标签:lag pack image 不难 xor hex for col 一个
测试文件:
有两处关键点
第一处
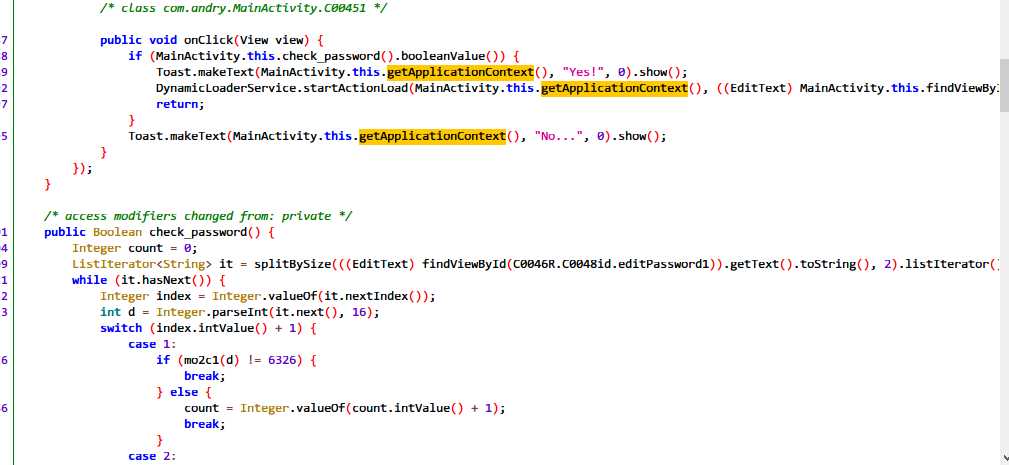
Onclick在对我们的键盘事件进行响应处理,调用check_password函数。通过check_password函数,我们知道密码长度为32,且调用了mo2c1等函数,这些函数是libandry-lib.so文件中的。
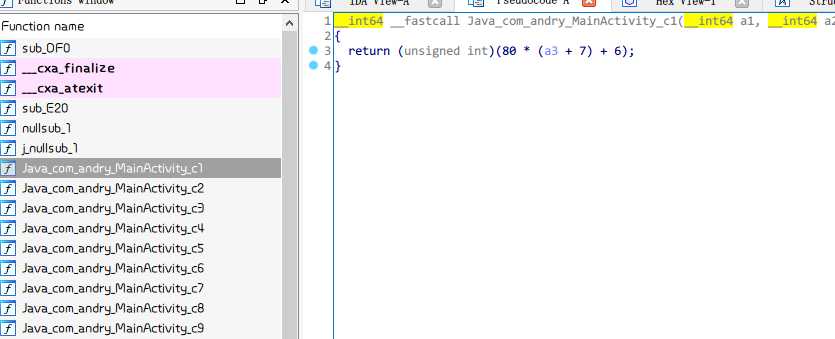
因此,我们可以逆推出输入为
48bb6e862e54f2a795ffc4e541caed4dbf985de4d3d7c5df73cf960638b4bf2
但是我们输入之后,依然会闪退。
第二处
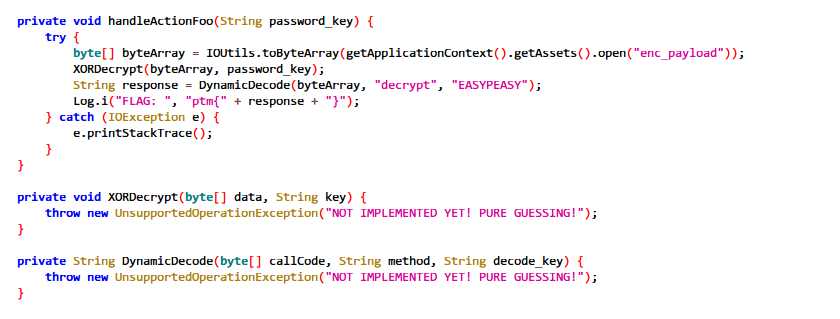
这里对enc_payload文件与我们的输入经过XORecrypt函数和DynamicDecode函数,输出flag,这里两个函数都没有定义,需要我们guess。
实际上,XORecrypt函数是将输入与enc_payload文件进行异或,这里不难猜出,可以看到结果
猜测应该是生成了一个dex文件,在调用dex文件中DynamicDecode函数,进行解密。写出脚本
# -*- coding:utf-8 -*- import binascii a = [72,187,110,134,46,84,242,167,149,255,196,229,65,202,237,77,11,249,133,222,77,61,124,93,247,60,249,96,99,139,75,242] b = [0x2C,0xDE,0x16,0x8C,0x1E,0x67,0xC7,0xA7,0x36,0x6F,0x11,0xB3,0x0F,0x6E,0x5C,0x13,0x2C,0x1B,0x60,0xE4,0x3C,0x61,0xA4,0xC2,0xDB,0xC0,0xE0,0x02,0x80,0x7F,0x22,0x0D,0xE8,0xBF,0x6E,0x86,0x5E,0x54,0xF2,0xA7,0xED,0xA9,0xF0,0xF7,0x41,0xCA,0xED,0x4D,0x0B,0xF9,0x85,0xDE,0x55,0x39,0x7C,0x5D,0xE0,0x3C,0xF9,0x60,0x13,0x8B,0x4B,0xF2,0x4F,0xBB,0x6E,0x86,0xE2,0x54,0xF2,0xA7,0x9D,0xFF,0xC4,0xE5,0xA9,0xCA,0xED,0x4D,0x0B,0xF9,0x85,0xDE,0x4D,0x3D,0x7C,0x5D,0xFB,0x3C,0xF9,0x60,0x2B,0x8A,0x4B,0xF2,0x49,0xBB,0x6E,0x86,0x86,0x55,0xF2,0xA7,0x4D,0xFD,0xC4,0xE5,0x89,0xCB,0xED,0x4D,0x21,0xFA,0x85,0xDE,0x61,0x3E,0x7C,0x5D,0xC3,0x3F,0xF9,0x60,0x54,0x88,0x4B,0xF2,0x73,0xB8,0x6E,0x86,0x10,0x57,0xF2,0xA7,0xD4,0xFC,0xC4,0xE5,0x04,0xC9,0xED,0x4D,0x45,0xFA,0x85,0xDE,0x1F,0x3E,0x7C,0x5D,0xA0,0x3F,0xF9,0x60,0x08,0x88,0x4B,0xF2,0x37,0xB8,0x6E,0x86,0xB4,0x57,0xF2,0xA7,0x2D,0xFC,0xC4,0xE5,0xFA,0xC9,0xED,0x4D,0xC8,0xFA,0x85,0xDE,0x86,0x3E,0x7C,0x5D,0x23,0x3F,0xF9,0x60,0xBE,0x88,0x4B,0xF2,0xAB,0xB8,0x6E,0x86,0xC5,0x57,0xF2,0xA7,0x60,0xFC,0xC4,0xE5,0x43,0xCA,0xED,0x4D,0x0F,0xF9,0x85,0xDE,0x4A,0x3D,0x7C,0x5D,0xFD,0x3C,0xF9,0x60,0x68,0x8B,0x4B,0xF2,0x44,0xBB,0x6E,0x86,0x20,0x54,0xF2,0xA7,0x96,0xFF,0xC4,0xE5,0x41,0xCA,0xED,0x4D,0x07,0xFA,0x85,0xDE,0x49,0x3D,0x7C,0x5D,0xF6,0x3C,0xF9,0x60,0x63,0x8B,0x4B,0xF2,0x4D,0xBB,0x6E,0x86,0x2A,0x54,0xF2,0xA7,0x95,0xFF,0xC4,0xE5,0x49,0xCA,0xED,0x4D,0x0F,0xF9,0x85,0xDE,0x59,0x3E,0x7C,0x5D,0xFE,0x3C,0xF9,0x60,0x67,0x8B,0x4B,0xF2,0x54,0xB8,0x6E,0x86,0x28,0x54,0xF2,0xA7,0x90,0xFF,0xC4,0xE5,0x65,0xC9,0xED,0x4D,0x03,0xF9,0x85,0xDE,0x48,0x3D,0x7C,0x5D,0xE3,0x3F,0xF9,0x60,0x6D,0x8B,0x4B,0xF2,0x4E,0xBB,0x6E,0x86,0x2E,0x54,0xF2,0xA7,0x97,0xFF,0xC3,0xE5,0x40,0xCA,0xED,0x4D,0x09,0xF9,0x86,0xDE,0x5C,0x3D,0x7C,0x5D,0xF5,0x3C,0xFD,0x60,0x71,0x8B,0x4B,0xF2,0x4A,0xBB,0x69,0x86,0x3D,0x54,0xF2,0xA7,0x96,0xFF,0xC3,0xE5,0x40,0xCA,0xED,0x4D,0x0F,0xF9,0x85,0xDE,0x5D,0x3D,0x7C,0x5D,0xF3,0x3C,0xF8,0x60,0x77,0x8B,0x4B,0xF2,0x4C,0xBB,0x6C,0x86,0x38,0x54,0xF2,0xA7,0x90,0xFF,0xC3,0xE5,0x40,0xCA,0xED,0x4D,0x0E,0xF9,0x80,0xDE,0x42,0x3D,0x7C,0x5D,0xF2,0x3C,0xFF,0x60,0x6C,0x8B,0x4B,0xF2,0x4D,0xBB,0x6C,0x86,0x3B,0x54,0xF2,0xA7,0x97,0xFF,0xC4,0xE5,0x40,0xCA,0xED,0x4D,0x08,0xF9,0x85,0xDE,0x4D,0x3D,0x7C,0x5D,0x08,0xC3,0x06,0x9F,0x63,0x8B,0x4B,0xF2,0x4A,0xBF,0x6E,0x86,0x2E,0x54,0xF2,0xA7,0x94,0xFF,0xC5,0xE5,0x40,0xCA,0xED,0x4D,0x0B,0xF9,0x85,0xDE,0x49,0x3D,0x7C,0x5D,0x87,0x2C,0xFD,0x60,0x63,0x8B,0x45,0xF2,0x4F,0xBB,0x6F,0x86,0x2C,0x54,0xF2,0xA7,0x95,0xFF,0xC4,0xE5,0x7C,0xCA,0xED,0x4D,0x19,0xF9,0x9F,0xDC,0x40,0x3D,0x66,0x5C,0xF7,0x3C,0x97,0x70,0x64,0x8B,0x49,0xF2,0x44,0xB8,0x69,0x94,0x2F,0x55,0x9C,0xB7,0x93,0xFF,0xC7,0xE5,0x4B,0xCE,0xD8,0x0C,0x26,0xF9,0xEB,0xFE,0x48,0x3D,0x6F,0x5D,0xFD,0x38,0xDB,0x65,0x66,0x8B,0x3B,0xE2,0x40,0xBB,0x6B,0x86,0x40,0x74,0xF8,0xA7,0xB0,0xFF,0xC8,0xE7,0x2F,0xEA,0xE8,0x4D,0x0D,0xF9,0x8F,0xDB,0xFC,0x69,0xA4,0x59,0xF3,0x26,0x25,0x64,0x67,0x91,0x93,0xF6,0x4C,0xFA,0xE0,0xC2,0x40,0x74,0xFB,0xA7,0xD7,0xFF,0xC8,0xE7,0x2F,0xDA,0xE6,0x4D,0x09,0xF9,0x89,0xDC,0x95,0x3D,0x7C,0x5C,0x99,0x2C,0xFF,0x60,0x65,0x8B,0x41,0xF6,0xFC,0xFB,0xB6,0x87,0x2F,0x55,0xDA,0x77,0x84,0xFD,0xC4,0xE5,0x49,0xCA,0xEF,0x4D,0x09,0xF9,0x85,0xDE,0x4D,0x3D,0x7C,0x5D,0xCA,0x3C,0xF9,0x60,0x71,0x8B,0x51,0xF3,0x48,0xBB,0x00,0x96,0x29,0x54,0xF4,0xA7,0x99,0xFC,0xC3,0xF7,0x40,0xCB,0x83,0x5D,0x0D,0xF9,0x86,0xDE,0x47,0x39,0x49,0x1C,0xD8,0x3C,0x97,0x40,0x66,0x8B,0x58,0xF2,0x42,0xBF,0x4C,0x83,0x2B,0x54,0x82,0xB7,0x9D,0xFF,0xC1,0xE5,0x2F,0xEA,0xE7,0x4D,0x2E,0xF9,0x89,0xDC,0x95,0x39,0x78,0xE2,0x99,0x1C,0xFC,0x60,0x64,0x8B,0x41,0xF7,0x90,0xBE,0x6B,0x39,0x9E,0x00,0x2E,0xA3,0x91,0xE5,0x1C,0xE1,0x45,0x8B,0x63,0x09,0x65,0xD9,0x8C,0xDE,0x0F,0x3D,0x70,0x5F,0x99,0x2C,0xF2,0x60,0x61,0x8B,0x47,0xF0,0x90,0xBB,0x6E,0x87,0x40,0x44,0xF4,0xA7,0x92,0xFF,0xCE,0xE1,0xF5,0x8A,0x35,0x4C,0x0A,0xF8,0xAD,0x10,0x5C,0x3F,0x7C,0x5D,0xF6,0x3C,0xF8,0x60,0x63,0x8B,0x4B,0xF2,0x48,0xBB,0x6E,0x86,0x2F,0x54,0xF2,0xA7,0x9B,0xFF,0xC4,0xE5,0x40,0xCA,0xED,0x4D,0x0A,0xF9,0x85,0xDE,0x4C,0x3D,0x7C,0x5D,0xF3,0x3C,0xF9,0x60,0x61,0x8B,0x4B,0xF2,0x4C,0xBB,0x6A,0x86,0x2F,0x54,0xF2,0xA7,0x95,0xFF,0xC4,0xE5,0x47,0xF6,0x84,0x23,0x62,0x8D,0xBB,0xDE,0x4C,0x7E,0x7C,0x5F,0xB4,0x75,0xF9,0x61,0x2A,0x8B,0x4A,0xBE,0x48,0xB9,0x22,0xC5,0x2E,0x53,0xBE,0xEE,0xFB,0x91,0xA1,0x97,0x7A,0xCA,0xEF,0x01,0x47,0xF9,0x86,0x92,0x01,0x71,0x7C,0x4F,0xBB,0x56,0x98,0x16,0x02,0xA4,0x27,0x93,0x26,0xDC,0x41,0xC9,0x4C,0x3E,0x97,0xC4,0xE1,0xC4,0xC4,0xF7,0x0D,0xA0,0x8C,0x3B,0x6A,0xD6,0xE9,0xBF,0x23,0x5A,0x53,0x0E,0x83,0x4E,0x90,0x0E,0x04,0xB0,0x4B,0xEB,0x04,0xD1,0x0F,0xF0,0x4F,0x7B,0x9E,0xC6,0xFB,0x98,0xEB,0xB6,0x35,0xB8,0x84,0x23,0x6C,0xBB,0xF0,0xB7,0x21,0x59,0x19,0x2F,0xCC,0x3C,0xE5,0x2E,0x36,0xC0,0x19,0xA2,0x0E,0xEE,0x28,0xC7,0x62,0x1B,0xAA,0xFE,0xD9,0xB5,0x91,0xA1,0x18,0x98,0xA9,0x07,0x46,0xA1,0xCD,0x93,0x1A,0x6C,0x2B,0x5D,0xF6,0x6A,0xF9,0x66,0x02,0xFB,0x3B,0x97,0x26,0xDF,0x6E,0x80,0x4D,0x3C,0x93,0xD5,0xD4,0x8B,0xC4,0xE2,0x25,0xAF,0x8E,0x3F,0x72,0x89,0xF1,0xDE,0x4A,0x58,0x12,0x3E,0x85,0x45,0x89,0x14,0x63,0x8F,0x20,0x97,0x2D,0xCB,0x6E,0x80,0x42,0x31,0x9C,0xC0,0xE1,0x97,0xC4,0xED,0x35,0xA5,0xBE,0x39,0x79,0x90,0xEB,0xB9,0x4D,0x36,0x08,0x32,0xA2,0x4C,0x89,0x05,0x11,0xC8,0x2A,0x81,0x2D,0xBB,0x6E,0x86,0x2D,0x55,0xF2,0x26,0x15,0xFB,0x0C,0xE6,0x40,0xC3,0x0D,0x4E,0x0A,0xF0,0x69,0xDA,0x4E,0x3C,0x84,0x58,0xFC,0x3C,0xF9,0x60,0x63,0x8B,0x4B,0xF2,0x49,0xBB,0x6E,0x86,0x2E,0x54,0xF2,0xA7,0x94,0xFF,0xC4,0xE5,0x56,0xCA,0xED,0x4D,0x7B,0xF9,0x85,0xDE,0x4F,0x3D,0x7C,0x5D,0xF0,0x3C,0xF9,0x60,0xAF,0x8B,0x4B,0xF2,0x4B,0xBB,0x6E,0x86,0x26,0x54,0xF2,0xA7,0x7D,0xFF,0xC4,0xE5,0x44,0xCA,0xED,0x4D,0x07,0xF9,0x85,0xDE,0x05,0x3C,0x7C,0x5D,0xF1,0x3C,0xF9,0x60,0x62,0x8B,0x4B,0xF2,0xE0,0xBA,0x6E,0x86,0x2F,0x74,0xF2,0xA7,0x91,0xFF,0xC4,0xE5,0x89,0xCB,0xED,0x4D,0x0A,0xE9,0x85,0xDE,0x49,0x3D,0x7C,0x5D,0xFB,0x3F,0xF9,0x60,0x61,0xAB,0x4B,0xF2,0x5F,0xBB,0x6E,0x86,0x04,0x57,0xF2,0xA7,0x95,0xDF,0xC4,0xE5,0x40,0xCA,0xED,0x4D,0x09,0xFD,0x85,0xDE,0x4D,0x2D,0x7C,0x5D,0xF6,0x3C,0xF9,0x60,0x7B,0x8F,0x4B,0xF2] data = [] for i in range(len(b)): data.append(b[i]^a[i%len(a)]) print (data) s = ‘‘ for x in data: tmp = hex(x)[2:] if len(tmp) == 1: tmp = ‘0‘+tmp s += tmp print (s) s = binascii.a2b_hex(s) with open(‘biu.dex‘,‘wb+‘) as f: f.write(s)
package p000; /* renamed from: Inner */ public class Inner { public static String decrypt(String str) { int i = 0; String upperCase = "NUKRPFUFALOXYLJUDYRDJMXHMWQW".toUpperCase(); String str2 = ""; for (int i2 = 0; i2 < upperCase.length(); i2++) { str2 = str2 + ((char) ((((upperCase.charAt(i2) - str.charAt(i)) + 26) % 26) + 65)); i = (i + 1) % str.length(); } return str2; } public static String encrypt(String str, String str2) { int i = 0; String upperCase = str.toUpperCase(); String str3 = ""; for (int i2 = 0; i2 < upperCase.length(); i2++) { str3 = str3 + ((char) ((((upperCase.charAt(i2) - ‘A‘) + (str2.charAt(i) - ‘A‘)) % 26) + 65)); i = (i + 1) % str2.length(); } return str3; } public void keep() { } }
调用的decrypt函数,我们能够很轻松写出脚本解密
s = "EASYPEASY" m = "NUKRPFUFALOXYLJUDYRDJMXHMWQW".upper() flag = ‘‘ i = 0 for j in range(len(m)): flag += chr(((ord(m[j]) - ord(s[i]))+26)%26+65) i = (i+1)%len(s) print (‘ptm{‘+flag+‘}‘)
ptm{JUSTABUNCHOFAWFULANDROIDMESS}
ptm{JUSTABUNCHOFAWFULANDROIDMESS}
标签:lag pack image 不难 xor hex for col 一个
原文地址:https://www.cnblogs.com/Mayfly-nymph/p/12969463.html