标签:
| Time Limit: 2000MS | Memory Limit: 65536K | |
| Total Submissions: 12905 | Accepted: 3472 |
Description
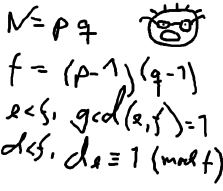 The young and very promising cryptographer Odd Even has implemented the security module of a large system with thousands of users, which is now in use in his company. The cryptographic keys are
created from the product of two primes, and are believed to be secure because there is no known method for factoring such a product effectively.
The young and very promising cryptographer Odd Even has implemented the security module of a large system with thousands of users, which is now in use in his company. The cryptographic keys are
created from the product of two primes, and are believed to be secure because there is no known method for factoring such a product effectively. Input
Output
Sample Input
143 10 143 20 667 20 667 30 2573 30 2573 40 0 0
Sample Output
GOOD BAD 11 GOOD BAD 23 GOOD BAD 31
Source
题意:给定一个大数str,str是两个大素数的乘积的值。再给定一个int内的数m问这两个大素数中最小的一个是否小于m,如果小于则输出这个素数。
#include<iostream>
#include<algorithm>
#include<stdio.h>
#include<string.h>
#include<stdlib.h>
using namespace std;
char str[100010];
int a[100100];
int m;
const int MAXN = 20000000;
bool flag[MAXN];
int primes[MAXN / 3], pi;
void GetPrime()
{
int i, j;
pi = 0;
memset(flag, false, sizeof(flag));
for (i = 2; i < MAXN; i++)
{
if (!flag[i])
{
primes[pi++] = i;
}
for (j = 0; (j < pi) && (i * primes[j] < MAXN); j++)
{
flag[i * primes[j]] = true;
if (i % primes[j] == 0)
{
break;
}
}
}
}
int main()
{
GetPrime();
while(scanf("%s%d",str,&m)!=EOF)
{
if(m == 0 && strcmp(str,"0") == 0)
{
break;
}
int len = strlen(str);
int ll = (len+2)/3;
int ans = len%3;
memset(a,0,sizeof(a));
for(int i=0; i<len; i++) ///将10进制数字转变成1000制的数字,
{
int pk = i/3;
a[pk] = a[pk]*10 + (str[i] - '0');
}
int p = 0;
int flag = 0;
int num;
while(primes[p]<m)
{
int sum = 0;
for(int i=0;i<ll;i++) /// 同余模定理
{
if(i == ll-1)
{
if(ans == 0)
{
sum = (sum*1000 + a[i])%primes[p];
}
else if(ans == 1)
{
sum = (sum*10 + a[i])%primes[p];
}
else
{
sum = (sum*100 + a[i])%primes[p];
}
}
else
{
sum = (sum*1000 + a[i])%primes[p];
}
}
if(sum == 0)
{
num = primes[p];
flag = 1;
break;
}
p++;
}
if(flag == 1)
{
printf("BAD %d\n",num);
}
else
{
printf("GOOD\n");
}
}
}
版权声明:本文为博主原创文章,如有特殊需要请与博主联系 QQ : 793977586。
POJ 2635 The Embarrassed Cryptographer(高精度取模 + 同余模定理)
标签:
原文地址:http://blog.csdn.net/yeguxin/article/details/47046037