标签:配置文件 一个 查看 无法访问 may ade host roots named
原理:要访问www.magedu.com网址,先在本地的缓存DNS服务器寻找,如果有,就可以访问,如果没有,根将DNS服务器的缓存放入到北京,将北京作为一个转发(作为期望的DNS转发服务器),上海和重庆直接指向北京寻找答案,节约了广域上的网络带宽。
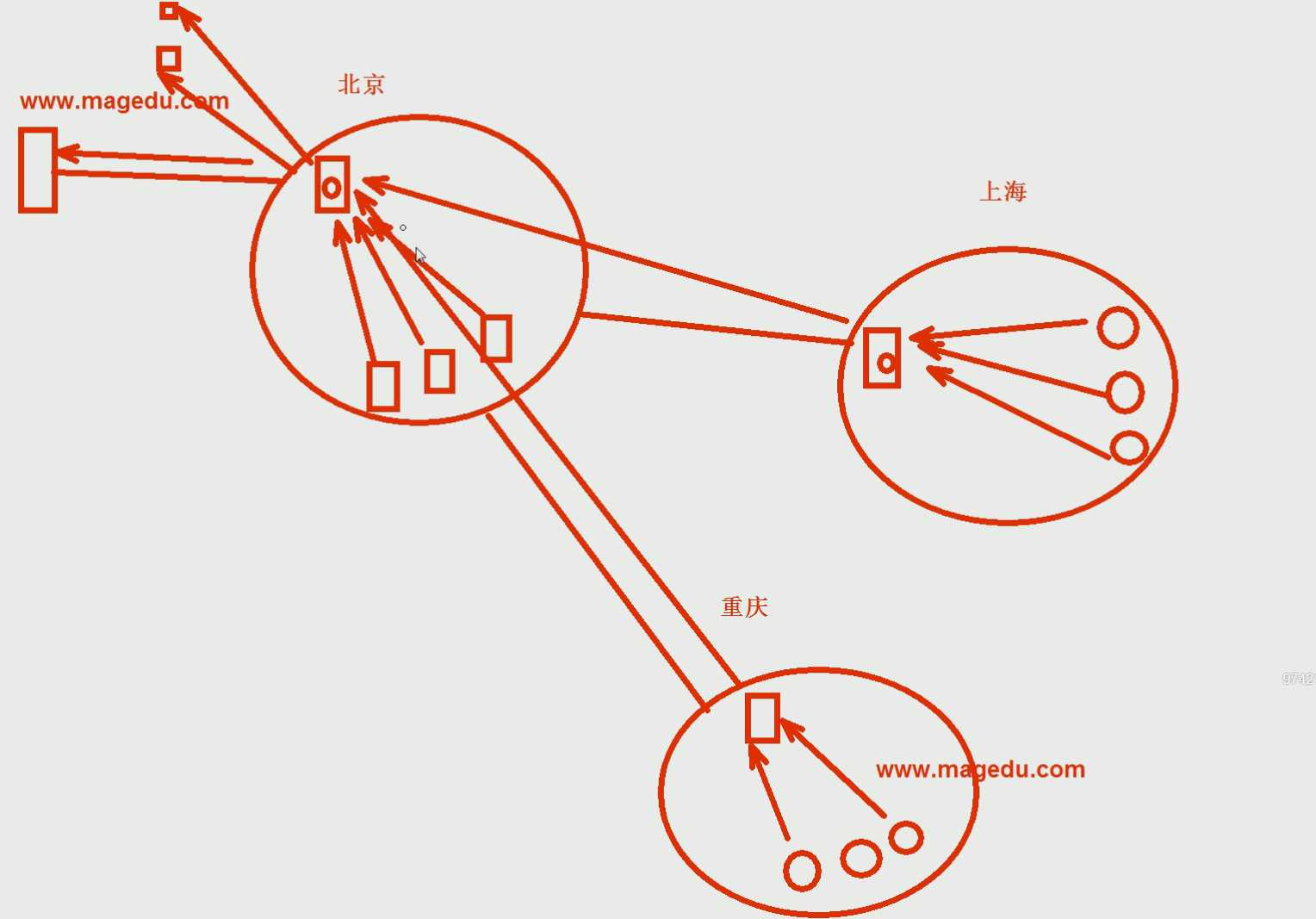
only用法:客户端发起请求在A服务器上找,A服务器转发到B(103IP)的服务器上,B服务器返回最终的结果,如果B服务器没有不去询问根。
创建一个转发服务器B(192.168.34.103),将/etc/named.rfc1912.zones配置文件进行修改:
[root@centos7-1~]#vim /etc/named.rfc1912.zones
zone "wang.com" {
type master;
file "wang.com.zone";
};
在/var/named/目录下创建一个wang.com.zone配置文件:
vim /var/named/www.wang.com.zone $TTL 1D @ IN SOA dns1 admin ( 1 1H 1M 1D 3H ) NS dns1 dns1 A 192.168.34.102 www A 6.6.6.6
注意将 wang.com.zone配置文件的所属组改为named,权限改为640
[root@centos7-1named]#ll total 32 -rw-r--r-- 1 root root 230 Nov 6 22:53 192.168.34.zone -rw-r----- 1 root named 296 Nov 7 15:35 baidu.com.zone drwxrwx--- 2 named named 23 Oct 31 2018 data drwxrwx--- 2 named named 31 Nov 7 16:21 dynamic -rw-r----- 1 root named 2281 May 22 2017 named.ca -rw-r----- 1 root named 152 Dec 15 2009 named.empty -rw-r----- 1 root named 152 Jun 21 2007 named.localhost -rw-r----- 1 root named 168 Dec 15 2009 named.loopback -rw-r----- 1 root named 198 Nov 7 15:59 shenzhen.baidu.com.zone drwxrwx--- 2 named named 6 Oct 31 2018 slaves -rw-r--r-- 1 root root 94 Nov 7 20:33 wang.com.zone [root@centos7-1named]#chgrp named wang.com.zone [root@centos7-1named]#chmod 640 wang.com.zone
配置完之后重新加载DNS服务:
dndc reload
在主服务器A上修改相应的配置文件,/etc/named.conf
[root@ansible~]#vim /etc/named.conf
options {
// listen-on port 53 { localhost; };
listen-on-v6 port 53 { ::1; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
recursing-file "/var/named/data/named.recursing";
secroots-file "/var/named/data/named.secroots";
// allow-query { any; };
allow-transfer { 192.168.34.103; };
forward only ; 将转发服务器的IP地址写到主服务器上面,保证只转发此IP地址
forwarders {192.168.34.103;};
dnssec-enable no; 将此两个功能关掉
dnssec-validation no; 关掉此功能
配置完之后重新加载DNS服务:
rndc reload 重新加载DNS服务
最后在客户端C上验证转发功能:
[root@centos6~]#dig www.wang.com ; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.68.rc1.el6 <<>> www.wang.com ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 41040 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 1 ;; QUESTION SECTION: ;www.wang.com. IN A ;; ANSWER SECTION: www.wang.com. 86063 IN A 6.6.6.6 ;; AUTHORITY SECTION: wang.com. 86063 IN NS dns1.wang.com. ;; ADDITIONAL SECTION: dns1.wang.com. 86063 IN A 192.168.34.102 ;; Query time: 2 msec ;; SERVER: 192.168.34.101#53(192.168.34.101) ;; WHEN: Thu Nov 7 20:54:11 2019 ;; MSG SIZE rcvd: 81
查看当前没有配置的域名,此时客户端发起请求,A服务器上没有,就会转发到服务器B IP地址为103机器上,此时B服务器如果有网络,就会在网上寻找答案
[root@centos6~]#dig www.wange.com ; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.68.rc1.el6 <<>> www.wange.com ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 28947 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 0 ;; QUESTION SECTION: ;www.wange.com. IN A ;; ANSWER SECTION: www.wange.com. 7200 IN A 93.90.145.101此时IP地址103在网上返回的答案 ;; Query time: 2356 msec ;; SERVER: 192.168.34.101#53(192.168.34.101) ;; WHEN: Thu Nov 7 21:36:54 2019 ;; MSG SIZE rcvd: 47
第二种方式服务器转发方式:
first用法:当客户端去访问服务器A时,此时A不知道结果会转发给B,B不知道结果,此时A会自己去询问根去反馈结果:
(1)在服务器A上写配置文件/etc/named.conf,将端口转发给服务器B(103IP地址)
[root@ansible~]#vim /etc/named.conf
options {
// listen-on port 53 { localhost; };
listen-on-v6 port 53 { ::1; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
recursing-file "/var/named/data/named.recursing";
secroots-file "/var/named/data/named.secroots";
// allow-query { any; };
allow-transfer { 192.168.34.103; };
forward first ;
forwarders {192.168.34.103;};
重新加载A服务器的DNS服务:
rndc reload
(2)将服务器B的网络断掉,此时B无法访问网络。
(3)在客户端进行访问当前的一个未知的网址,A主机如果不知道,先会转发给B服务器,B服务器不知道结果,A服务器主动去网上寻找答案:
[root@centos6~]#dig www.wange.com ; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.68.rc1.el6 <<>> www.wange.com ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 52394 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 5, ADDITIONAL: 10 ;; QUESTION SECTION: ;www.wange.com. IN A ;; ANSWER SECTION: www.wange.com. 7200 IN A 93.90.145.101 ;; AUTHORITY SECTION: wange.com. 172755 IN NS ns01.crystone.se. wange.com. 172755 IN NS ns05.crystone.se. wange.com. 172755 IN NS ns03.crystone.se. wange.com. 172755 IN NS ns04.crystone.se. wange.com. 172755 IN NS ns02.crystone.se. ;; ADDITIONAL SECTION: ns01.crystone.se. 884 IN A 194.58.193.60 ns01.crystone.se. 884 IN AAAA 2a01:3f1:460::53 ns02.crystone.se. 86382 IN A 185.42.137.108 ns02.crystone.se. 884 IN AAAA 2a01:3f0:400::60 ns03.crystone.se. 884 IN A 194.58.193.124 ns03.crystone.se. 86382 IN AAAA 2a01:3f1:460:1::53 ns04.crystone.se. 884 IN A 185.42.137.126 ns04.crystone.se. 884 IN AAAA 2a01:3f0:400::190 ns05.crystone.se. 884 IN A 93.90.145.25 ns05.crystone.se. 884 IN AAAA 2a06:1003:1:1::5d5a:9119 ;; Query time: 2247 msec ;; SERVER: 192.168.34.101#53(192.168.34.101) ;; WHEN: Thu Nov 7 21:50:10 2019 ;; MSG SIZE rcvd: 373
标签:配置文件 一个 查看 无法访问 may ade host roots named
原文地址:https://www.cnblogs.com/struggle-1216/p/12582269.html