标签:ken tcp http -o mes app star push bad
架构图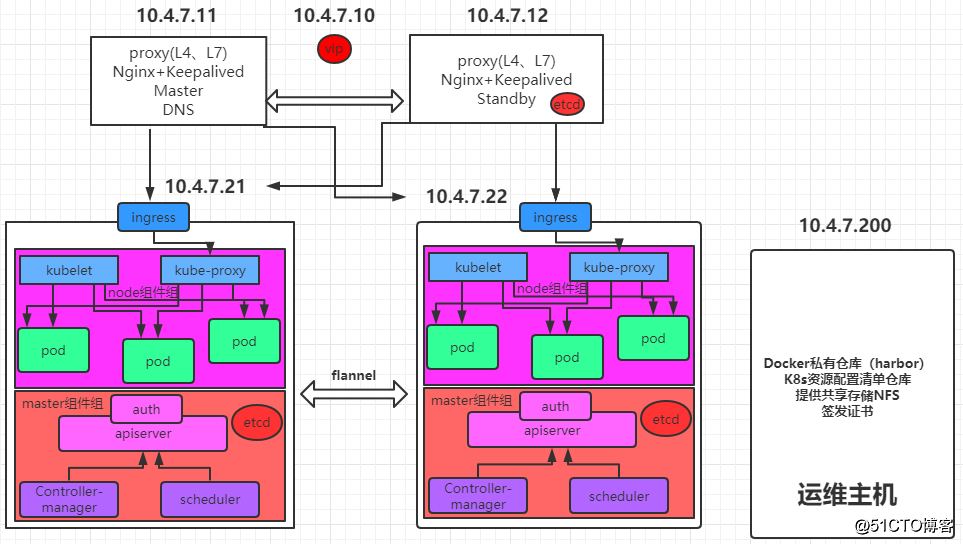
hdss7-200.host.com上操作
docker pull hexun/kubernetes-dashboard-amd64:v1.10.1
docker tag f9aed6605b81 harbor.od.com/k8s/dashboard:v1.10.1
docker push harbor.od.com/k8s/dashboard:v1.10.1mkdir -p /data/k8s-yaml/dashboard && cd /data/k8s-yaml/dashboard参考链接 https://github.com/kubernetes/kubernetes/blob/master/cluster/addons/dashboard/dashboard.yaml
cat > /data/k8s-yaml/dashboard/rbac.yaml <<‘eof‘
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
k8s-app: kubernetes-dashboard
addonmanager.kubernetes.io/mode: Reconcile
name: kubernetes-dashboard-admin
namespace: kube-system
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: kubernetes-dashboard-admin
namespace: kube-system
labels:
k8s-app: kubernetes-dashboard
addonmanager.kubernetes.io/mode: Reconcile
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: kubernetes-dashboard-admin
namespace: kube-system
eofcat > /data/k8s-yaml/dashboard/secret.yaml <<‘eof‘
apiVersion: v1
kind: Secret
metadata:
labels:
k8s-app: kubernetes-dashboard
# Allows editing resource and makes sure it is created first.
addonmanager.kubernetes.io/mode: EnsureExists
name: kubernetes-dashboard-certs
namespace: kube-system
type: Opaque
---
apiVersion: v1
kind: Secret
metadata:
labels:
k8s-app: kubernetes-dashboard
# Allows editing resource and makes sure it is created first.
addonmanager.kubernetes.io/mode: EnsureExists
name: kubernetes-dashboard-key-holder
namespace: kube-system
type: Opaque
eofcat > /data/k8s-yaml/dashboard/configmap.yaml <<‘eof‘
apiVersion: v1
kind: ConfigMap
metadata:
labels:
k8s-app: kubernetes-dashboard
# Allows editing resource and makes sure it is created first.
addonmanager.kubernetes.io/mode: EnsureExists
name: kubernetes-dashboard-settings
namespace: kube-system
eofcat > /data/k8s-yaml/dashboard/deployment.yaml <<‘eof‘
apiVersion: apps/v1
kind: Deployment
metadata:
name: kubernetes-dashboard
namespace: kube-system
labels:
k8s-app: kubernetes-dashboard
kubernetes.io/cluster-service: "true"
addonmanager.kubernetes.io/mode: Reconcile
spec:
selector:
matchLabels:
k8s-app: kubernetes-dashboard
template:
metadata:
labels:
k8s-app: kubernetes-dashboard
annotations:
scheduler.alpha.kubernetes.io/critical-pod: ‘‘
spec:
priorityClassName: system-cluster-critical
containers:
- name: kubernetes-dashboard
image: harbor.od.com/k8s/dashboard:v2.0.4
resources:
limits:
cpu: 100m
memory: 300Mi
requests:
cpu: 50m
memory: 100Mi
ports:
- containerPort: 8443
protocol: TCP
args:
# PLATFORM-SPECIFIC ARGS HERE
- --auto-generate-certificates
volumeMounts:
- name: kubernetes-dashboard-certs
mountPath: /certs
- name: tmp-volume
mountPath: /tmp
livenessProbe:
httpGet:
scheme: HTTPS
path: /
port: 8443
initialDelaySeconds: 30
timeoutSeconds: 30
volumes:
- name: kubernetes-dashboard-certs
secret:
secretName: kubernetes-dashboard-certs
- name: tmp-volume
emptyDir: {}
serviceAccountName: kubernetes-dashboard-admin
tolerations:
- key: "CriticalAddonsOnly"
operator: "Exists"
imagePullSecrets:
- name: harbor
eofcat > /data/k8s-yaml/dashboard/svc.yaml <<‘eof‘
apiVersion: v1
kind: Service
metadata:
name: kubernetes-dashboard
namespace: kube-system
labels:
k8s-app: kubernetes-dashboard
kubernetes.io/cluster-service: "true"
addonmanager.kubernetes.io/mode: Reconcile
spec:
selector:
k8s-app: kubernetes-dashboard
ports:
- port: 443
targetPort: 8443
eofcat > /data/k8s-yaml/dashboard/ingress.yaml <<‘eof‘
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: kubernetes-dashboard
namespace: kube-system
annotations:
kubernetes.io/ingress.class: traefik
spec:
rules:
- host: dashboard.od.com
http:
paths:
- path: /
backend:
serviceName: kubernetes-dashboard
servicePort: 443
eofopenssl生成证书方式(需先生成ca.pem,ca-key.pem)
cd /opt/certs/
(umask 077;openssl genrsa -out dashboard.od.com.key 2048)
openssl req -new -key dashboard.od.com.key -out dashboard.od.com.csr -subj "/CN=dashboard.od.com/C=CN/ST=GZ/L=GuangZhou/O=k8s/OU=k8s"
openssl x509 -req -in dashboard.od.com.csr -CA ca.pem -CAkey ca-key.pem -CAcreateserial -out dashboard.od.com.crt -days 3650
[root@hdss7-200 certs]# ll dashboard.od.com.*
-rw-r--r-- 1 root root 1196 10月 5 22:49 dashboard.od.com.crt
-rw-r--r-- 1 root root 1001 10月 5 22:49 dashboard.od.com.csr
-rw------- 1 root root 1675 10月 5 22:49 dashboard.od.com.key
scp hdss7-200:/opt/certs/dashboard.od.com.crt /etc/nginx/certs/
scp hdss7-200:/opt/certs/dashboard.od.com.csr /etc/nginx/certs/hdss7-11上操作
cat >> /var/named/od.com.zone <<eof
dashboard A 10.4.7.10
eof
vi /var/named/od.com.zone
2020100505 ; serial # 数字加1
system restart namedhdss7-11和hdss7-12上操作
mkdir -p /etc/nginx/certs
cat > /etc/nginx/conf.d/dashboard.od.com.conf <<‘eof‘
server {
listen 80;
server_name dashboard.od.com;
rewrite ^(.*)$ https://${server_name}$1 permanent;
}
server {
listen 443 ssl;
server_name dashboard.od.com;
ssl_certificate "certs/dashboard.od.com.crt";
ssl_certificate_key "certs/dashboard.od.com.key";
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 10m;
ssl_ciphers HIGH:!aNULL:!MD5;
ssl_prefer_server_ciphers on;
location / {
proxy_pass http://default_backend_traefik;
proxy_set_header Host $http_host;
proxy_set_header x-forwarded-for $proxy_add_x_forwarded_for;
}
}
eofhdss7-21或hdss7-22上执行
kubectl apply -f http://k8s-yaml.od.com/dashboard/rbac.yaml
kubectl apply -f http://k8s-yaml.od.com/dashboard/secret.yaml
kubectl apply -f http://k8s-yaml.od.com/dashboard/configmap.yaml
kubectl apply -f http://k8s-yaml.od.com/dashboard/svc.yaml
kubectl apply -f http://k8s-yaml.od.com/dashboard/ingress.yaml
kubectl apply -f http://k8s-yaml.od.com/dashboard/deployment.yaml[root@hdss7-22 /]# kubectl get secret -n kube-system
NAME TYPE DATA AGE
coredns-token-xvr85 kubernetes.io/service-account-token 3 42h
default-token-q9rpn kubernetes.io/service-account-token 3 3d10h
harbor kubernetes.io/dockerconfigjson 1 2d9h
kubernetes-dashboard-admin-token-dpb77 kubernetes.io/service-account-token 3 10h
kubernetes-dashboard-certs Opaque 0 10h
kubernetes-dashboard-key-holder Opaque 2 10h
traefik-ingress-controller-token-b2z7n kubernetes.io/service-account-token 3 25h
[root@hdss7-22 /]# kubectl describe secret kubernetes-dashboard-admin-token-dpb77 -n kube-system
Name: kubernetes-dashboard-admin-token-dpb77
Namespace: kube-system
Labels: <none>
Annotations: kubernetes.io/service-account.name: kubernetes-dashboard-admin
kubernetes.io/service-account.uid: daa17a07-bd8b-4ac7-bc45-d883badb7102
Type: kubernetes.io/service-account-token
Data
====
ca.crt: 1359 bytes
namespace: 11 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6Ind4Rk9fbGdYbWdHNlc0OUFHNXQyUTdSc2JIaGNubnZ6TTRfSWtsYkpITVUifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJrdWJlcm5ldGVzLWRhc2hib2FyZC1hZG1pbi10b2tlbi1kcGI3NyIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJrdWJlcm5ldGVzLWRhc2hib2FyZC1hZG1pbiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6ImRhYTE3YTA3LWJkOGItNGFjNy1iYzQ1LWQ4ODNiYWRiNzEwMiIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDprdWJlLXN5c3RlbTprdWJlcm5ldGVzLWRhc2hib2FyZC1hZG1pbiJ9.WFQf5jiRdztyOopdRI9gGZxDcZ4xrIwHMTC38IopnTkxkokSF4vywcnRrZyH-0mmDHXTGrval6cgSN_rdslkpVjcgmfKMnvJ7eGt-oEqryDPj6CAl_ZaXk2R4cvMN8kJMcl5zktix9f1pd6H3hQVMMRGXk_E-WmTq80GQXbdABqvasNglTT8XlQmNX3tDk-EAP4ctL3UUw1R_cTKe43dKmwwf2QmTg1aDNBYUk3rFL1duMjjefOw9yeBPXLcGBB4UOtfIWQCCpyVJNUW9UU7tx829Z8a_nzA5Ee8LO7DGe-yoAF688G70AHVgHRRF10T28yuK1cp8M8bkvcVGT_R-g
kubectl get clusterrole cluster-admin -o yaml # 查看集群admin权限配置web访问: https://dashboard.od.com/
复制上面的token登陆
二进制部署K8s集群第23节addons之安装部署dashboard
标签:ken tcp http -o mes app star push bad
原文地址:https://blog.51cto.com/yht1990/2540394