标签:star ica usr efault python2 print message version ==
#!/usr/bin/python3
# -*- coding: utf-8 -*-
"""
@Author: r0cky
@Time: 2019/9/2-17:35
"""
import socket
import sys
passwds = ['redis','root','oracle','password','p@ssw0rd','abc123!','123456','admin','abc123']
def check(ip, port, timeout):
try:
socket.setdefaulttimeout(timeout)
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
print u"[INFO] connecting " + ip + u":" + port
s.connect((ip, int(port)))
print u"[INFO] connected "+ip+u":"+port+u" hacking..."
s.send("INFO\r\n")
result = s.recv(1024)
if "redis_version" in result:
return u"[HACKED] 未授权访问"
elif "Authentication" in result:
for passwd in passwds:
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((ip, int(port)))
s.send("AUTH %s\r\n" %(passwd))
# print u"[HACKING] hacking to passwd --> "+passwd
result = s.recv(1024)
if 'OK' in result:
return u"[HACKED] 存在弱口令,密码:%s" % (passwd)
s.close()
except Exception, e:
if len(e.message) != 0:
print u"[ERROR] "+e.message
return u"[INFO] 目标Redis服务,暂不存在未授权和弱口令漏洞!"
if __name__ == '__main__':
ip=sys.argv[1]
# default Port
port="6379"
if len(sys.argv) >= 3:
port=sys.argv[2]
result = check(ip,port, timeout=10)
print result
if "HACKED" in result:
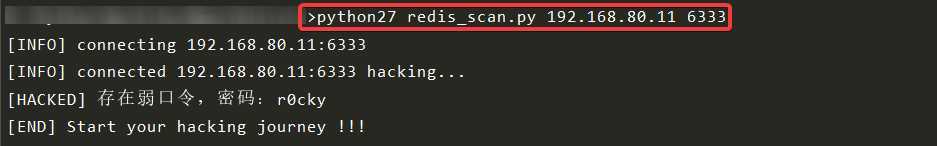
print u"[END] Start your hacking journey !!!"python27 redis_scan.py [目标IP] [指定端口](可以不写)
不写指定端口默认为 6379 端口
标签:star ica usr efault python2 print message version ==
原文地址:https://www.cnblogs.com/r0ckysec/p/11448225.html