标签:constrain ued red enable 启动服务 ons start ttl 自签名证书
1.TSL链路通信TLS: Transport Layer Security 安全传输协议,在应用层 传输层之间主要应用https 协议,ftps 协议等
https大体流程
客户端A 服务端B
A ————》 (连接请求 ) B
A《———— (发送CA私钥加密过B的公钥,也就是安全证书)B
A (用CA公钥解开证书得到B的公钥)
A (生成对称秘钥key,并用B的公钥加密)
A ————》(加密的秘钥key) B
B (B用自己的私钥解密得到对称私钥key)
A B后续通讯使用对称私钥加密通讯
搭建私有CA,用于自签名
[root@centos7 ~]#(umask 066; openssl genrsa -out /etc/pki/CA/private/cakey.pem 2048)
Generating RSA private key, 2048 bit long modulus
.................................................................................................+++
..........+++
e is 65537 (0x10001)注意生成文件必须与/etc/pki/tls/openssl.cnf配置文件定义一致
dir = /etc/pki/CA # Where everything is kept
private_key = $dir/private/cakey.pem# The private key
而且生成文件权限为600
[root@centos7 ~]#openssl req -new -x509 -key /etc/pki/CA/private/cakey.pem -days 7200 -out /etc/pki/CA/cacert.pem
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter ‘.‘, the field will be left blank.
Country Name (2 letter code) [XX]:cn
State or Province Name (full name) []:gd
Locality Name (eg, city) [Default City]:gz
Organization Name (eg, company) [Default Company Ltd]:nvliu
Organizational Unit Name (eg, section) []:dcrfan
Common Name (eg, your name or your server‘s hostname) []:centos7
Email Address []:注意生成文件必须与/etc/pki/tls/openssl.cnf配置文件定义一致
certificate = $dir/cacert.pem # The CA certificate
定义一些国家省份信息
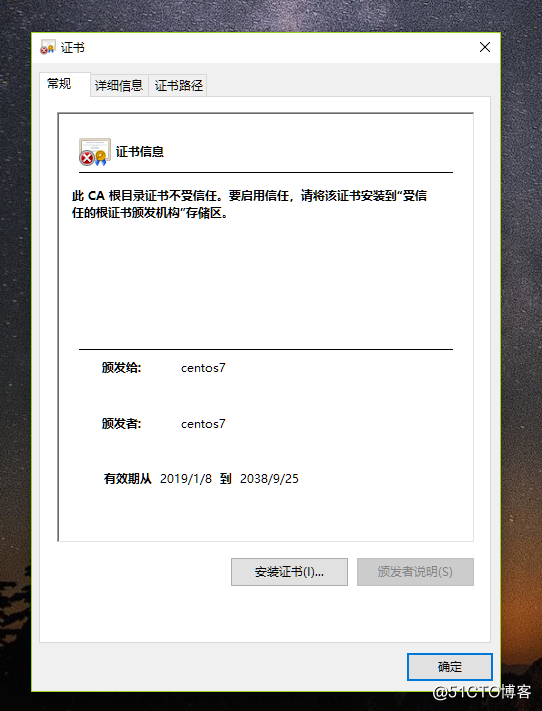
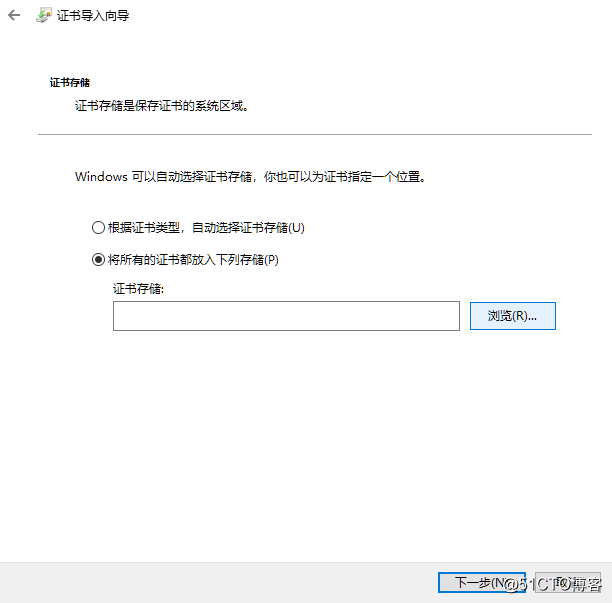
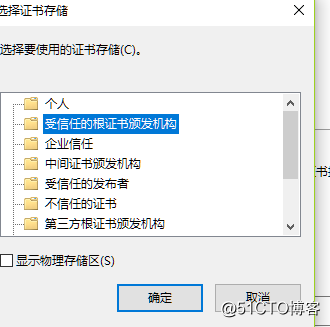
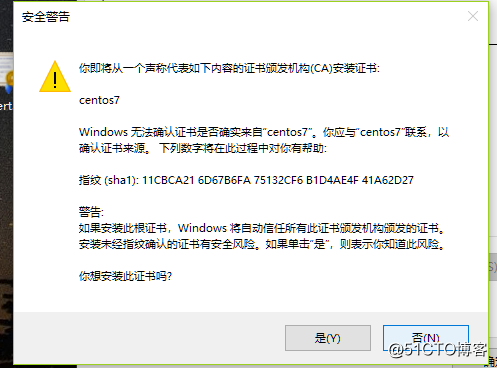
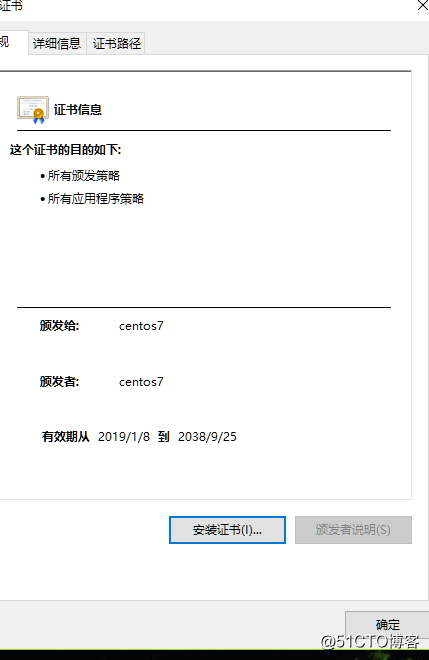
[root@localhost ~]# (umask 066; openssl genrsa -out /data/app.key 2048)
Generating RSA private key, 2048 bit long modulus
............................................+++
........................+++
e is 65537 (0x10001)而且生成文件权限为600
[root@localhost ~]# (umask 066; openssl genrsa -out /data/app.key 2048)
Generating RSA private key, 2048 bit long modulus
............................................+++
........................+++
e is 65537 (0x10001)
[root@localhost ~]# openssl req -new -key /data/app.key -out /data/app.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter ‘.‘, the field will be left blank.
Country Name (2 letter code) [XX]:cn
State or Province Name (full name) []:gd
Locality Name (eg, city) [Default City]:gz
Organization Name (eg, company) [Default Company Ltd]:nvliu
Organizational Unit Name (eg, section) []:dcrfan1
Common Name (eg, your name or your server‘s hostname) []:centos7.1
Email Address []:
Please enter the following ‘extra‘ attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:[root@centos7 ~]#echo 01 > /etc/pki/CA/serial
[root@centos7 ~]#touch /etc/pki/CA/index.txt这两个位置在/etc/pki/tls/openssl.cnf 均有定义
database = $dir/index.txt # database index file.
serial = $dir/serial # The current serial number
[root@centos7 ~]#openssl ca -in /data/app.csr -out /etc/pki/CA/certs/app.crt -days 160
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Jan 8 11:23:04 2019 GMT
Not After : Jun 17 11:23:04 2019 GMT
Subject:
countryName = cn
stateOrProvinceName = gd
organizationName = nvliu
organizationalUnitName = dcrfan1
commonName = centos7.1
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
2C:54:95:C8:30:80:97:89:7E:4A:40:50:F9:64:CB:2F:2E:D9:97:EA
X509v3 Authority Key Identifier:
keyid:48:8F:FB:78:84:50:F0:B0:AB:6F:2C:10:B6:03:9F:21:03:03:20:70
Certificate is to be certified until Jun 17 11:23:04 2019 GMT (160 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated注意生成文件必须与/etc/pki/tls/openssl.cnf配置文件定义一致
certs = $dir/certs # Where the issued certs are kept
实验分别准备8台实验机器,
192.168.0.108 远程访问客服端
192.168.0.109 缓存dns服务器
192.168.0.112 dcrfan.com dns主服务器
192.168.0.113 dcrfan.com dns 从服务器
192.168.0.114 com dns服务器
192.168.0.115 根dns 服务器
192.168.0.116 web 服务器
192.168.0.117 web 服务器
options {
//listen-on port 53 { 127.0.0.1; }; #注释该行,让本服务器ip监听53端口
allow-query { 192.168.0.0/24; }; # 修改改行,允许该网段的ip使用dns服务器
allow-transfer { 192.168.0.113; }; #新增改行,只允许从dns服务器拉取数据
};zone "dcrfan.com" IN {
type master;#定义类型为主dns服务器
file "dcrfan.com.zone";#定义该域数据文件位置
};@ IN SOA dns1.dcrfan.com. admin.dcrfan.com. (
0
1D
1H
1W
3H )
NS dns1
NS dns2
dns1 A 192.168.0.112
dns2 A 192.168.0.113
srv A 192.168.0.116
srv A 192.168.0.117
www CNAME srv[root@centos6 ~]# dig www.dcrfan.com @192.168.0.112
; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.62.rc1.el6 <<>> www.dcrfan.com @192.168.0.112
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 60001
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 2, ADDITIONAL: 2
;; QUESTION SECTION:
;www.dcrfan.com. IN A
;; ANSWER SECTION:
www.dcrfan.com. 86400 IN CNAME srv.dcrfan.com.
srv.dcrfan.com. 86400 IN A 192.168.0.117
srv.dcrfan.com. 86400 IN A 192.168.0.116
;; AUTHORITY SECTION:
dcrfan.com. 86400 IN NS dns2.dcrfan.com.
dcrfan.com. 86400 IN NS dns1.dcrfan.com.
;; ADDITIONAL SECTION:
dns1.dcrfan.com. 86400 IN A 192.168.0.112
dns2.dcrfan.com. 86400 IN A 192.168.0.113
;; Query time: 1 msec
;; SERVER: 192.168.0.112#53(192.168.0.112)
;; WHEN: Thu Jan 10 16:09:29 2019
;; MSG SIZE rcvd: 152options {
//listen-on port 53 { 127.0.0.1; }; #注释该行,让本服务器ip监听53端口
allow-query { 192.168.0.0/24; }; # 修改改行,允许该网段的ip使用dns服务器
allow-transfer { none; }; #新增改行,不允许任何dns服务器拉取数据
};zone "dcrfan.com" IN {
type slave;#定义类型是从dns服务器
masters { 192.168.0.112; }; #指定主dns服务器
file "slaves/dcrfan.com.slave.zone"; #dns记录数据存放位置
};[root@localhost ~]# ll /var/named/slaves/dcrfan.com.slave.zone
-rw-r--r--. 1 named named 371 Jan 10 16:38 /var/named/slaves/dcrfan.com.slave.zone[root@centos6 ~]# dig www.dcrfan.com @192.168.0.113
; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.62.rc1.el6 <<>> www.dcrfan.com @192.168.0.113
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 38752
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 2, ADDITIONAL: 2
;; QUESTION SECTION:
;www.dcrfan.com. IN A
;; ANSWER SECTION:
www.dcrfan.com. 86400 IN CNAME srv.dcrfan.com.
srv.dcrfan.com. 86400 IN A 192.168.0.117
srv.dcrfan.com. 86400 IN A 192.168.0.116
;; AUTHORITY SECTION:
dcrfan.com. 86400 IN NS dns2.dcrfan.com.
dcrfan.com. 86400 IN NS dns1.dcrfan.com.
;; ADDITIONAL SECTION:
dns1.dcrfan.com. 86400 IN A 192.168.0.112
dns2.dcrfan.com. 86400 IN A 192.168.0.113
;; Query time: 4 msec
;; SERVER: 192.168.0.113#53(192.168.0.113)
;; WHEN: Thu Jan 10 16:41:18 2019
;; MSG SIZE rcvd: 152options {
//listen-on port 53 { 127.0.0.1; }; #注释该行,让本服务器ip监听53端口
//allow-query { 192.168.0.0/24; }; # 注释改行,允许所有ip使用dns服务器
dnssec-enable no;
dnssec-validation no; #都修改为no
};zone "dcrfan.com" IN {
type forward;
forward first;
forwarders { 192.168.0.112; 192.168.0.113;};
};[root@centos6 ~]# dig www.dcrfan.com @192.168.0.114
; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.62.rc1.el6 <<>> www.dcrfan.com @192.168.0.114
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 26492
;; flags: qr rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 2, ADDITIONAL: 2
;; QUESTION SECTION:
;www.dcrfan.com. IN A
;; ANSWER SECTION:
www.dcrfan.com. 86400 IN CNAME srv.dcrfan.com.
srv.dcrfan.com. 86400 IN A 192.168.0.117
srv.dcrfan.com. 86400 IN A 192.168.0.116
;; AUTHORITY SECTION:
dcrfan.com. 86400 IN NS dns2.dcrfan.com.
dcrfan.com. 86400 IN NS dns1.dcrfan.com.
;; ADDITIONAL SECTION:
dns1.dcrfan.com. 86400 IN A 192.168.0.112
dns2.dcrfan.com. 86400 IN A 192.168.0.113
;; Query time: 14 msec
;; SERVER: 192.168.0.114#53(192.168.0.114)
;; WHEN: Thu Jan 10 17:18:21 2019
;; MSG SIZE rcvd: 152options {
//listen-on port 53 { 127.0.0.1; }; #注释该行,让本服务器ip监听53端口
//allow-query { 192.168.0.0/24; }; # 注释改行,允许所有ip使用dns服务器
dnssec-enable no;
dnssec-validation no; #都修改为no
};
zone "." IN { #删除这个根zone
type hint;
file "named.ca";
};zone "." IN {
type master;#定义类型为主dns服务器
file "root.zone";#定义该域数据文件位置
};@ IN SOA dns1. admin. (
0
1D
1H
1W
3H )
NS dns1
com NS dns2 #指派com域到192.168.0.114管理
dns1 A 192.168.0.115
dns2 A 192.168.0.114[root@centos6 ~]# dig www.dcrfan.com @192.168.0.115
; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.62.rc1.el6 <<>> www.dcrfan.com @192.168.0.115
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 51669
;; flags: qr rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 2, ADDITIONAL: 2
;; QUESTION SECTION:
;www.dcrfan.com. IN A
;; ANSWER SECTION:
www.dcrfan.com. 84281 IN CNAME srv.dcrfan.com.
srv.dcrfan.com. 86400 IN A 192.168.0.117
srv.dcrfan.com. 86400 IN A 192.168.0.116
;; AUTHORITY SECTION:
dcrfan.com. 84281 IN NS dns2.dcrfan.com.
dcrfan.com. 84281 IN NS dns1.dcrfan.com.
;; ADDITIONAL SECTION:
dns1.dcrfan.com. 84281 IN A 192.168.0.112
dns2.dcrfan.com. 84281 IN A 192.168.0.113
;; Query time: 14 msec
;; SERVER: 192.168.0.115#53(192.168.0.115)
;; WHEN: Thu Jan 10 17:53:40 2019
;; MSG SIZE rcvd: 152
`options {
//listen-on port 53 { 127.0.0.1; }; #注释该行,让本服务器ip监听53端口
//allow-query { 192.168.0.0/24; }; # 注释改行,允许所有ip使用dns服务器
dnssec-enable no;
dnssec-validation no; #都修改为no
};. 518400 IN NS a.root-servers.net.
a.root-servers.net. 3600000 IN A 192.168.0.115[root@centos6 ~]# dig www.dcrfan.com @192.168.0.109
; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.62.rc1.el6 <<>> www.dcrfan.com @192.168.0.109
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 41909
;; flags: qr rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 2, ADDITIONAL: 2
;; QUESTION SECTION:
;www.dcrfan.com. IN A
;; ANSWER SECTION:
www.dcrfan.com. 83143 IN CNAME srv.dcrfan.com.
srv.dcrfan.com. 86400 IN A 192.168.0.116
srv.dcrfan.com. 86400 IN A 192.168.0.117
;; AUTHORITY SECTION:
dcrfan.com. 83143 IN NS dns1.dcrfan.com.
dcrfan.com. 83143 IN NS dns2.dcrfan.com.
;; ADDITIONAL SECTION:
dns2.dcrfan.com. 83143 IN A 192.168.0.113
dns1.dcrfan.com. 83143 IN A 192.168.0.112
;; Query time: 16 msec
;; SERVER: 192.168.0.109#53(192.168.0.109)
;; WHEN: Thu Jan 10 18:12:37 2019
;; MSG SIZE rcvd: 152[root@centos6 ~]# curl www.dcrfan.com
dcrfan2
[root@centos6 ~]# curl www.dcrfan.com
dcrfan1[root@centos6 ~]# curl www.dcrfan.com
dcrfan2
[root@centos6 ~]# curl www.dcrfan.com
dcrfan2
[root@centos6 ~]# curl www.dcrfan.com
dcrfan1标签:constrain ued red enable 启动服务 ons start ttl 自签名证书
原文地址:http://blog.51cto.com/6289984/2342154