标签:mail end out example register intranet including form database
Explore online vulnerability for servers and IoT devices : https://www.shodan.com
get dumped leaked information : https://www.pastebin.com
Text and source code leak: https://github.com
online Swiss Army knife tools: https://www.dnsstuff.com
also use the url: http://searchdns.netcraft.com you can find target website information
whois domain-name.com ,because every domain name is registered in a public WHOIS database , depending on the database that is queried.it will reveal a lot of juicy information . including name ,phone number ,Emails address Physical DNS and so on .
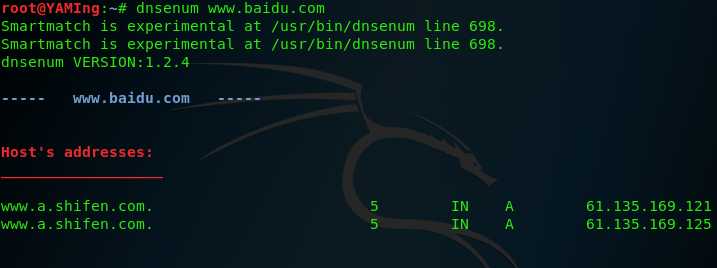
dnsenum domain-name.com ,DOMAIN name System is a database that resolves domain name ,wen can use it gather information such as identigy new domain names or subdomians associated target .and find services (for example FTP ,SSL ,Telnet)
these commands may userful
denenum domain_name.com
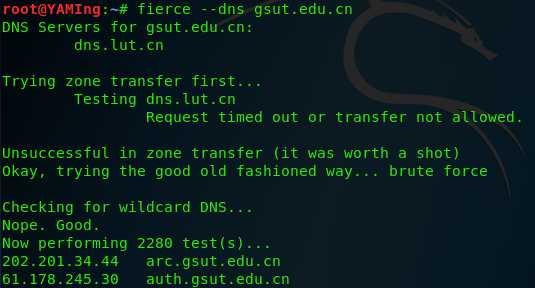
fierce -dns domain_name.com
dnsrecon -w -d domain_name.com -t axfr (-w it means deep , -t stand for type axfr it‘s all DNS server )
Gatering email address :theharvester script is a Python tool/script that can gather the target email address
Active information gathering services enumeration ,a lot of wegit can be used .scan ,advanced_ip_scanner nmap
the nmap command :
nmap -sn [ip ]
netdiscover -r [ip]
how to identifying opne ports/services ,we usually use ping ,but is not in here : we can use TCP scan -interanet
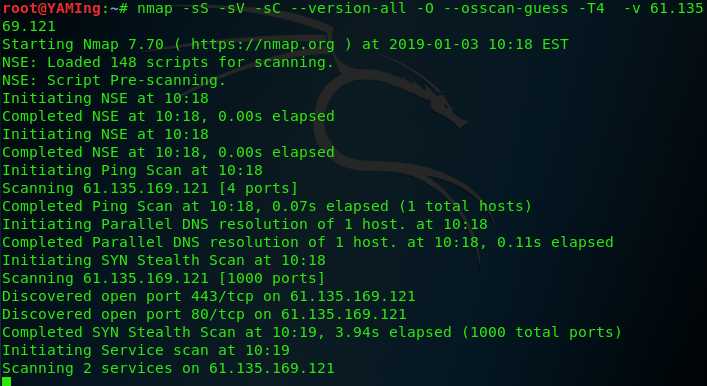
nmap -sS -sV -sC --version-all -o --osscan-guess -T4 --reason --open -p--Pn -v [ip]
UDP scan -intranet : nmap -sU --top-ports 1000 -Pn -v [ip]
TCP scan -from the internet: nmap -sS -T2 --top--ports 1000 -Pn -v [ip]
nmap -sU --top-ports 100 -Pn -v [ip]
Server probing and enumeration to find 21 port server FTP we can use command
nmap -sV -p 21 -Pn -T5 --host-timeout 15ms --script=ftp* -v [ip]
ofcourse the Credential burte force: hydra -t 10 -V -f -L [users dic file path ] -P [passwords dic file path] ftp://[ip]
and other ports also user the way .
tomorrow see
标签:mail end out example register intranet including form database
原文地址:https://www.cnblogs.com/xinxianquan/p/10217561.html