标签:rem nbsp record tar lis back eterm discus eva
1、theree -way handshake
A TCP SYN packet is sent from the device that wishes to establish a connection with a port of the device the it derires to connect with ,if the service assoicated with the receiving port accepts the connection , it will replay to the requesting system with a TCP packet that has both the SYN and ACKbits activated ,the connection is established only when the requesting system responds with the a TCP ACK response ,this therr-step process establish a TCP session between the two system. all of the TCP port scanning techniques will perform some varatio of this process to identify live service on the remote hosts.
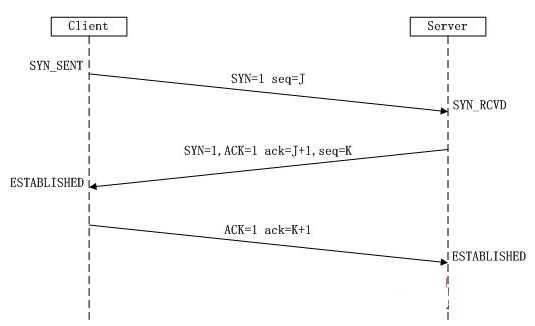
we know the Connect scanning is used to establish a full TCP connection for each port that is scanned ,Alternatively ,Stealth scanning doesn‘t esatblish a full connection ,it only refered to as SYN scanning or half-open scanning , for each port that is scanned , a single SYN packet is sent to the destination port ,and all ports that replay with a SYN +ACK packet are assumed to be running live service ,since no final ACK is sent from the initiating system ,the connection is left half-open ,this is referred to as stealth scanning because logging solutions that only recode established connection will not record any evidence of the scan .
2、 Zombie scanning
when we know the scanning principle , let‘s discussed the final method of TCP scanning , the zombie scanning is to map ope ports on the remote the system without producing any evidence that you have interavted with the system ,
then how to do carry out the process of zombie scanning : as follow
step one : identify a remote system for you zombie ,this system should have the following characteristics
step two : Send a SYN+ACK packet to this zombie host and record the initial IPID values
step three: send a SYN packet with a spoofed source ip address of the zombie system to the scan target system
setp four : depending the status of the port the scan target ,one of the following two things will happen:
step five : send another SYN+ACK packet to the zombie host ,and evaluate the final IPID value of the return RST resopnse , if this value has incermente by ONE ,then the port on the scan target is closed ,and if the value the incermented by TWO , then the port on the scan target is open .
.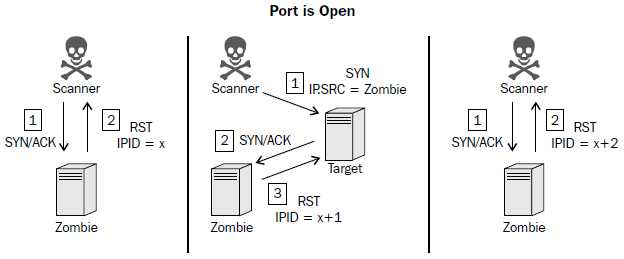
To perform a zombie scan, an initial SYN+ACK request should be sent to the zombie system to determine the current IPID value in the returned RST packet. Then, a spoofed SYN packet is sent to the scan target with a source IP address of the zombie system. If the port is open, the scan target will send a SYN+ACK response back to the zombie. Since the zombie did not actually send the initial SYN request, it will interpret the SYN+ACK response as unsolicited and send an RST packet back to the target, thereby incrementing its IPID by one. Finally, another SYN+ACK packet should be sent to the zombie, which will return an RST packet and increment the IPID one more
time. An IPID that has incremented by two from the initial response is indicative of the fact that all of these events have transpired and that the destination port on the scanned system is open. Alternatively, if the port on the scan target is closed, a different series of events will transpire, which will only cause the final RST response IPID value to increment by one.
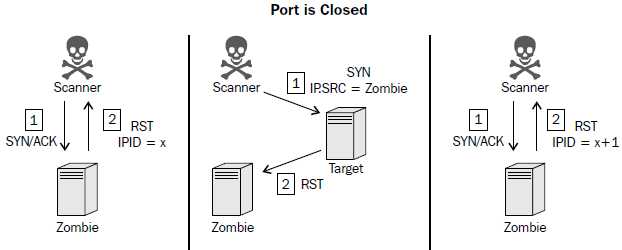
If the destination port on the scan target is closed, an RST packet will be sent to the zombie system in response to the initially spoofed SYN packet. Since the RST packet solicits no response, the IPID value of the zombie system will not be incremented. As a result, the final RST packet returned to the scanning system in response to the SYN+ACK packet will have the IPID incremented by only one. This process can be performed for each port that is to be scanned, and it can be used to map open ports on a remote system without leaving any evidence that a scan was performed by the scanning system.
标签:rem nbsp record tar lis back eterm discus eva
原文地址:https://www.cnblogs.com/xinxianquan/p/10300499.html