务器配置跟DNS主配置文件IP一样,重启网卡自然被原先的文件覆盖
ping www.baidu.com ===>ping一下检查服务是否正确,卡是正常,因为是在找点域名
rpm -qa | grep -w bind bind-chroot ===>需要安装2个软件包
vim /etc/named.conf ===>DNS主配置文件===>DNS主配置文件(安装完软件包就有主配置文件)
options {listen-on port 53 { 192.168.200.67; };// listen-on-v6 port 53 { ::1; };directory "/var/named";dump-file "/var/named/data/cache_dump.db";statistics-file "/var/named/data/named_stats.txt";memstatistics-file "/var/named/data/named_mem_stats.txt";allow-query { any; };forwarders { 202.106.0.20; };recursion yes;// dnssec-enable no;// dnssec-validation no;// dnssec-lookaside auto;/* Path to ISC DLV key */bindkeys-file "/etc/named.iscdlv.key";managed-keys-directory "/var/named/dynamic";};logging {channel default_debug {file "data/named.run";severity dynamic;};};zone "yunjisuan.com" IN {type master;file "yunjisuan.com.zone";};zone "." IN {type hint;file "named.ca";};include "/etc/named.rfc1912.zones";include "/etc/named.root.key";配置详解listen-on port 53 { 192.168.200.67; }; ===>监听IP地址listen-on-v6 port 53 { ::1; }; ===>注释掉,在DNS配置文件//代表注释directory "/var/named"; ===>DNS目录位置dump-file "/var/named/data/cache_dump.db"; ===>DNS数据文件位置memstatistics-file "/var/named/data/named_mem_stats.txt"; ===>DNS缓存数据文件位置allow-query { any; }; ===>允许连接我的IP地址范围,any代表允许所有人forwarders { 202.106.0.20; }; ===>告诉去找哪个域名recursion yes; ===>是否迭代查询dnssec-enable no; ===>注释掉dnssec-validation no; ===>注释掉dnssec-lookaside auto; ===>注释掉zone "yunjisuan.com" IN { ===>代表区域文件,正向解析zone "." IN { ===>代表去点域名找cd /var/named/named.empty ===>记录本文件
cp -p named.empty yunjisuan.com.zone ===>完全复制记录本文件各项属性
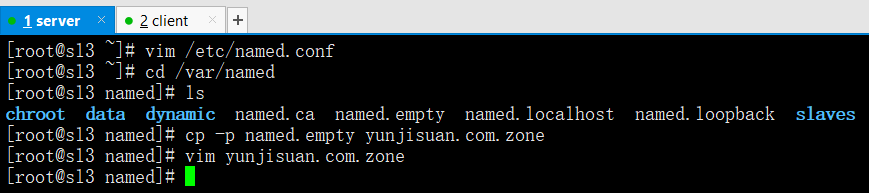
$TTL 3H@ IN SOA yunjisuan.com. root.ns1.yunjisuan.com. (20181022 ; serial1D ; refresh1H ; retry1W ; expire3H ) ; minimumNS ns1.yunjisuan.com.ns1 A 192.168.200.67www A 192.168.200.2news A 192.168.200.1bbs CNAME news* A 192.168.200.68配置详解$TTL 3H ===>时间周期yunjisuan.com. root.ns1.yunjisuan.com. ===>解析文件是以点结尾20181022 ; serial ===>当前日期,也是比对日期NS ns1.yunjisuan.com. ===>解析服务器的位置ns1 A 192.168.200.66 ===>当前解析记录IPbbs CNAME news ===>别名记录,bbs跟news是一个IP* A 192.168.200.68 ===>其他的所有找输入的IP地址named-checkzone yunjisuan.com yunjisuan.com.zone ===>核对提示OK代表成功
/etc/init.d/named start ===>启动DNS服务

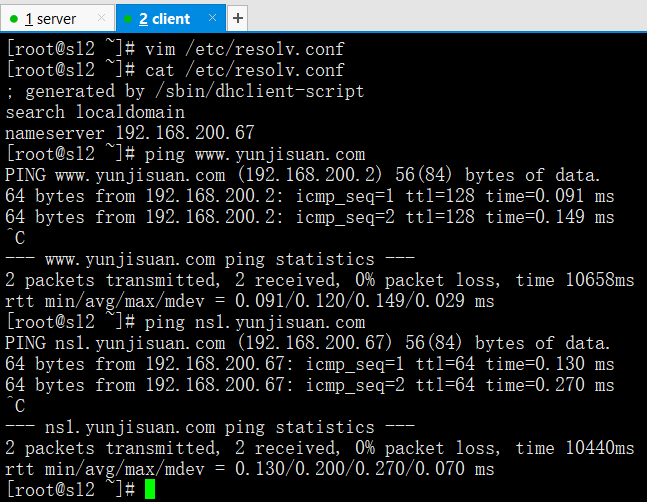
vim /etc/resolv.conf
nameserver 192.168.200.67 ===>临时修改服务器配置跟DNS主配置文件IP一样,重启网卡自然被原先的文件覆盖
ping www.yunjisuan.com ===>ping一下检查服务是否正确,卡是正常,因为是在找点域名
ping ns1.yunjisuan.com ===>ping一下检查服务是否正确,卡是正常,
rpm -qa | grep -w bind bind-chroot ===>需要安装2个软件包
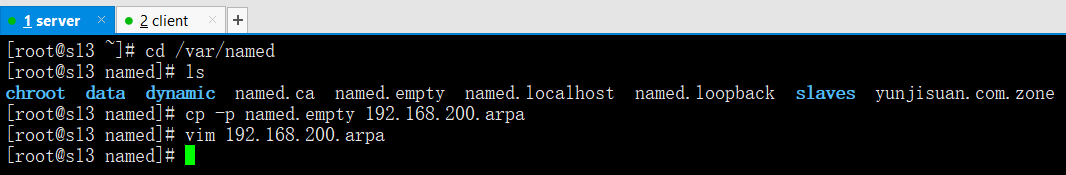
vim /etc/named.conf ===>DNS主配置文件===>DNS主配置文件(安装完软件包就有主配置文件)
options {listen-on port 53 { 192.168.200.67; };// listen-on-v6 port 53 { ::1; };directory "/var/named";dump-file "/var/named/data/cache_dump.db";statistics-file "/var/named/data/named_stats.txt";memstatistics-file "/var/named/data/named_mem_stats.txt";allow-query { any; };forwarders { 202.106.0.20; };recursion yes;// dnssec-enable no;// dnssec-validation no;// dnssec-lookaside auto;/* Path to ISC DLV key */bindkeys-file "/etc/named.iscdlv.key";managed-keys-directory "/var/named/dynamic";};logging {channel default_debug {file "data/named.run";severity dynamic;};};zone "202.168.192.inaddr.arpa" IN {type master;file "192.168.200.arpa";};zone "." IN {type hint;file "named.ca";};include "/etc/named.rfc1912.zones";include "/etc/named.root.key";配置详解listen-on port 53 { 192.168.200.67; }; ===>监听IP地址listen-on-v6 port 53 { ::1; }; ===>注释掉,在DNS配置文件//代表注释directory "/var/named"; ===>DNS目录位置dump-file "/var/named/data/cache_dump.db"; ===>DNS数据文件位置memstatistics-file "/var/named/data/named_mem_stats.txt"; ===>DNS缓存数据文件位置allow-query { any; }; ===>允许连接我的IP地址范围,any代表允许所有人forwarders { 202.106.0.20; }; ===>告诉去找哪个域名recursion yes; ===>是否迭代查询dnssec-enable no; ===>注释掉dnssec-validation no; ===>注释掉dnssec-lookaside auto; ===>注释掉zone "200.168.192.inaddr.arpa" IN { ===>代表区域文件,反向解析zone "." IN { ===>代表去点域名找cd /var/named/named.empty ===>记录本文件
cp -p named.empty 192.168.200.arpa ===>完全复制记录本文件各项属性
$TTL 3H@ IN SOA yunjisuan.com. root.ns1.yunjisuan.com. (20181022 ; serial1D ; refresh1H ; retry1W ; expire3H ) ; minimumNS ns1.yunjisuan.com.2 PTR www.yunjisuan.com.67 PTR ns1.yunjisuan.com.配置详解$TTL 3H ===>时间周期yunjisuan.com. root.ns1.yunjisuan.com. ( ===>解析文件是以点结尾20181022 ; serial ===>当前日期,也是比对日期NS ns1.yunjisuan.com. ===>解析服务器的位置PTR www.yunjisuan.com. ===>已知IP反推域名,PTR反向解析yum -y install bind-utils ===>安装完软件包就有nslookup命令
which nslookup
vim /etc/resolv.conf
nameserver 192.168.200.67 ===>临时修改服务器配置跟DNS主配置文件IP一样,重启网卡自然被原先的文件覆盖
nslookup www.yunjisuan.com ===>反向解析为了追踪黑客位置
nslookup ns1.yunjisuan.com
nslookup 192.168.200.67
标签:ptr 地址 tor seve 服务器 ndk 不能 验证 nslookup
原文地址:https://www.cnblogs.com/666boke/p/9946104.html