标签:ports als cert case epo time new oca rman
1.定义一个deployment
[root@k8s-master01 service-ingress]# cat nginx-test.yaml
---
apiVersion: v1
kind: Service
metadata:
name: ingress-test
labels:
app: ingress-test
spec:
selector:
app: ingress-test
type: ClusterIP
ports:
- name: web
port: 80
protocol: TCP
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: ingress-test
labels:
app: ingress-test
spec:
replicas: 1
selector:
matchLabels:
app: ingress-test
template:
metadata:
labels:
app: ingress-test
spec:
containers:
- name: nginx
image: nginx:1.15.2
imagePullPolicy: IfNotPresent
volumeMounts:
- name: tz-config
mountPath: /etc/localtime
readOnly: true
volumes:
- name: tz-config
hostPath:
path: /usr/share/zoneinfo/Asia/Shanghai
2.定义一个ingress
[root@k8s-master01 service-ingress]# cat ingress-web.yaml
apiVersion: networking.k8s.io/v1beta1
kind: Ingress
metadata:
name: ingress-test
annotations:
kubernetes.io/ingressClass: "nginx"
spec:
rules:
- host: ingress.test.com
http:
paths:
- path: /
backend:
serviceName: ingress-test
servicePort: 80
[root@k8s-master01 service-ingress]# kubectl apply -f ingress-web.yaml
[root@k8s-master01 service-ingress]# kubectl apply -f nginx-test.yaml
3.查看ingress-nginx-controller跑再在哪node上,win本地做域名解析
[root@k8s-master01 service-ingress]# kubectl get pod -n ingress-nginx -owide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
ingress-nginx-controller-8bhfm 1/1 Running 0 9h 192.168.0.110 k8s-node01 <none> <none>
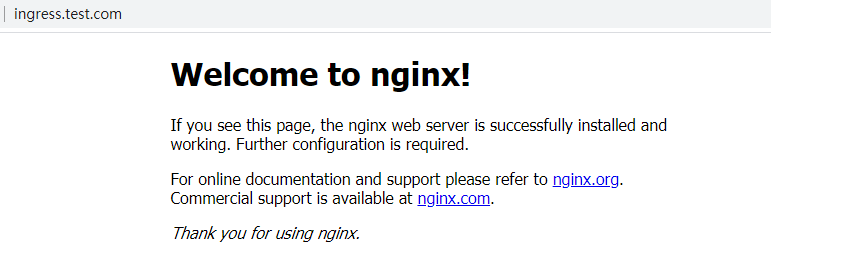
只需要添加一个annotation,就能将访问指向重定向的网址
[root@k8s-master01 service-ingress]# cat ingress-web.yaml
apiVersion: networking.k8s.io/v1beta1
kind: Ingress
metadata:
name: ingress-test
annotations:
kubernetes.io/ingressClass: "nginx"
nginx.ingress.kubernetes.io/permanent-redirect: "https://www.baidu.com" #新增,这里指定重定向网站
spec:
rules:
- host: ingress.test.com
http:
paths:
- path: /
backend:
serviceName: ingress-test
servicePort: 80
# 查看ingress-nginx-controller配置文件
[root@k8s-master01 service-ingress]# kubectl exec -it ingress-nginx-controller-8bhfm -n ingress-nginx -- bash
bash-5.1$ cat nginx.conf | grep "end server ingress.test.com" -B 20
proxy_request_buffering on;
proxy_http_version 1.1;
proxy_cookie_domain off;
proxy_cookie_path off;
# In case of errors try the next upstream server before returning an error
proxy_next_upstream error timeout;
proxy_next_upstream_timeout 0;
proxy_next_upstream_tries 3;
return 301 https://www.baidu.com; ### 发现配置中有 return 301,跳转到百度去了
proxy_pass http://upstream_balancer;
proxy_redirect off;
}
}
## end server ingress.test.com
[root@k8s-master01 service-ingress]# cat ingress-web.yaml
apiVersion: networking.k8s.io/v1beta1
kind: Ingress
metadata:
name: ingress-test
annotations:
kubernetes.io/ingressClass: "nginx"
nginx.ingress.kubernetes.io/rewrite-target: /$2 #修改这里
spec:
rules:
- host: ingress.test.com
http:
paths:
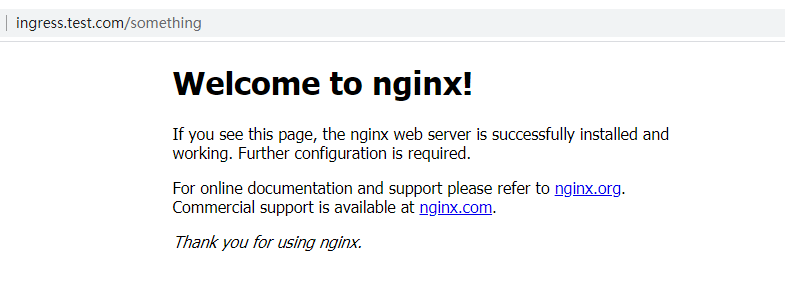
- path: /something(/|$)(.*) # 修改这里
backend:
serviceName: ingress-test
servicePort: 80
# 将xxx.com/something/xxx 重定向到 xxx.com/xxx
# 该处其实还是重定向到 ingress.test.com根目录下
# 1.创建证书
[root@k8s-master01 service-ingress]# openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout tls.key -out tls.cert -subj "/CN=ingress.test.com/O=ingress.test.com"
Generating a 2048 bit RSA private key
................................+++
........................+++
writing new private key to ‘tls.key‘
-----
# 2.创建secret
[root@k8s-master01 service-ingress]# kubectl create secret tls ca-cert --key tls.key --cert tls.cert
secret/ca-cert created
[root@k8s-master01 service-ingress]# kubectl get secret
NAME TYPE DATA AGE
ca-cert kubernetes.io/tls 2 38s
# 3.创建ingress请求域名
[root@k8s-master01 service-ingress]# cat ingress-web.yaml
apiVersion: networking.k8s.io/v1beta1
kind: Ingress
metadata:
name: ingress-test
annotations:
kubernetes.io/ingressClass: "nginx"
spec:
rules:
- host: ingress.test.com
http:
paths:
- path: /
backend:
serviceName: ingress-test
servicePort: 80
tls:
- hosts:
- ingress.test.com
secretName: ca-cert
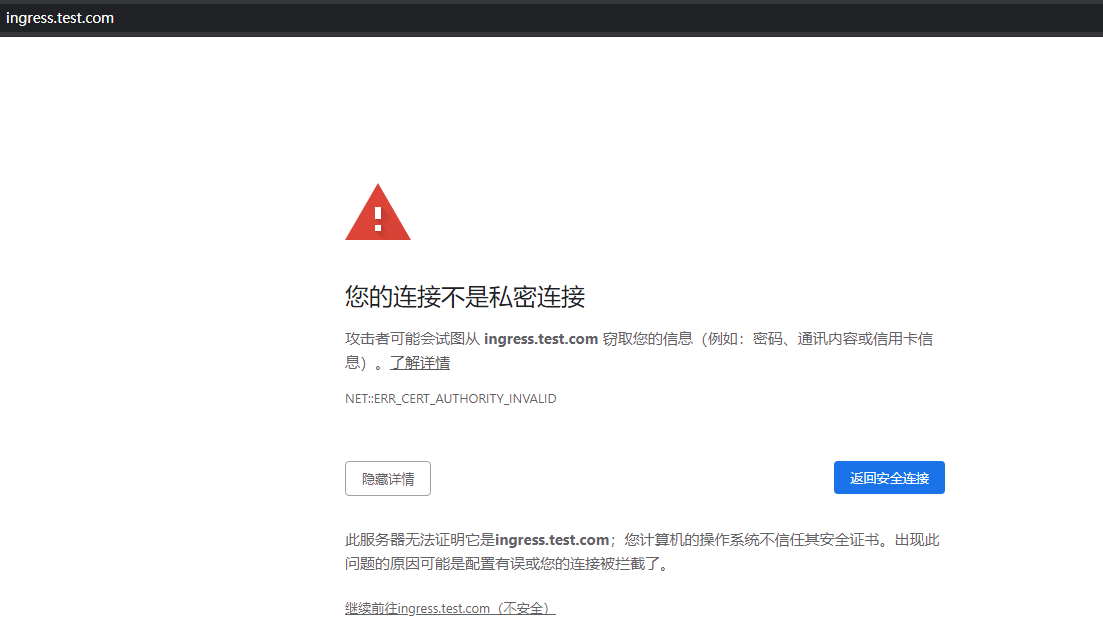
# 4.禁用https强制跳转,默认是true
annotations:
nginx.ingress.kubernetes.io/ssl-redirect: "false"
标签:ports als cert case epo time new oca rman
原文地址:https://www.cnblogs.com/Applogize/p/14665737.html