标签:iam ted auto -name com learn use visio replace
Give Admin access
1) Create facts table: **** (use ^ - Shift + 6 if you are a windows user, not \) **** aws dynamodb create-table --table-name facts --attribute-definitions AttributeName=fact_id,AttributeType=N --key-schema AttributeName=fact_id,KeyType=HASH --provisioned-throughput ReadCapacityUnits=5,WriteCapacityUnits=5 2) Populate facts table: **** (make sure items.json is in your working directory) **** aws dynamodb batch-write-item --request-items file://items.json
items.json
Install HTTPD:
#!/bin/bash yum update -y yum install -y httpd systemctl start httpd systemctl enable httpd
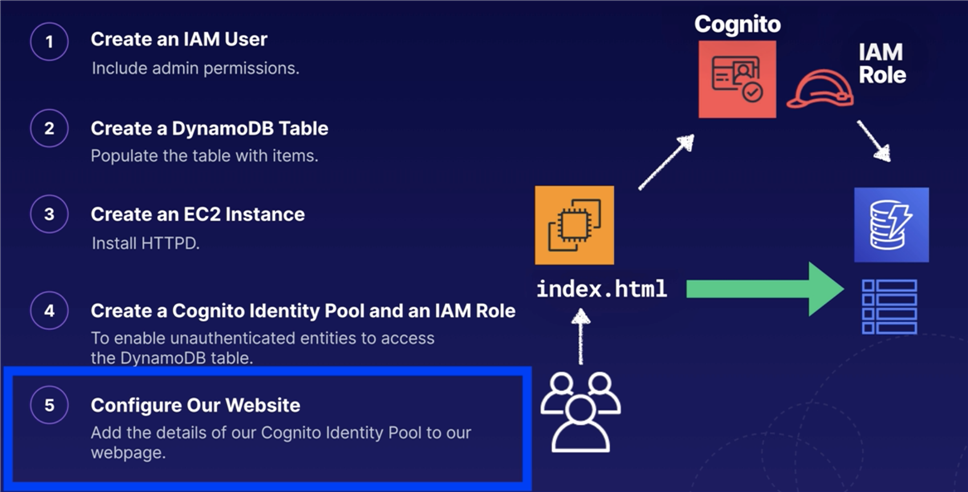
Cognito Commands: 1) Using the CLI, create new identity pool, named DynamoPool, allow unauthenticated entities. **** (use ^ - Shift + 6 if you are a windows user, not \) **** aws cognito-identity create-identity-pool --identity-pool-name DynamoPool --allow-unauthenticated-identities --output json 2) Create an IAM role named Cognito_DynamoPoolUnauth. aws iam create-role --role-name Cognito_DynamoPoolUnauth --assume-role-policy-document file://myCognitoPolicy.json --output json 3) Grant the Cognito_DynamoPoolUnauth role read access to DynamoDB by attaching a managed policy (AmazonDynamoDBReadOnlyAccess). aws iam attach-role-policy --policy-arn arn:aws:iam::aws:policy/AmazonDynamoDBReadOnlyAccess --role-name Cognito_DynamoPoolUnauth 4) Get the IAM role Amazon Resource Name (ARN). aws iam get-role --role-name Cognito_DynamoPoolUnauth --output json 5) Add our role to the Cognito Identity Pool. Replace the pool ID with your own pool ID and use the role ARN from the previous step. aws cognito-identity set-identity-pool-roles --identity-pool-id "us-east-1:xxxxxxxxxxxxxxxxxxxxxxxxxxxxx" --roles unauthenticated=arn:aws:iam::xxxxx:role/Cognito_DynamoPoolUnauthRole --output json 6) Double check it worked using: aws cognito-identity get-identity-pool-roles --identity-pool-id "us-east-1:xxxxxxxxxxxxxxxxxxxxxxxxxxxxx" 7) We can now specify the Cognito credentials in our application - i.e. in the JavaScript section of our webpage! Replace the identity pool ID with your own and the role ARN with your own role ARN. We are going to add this snippet to our index.html: AWS.config.credentials = new AWS.CognitoIdentityCredentials({ IdentityPoolId: "us-east-1:xxxxxxxxxxxxxxxxxxxxxxxxxxxxx", RoleArn: "arn:aws:iam::xxxxx:role/Cognito_DynamoPoolUnauthRole" });
myCognitoPolicy.json
[AWS] Lab: Configure a Cognito user can access DynamoDB for read
标签:iam ted auto -name com learn use visio replace
原文地址:https://www.cnblogs.com/Answer1215/p/14695278.html