标签:second https hat release pat plugin radmin solr except
Apache Ranger简介Apache Ranger提供一个集中式安全管理框架, 并解决授权和审计。它可以对Hadoop生态的组件如HDFS、Yarn、Hive、Hbase等进行细粒度的数据访问控制。通过操作Ranger控制台,管理员可以轻松的通过配置策略来控制用户访问权限。Ranger优点:
为什么选择Ranger:
Ranger的架构图: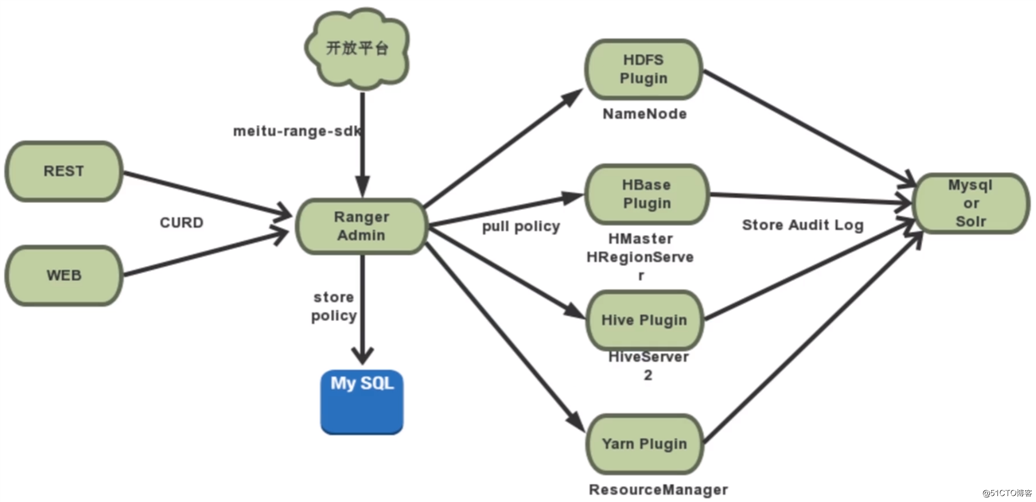
RangerAdmin:
Service Plugin:
Ranger权限模型
以HDFS为例,与Ranger集成后的访问流程: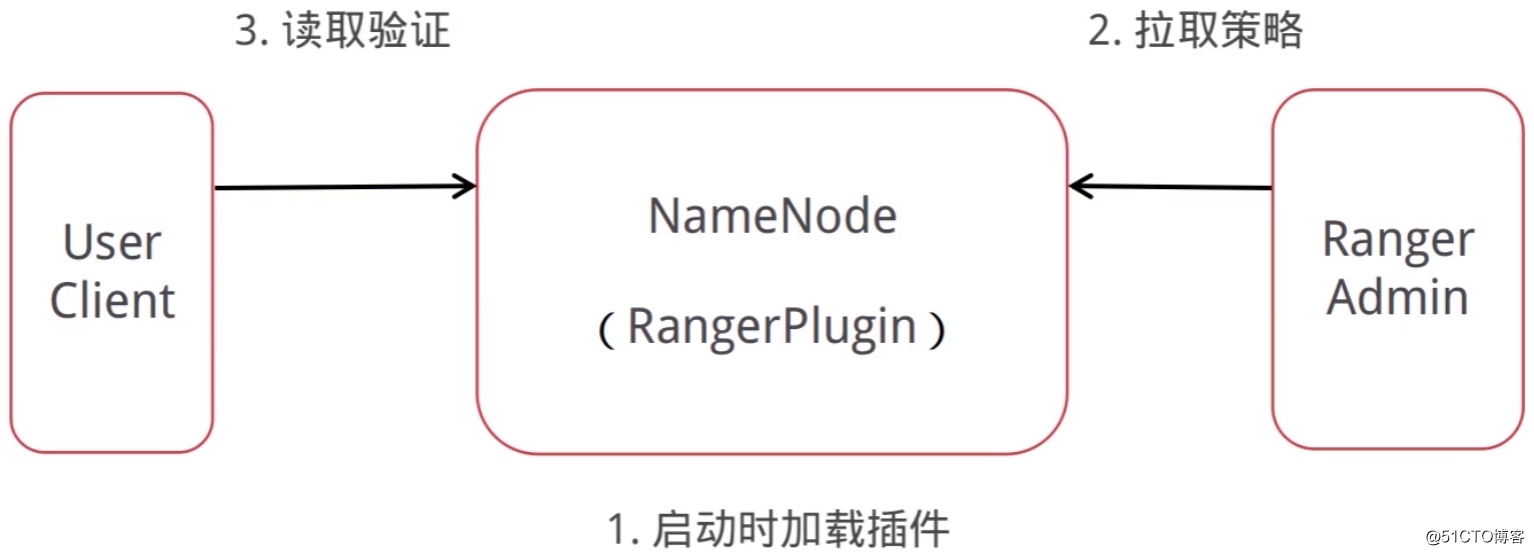
以Hive为例,与Ranger集成后的访问流程: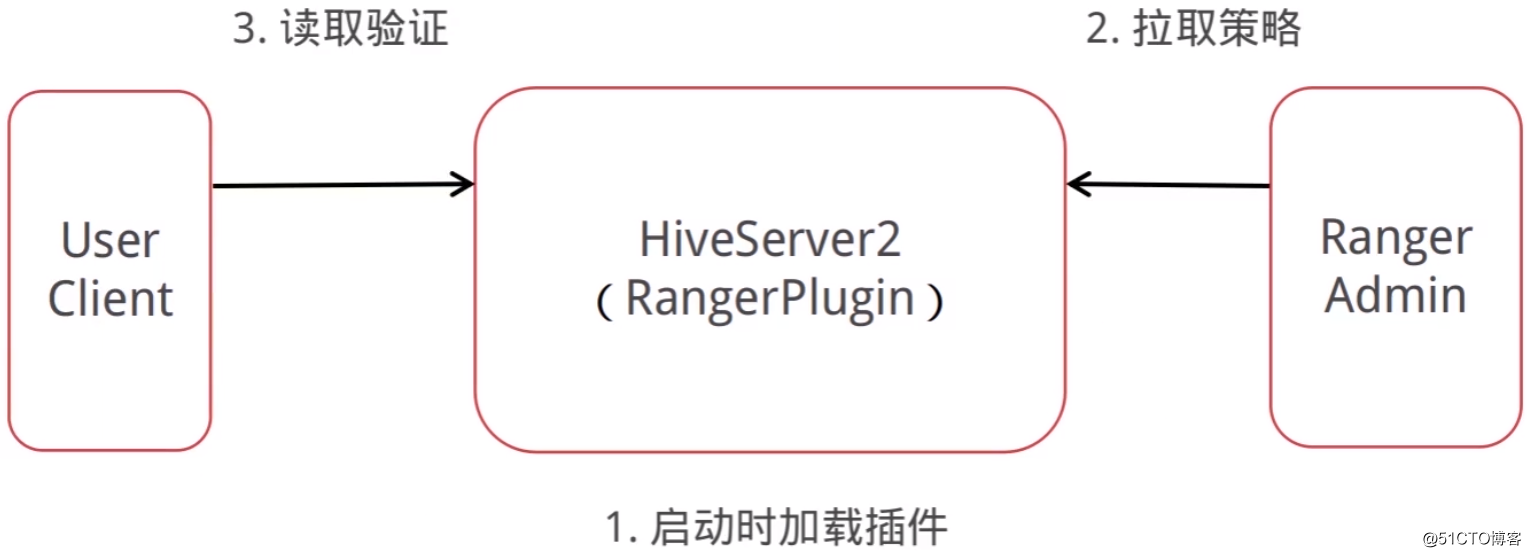
以YARN为例,与Ranger集成后的访问流程: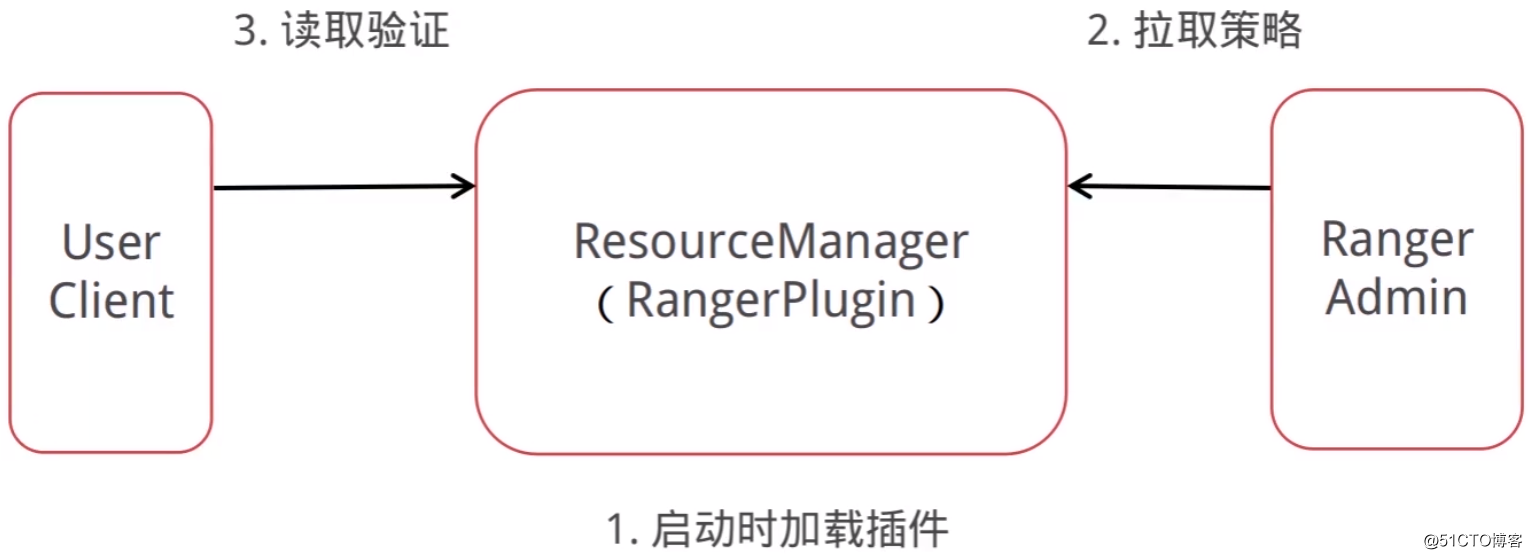
官方文档:
首先准备好Java和Maven环境:
[root@hadoop ~]# java -version
java version "1.8.0_261"
Java(TM) SE Runtime Environment (build 1.8.0_261-b12)
Java HotSpot(TM) 64-Bit Server VM (build 25.261-b12, mixed mode)
[root@hadoop ~]# mvn -v
Apache Maven 3.6.3 (cecedd343002696d0abb50b32b541b8a6ba2883f)
Maven home: /usr/local/maven
Java version: 1.8.0_261, vendor: Oracle Corporation, runtime: /usr/local/jdk/1.8/jre
Default locale: zh_CN, platform encoding: UTF-8
OS name: "linux", version: "3.10.0-1062.el7.x86_64", arch: "amd64", family: "unix"
[root@hadoop ~]# 安装一个MySQL数据库,我这里使用的是我本地的数据库:
C:\Users\Administrator>mysql --version
mysql Ver 8.0.21 for Win64 on x86_64 (MySQL Community Server - GPL)搭建一个Hadoop环境,注意Hadoop的版本一定要 >= 2.7.1,因为我之前尝试过2.6.0版本的Hadoop无法与Ranger整合成功,本文使用的是2.8.5版本:
[root@hadoop ~]# echo $HADOOP_HOME
/usr/local/hadoop-2.8.5
[root@hadoop ~]# Ranger依赖了MySQL作为状态存储,所以需要准备一个MySQL的驱动包:
[root@hadoop ~]# ls /usr/local/src |grep mysql
mysql-connector-java-8.0.21.jar
[root@hadoop ~]# 到官网上下载源码包:
需要注意Ranger与Hadoop的对应版本,如果你安装的Hadoop是2.x的,那么Ranger需要采用2.x以下的版本。如果你安装的Hadoop是3.x的,那么Ranger需要采用2.x以上的版本。例如,我这里安装的Hadoop版本是2.8.5,所以选择1.2.0版本的Ranger:
[root@hadoop ~]# cd /usr/local/src
[root@hadoop /usr/local/src]# wget https://mirror-hk.koddos.net/apache/ranger/1.2.0/apache-ranger-1.2.0.tar.gz解压源码包:
[root@hadoop /usr/local/src]# tar -zxvf apache-ranger-1.2.0.tar.gz进入解压后的目录:cd apache-ranger-1.2.0,修改该目录下的pom文件,将仓库相关配置都给注释掉:
<!--
<repositories>
<repository>
<id>apache.snapshots.https</id>
<name>Apache Development Snapshot Repository</name>
<url>https://repository.apache.org/content/repositories/snapshots</url>
<snapshots>
<enabled>true</enabled>
</snapshots>
</repository>
<repository>
<id>apache.public.https</id>
<name>Apache Development Snapshot Repository</name>
<url>https://repository.apache.org/content/repositories/public</url>
<releases>
<enabled>true</enabled>
</releases>
<snapshots>
<enabled>false</enabled>
</snapshots>
</repository>
<repository>
<id>repo</id>
<url>file://${basedir}/local-repo</url>
<snapshots>
<enabled>true</enabled>
</snapshots>
</repository>
</repositories>
-->完成以上的修改后,使用maven命令进行编译打包:
[root@hadoop /usr/local/src/apache-ranger-1.2.0]# mvn -DskipTests=true clean package assembly:assembly经过一段漫长的等待后,编译打包完成将输出如下信息:
[INFO] ------------------------------------------------------------------------
[INFO] Reactor Summary for ranger 1.2.0:
[INFO]
[INFO] ranger ............................................. SUCCESS [ 0.838 s]
[INFO] Jdbc SQL Connector ................................. SUCCESS [ 0.861 s]
[INFO] Credential Support ................................. SUCCESS [ 26.341 s]
[INFO] Audit Component .................................... SUCCESS [ 1.475 s]
[INFO] Common library for Plugins ......................... SUCCESS [ 3.154 s]
[INFO] Installer Support Component ........................ SUCCESS [ 0.471 s]
[INFO] Credential Builder ................................. SUCCESS [ 1.074 s]
[INFO] Embedded Web Server Invoker ........................ SUCCESS [ 0.807 s]
[INFO] Key Management Service ............................. SUCCESS [ 3.335 s]
[INFO] ranger-plugin-classloader .......................... SUCCESS [ 0.797 s]
[INFO] HBase Security Plugin Shim ......................... SUCCESS [ 17.365 s]
[INFO] HBase Security Plugin .............................. SUCCESS [ 6.050 s]
[INFO] Hdfs Security Plugin ............................... SUCCESS [ 5.831 s]
[INFO] Hive Security Plugin ............................... SUCCESS [02:01 min]
[INFO] Knox Security Plugin Shim .......................... SUCCESS [03:47 min]
[INFO] Knox Security Plugin ............................... SUCCESS [07:05 min]
[INFO] Storm Security Plugin .............................. SUCCESS [ 1.757 s]
[INFO] YARN Security Plugin ............................... SUCCESS [ 0.820 s]
[INFO] Ranger Util ........................................ SUCCESS [ 0.869 s]
[INFO] Unix Authentication Client ......................... SUCCESS [ 17.494 s]
[INFO] Security Admin Web Application ..................... SUCCESS [03:01 min]
[INFO] KAFKA Security Plugin .............................. SUCCESS [ 6.686 s]
[INFO] SOLR Security Plugin ............................... SUCCESS [03:07 min]
[INFO] NiFi Security Plugin ............................... SUCCESS [ 1.210 s]
[INFO] NiFi Registry Security Plugin ...................... SUCCESS [ 1.205 s]
[INFO] Unix User Group Synchronizer ....................... SUCCESS [ 2.062 s]
[INFO] Ldap Config Check Tool ............................. SUCCESS [ 3.478 s]
[INFO] Unix Authentication Service ........................ SUCCESS [ 0.638 s]
[INFO] KMS Security Plugin ................................ SUCCESS [ 1.430 s]
[INFO] Tag Synchronizer ................................... SUCCESS [01:58 min]
[INFO] Hdfs Security Plugin Shim .......................... SUCCESS [ 0.584 s]
[INFO] Hive Security Plugin Shim .......................... SUCCESS [ 24.249 s]
[INFO] YARN Security Plugin Shim .......................... SUCCESS [ 0.612 s]
[INFO] Storm Security Plugin shim ......................... SUCCESS [ 0.709 s]
[INFO] KAFKA Security Plugin Shim ......................... SUCCESS [ 0.617 s]
[INFO] SOLR Security Plugin Shim .......................... SUCCESS [ 0.716 s]
[INFO] Atlas Security Plugin Shim ......................... SUCCESS [ 31.534 s]
[INFO] KMS Security Plugin Shim ........................... SUCCESS [ 0.648 s]
[INFO] ranger-examples .................................... SUCCESS [ 0.015 s]
[INFO] Ranger Examples - Conditions and ContextEnrichers .. SUCCESS [ 1.108 s]
[INFO] Ranger Examples - SampleApp ........................ SUCCESS [ 0.386 s]
[INFO] Ranger Examples - Ranger Plugin for SampleApp ...... SUCCESS [ 0.519 s]
[INFO] Ranger Tools ....................................... SUCCESS [ 1.411 s]
[INFO] Atlas Security Plugin .............................. SUCCESS [ 3.977 s]
[INFO] Sqoop Security Plugin .............................. SUCCESS [ 3.637 s]
[INFO] Sqoop Security Plugin Shim ......................... SUCCESS [ 0.558 s]
[INFO] Kylin Security Plugin .............................. SUCCESS [01:04 min]
[INFO] Kylin Security Plugin Shim ......................... SUCCESS [ 0.883 s]
[INFO] Unix Native Authenticator .......................... SUCCESS [ 0.452 s]
[INFO] ------------------------------------------------------------------------
[INFO] BUILD SUCCESS
[INFO] ------------------------------------------------------------------------此时在target目录下可以看到打包好的插件安装包:
[root@hadoop /usr/local/src/apache-ranger-1.2.0]# ls target/
antrun ranger-1.2.0-hbase-plugin.zip ranger-1.2.0-kms.zip ranger-1.2.0-ranger-tools.zip ranger-1.2.0-storm-plugin.zip
archive-tmp ranger-1.2.0-hdfs-plugin.tar.gz ranger-1.2.0-knox-plugin.tar.gz ranger-1.2.0-solr-plugin.tar.gz ranger-1.2.0-tagsync.tar.gz
maven-shared-archive-resources ranger-1.2.0-hdfs-plugin.zip ranger-1.2.0-knox-plugin.zip ranger-1.2.0-solr-plugin.zip ranger-1.2.0-tagsync.zip
ranger-1.2.0-admin.tar.gz ranger-1.2.0-hive-plugin.tar.gz ranger-1.2.0-kylin-plugin.tar.gz ranger-1.2.0-sqoop-plugin.tar.gz ranger-1.2.0-usersync.tar.gz
ranger-1.2.0-admin.zip ranger-1.2.0-hive-plugin.zip ranger-1.2.0-kylin-plugin.zip ranger-1.2.0-sqoop-plugin.zip ranger-1.2.0-usersync.zip
ranger-1.2.0-atlas-plugin.tar.gz ranger-1.2.0-kafka-plugin.tar.gz ranger-1.2.0-migration-util.tar.gz ranger-1.2.0-src.tar.gz ranger-1.2.0-yarn-plugin.tar.gz
ranger-1.2.0-atlas-plugin.zip ranger-1.2.0-kafka-plugin.zip ranger-1.2.0-migration-util.zip ranger-1.2.0-src.zip ranger-1.2.0-yarn-plugin.zip
ranger-1.2.0-hbase-plugin.tar.gz ranger-1.2.0-kms.tar.gz ranger-1.2.0-ranger-tools.tar.gz ranger-1.2.0-storm-plugin.tar.gz version
[root@hadoop /usr/local/src/apache-ranger-1.2.0]# 将ranger admin的安装包解压到合适的目录下,我这里习惯放到/usr/local:
[root@hadoop /usr/local/src/apache-ranger-1.2.0]# tar -zxvf target/ranger-1.2.0-admin.tar.gz -C /usr/local/进入解压后的目录,目录结构如下:
[root@hadoop /usr/local/src/apache-ranger-1.2.0]# cd /usr/local/ranger-1.2.0-admin/
[root@hadoop /usr/local/ranger-1.2.0-admin]# ls
bin contrib dba_script.py ews ranger_credential_helper.py set_globals.sh templates-upgrade upgrade.sh
changepasswordutil.py cred db_setup.py install.properties restrict_permissions.py setup_authentication.sh update_property.py version
changeusernameutil.py db deleteUserGroupUtil.py jisql rolebasedusersearchutil.py setup.sh upgrade_admin.py
[root@hadoop /usr/local/ranger-1.2.0-admin]# 配置安装选项:
[root@hadoop /usr/local/ranger-1.2.0-admin]# vim install.properties
# 指定MySQL驱动包所在的路径
SQL_CONNECTOR_JAR=/usr/local/src/mysql-connector-java-8.0.21.jar
# 配置root用户名密码以及MySQL实例的连接地址
db_root_user=root
db_root_password=123456a.
db_host=192.168.1.11
# 配置访问数据库的用户名密码
db_name=ranger_test
db_user=root
db_password=123456a.
# 指定审计日志的存储方式
audit_store=db
audit_db_user=root
audit_db_name=ranger_test
audit_db_password=123456a.在MySQL中创建ranger数据库:
create database ranger_test;由于我这里使用的是MySQL8.x,需要修改一下数据库相关的脚本,不是MySQL8版本的可以跳过这一步。打开dba_script.py和db_setup.py文件,搜索如下内容:
-cstring jdbc:mysql://%s/%s%s将其全部修改为如下所示,主要是添加JDBC的serverTimezone连接参数:
-cstring jdbc:mysql://%s/%s%s?serverTimezone=Asia/Shanghai然后执行如下命令开始安装ranger admin:
[root@hadoop /usr/local/ranger-1.2.0-admin]# ./setup.sh安装过程中如果报如下错误:
SQLException : SQL state: HY000 java.sql.SQLException: Operation CREATE USER failed for ‘root‘@‘localhost‘ ErrorCode: 1396
SQLException : SQL state: 42000 java.sql.SQLSyntaxErrorException: Access denied for user ‘root‘@‘192.168.1.11‘ to database ‘mysql‘ ErrorCode: 1044解决方式,就是在MySQL中执行如下语句:
use mysql;
flush privileges;
grant system_user on *.* to ‘root‘;
drop user‘root‘@‘localhost‘;
create user ‘root‘@‘localhost‘ identified by ‘123456a.‘;
grant all privileges on *.* to ‘root‘@‘localhost‘ with grant option;
drop user‘root‘@‘192.168.1.11‘;
create user ‘root‘@‘192.168.1.11‘ identified by ‘123456a.‘;
grant all privileges on *.* to ‘root‘@‘192.168.1.11‘ with grant option;
flush privileges;如果报如下错误:
SQLException : SQL state: HY000 java.sql.SQLException: This function has none of DETERMINISTIC, NO SQL, or READS SQL DATA in its declaration and binary logging is enabled (you *might* want to use the less safe log_bin_trust_function_creators variable) ErrorCode: 1418解决方式:
set global log_bin_trust_function_creators=TRUE;
flush privileges;如果报如下错误:
SQLException : SQL state: HY000 java.sql.SQLException: Cannot drop table ‘x_policy‘ referenced by a foreign key constraint ‘x_policy_ref_role_FK_policy_id‘ on table ‘x_policy_ref_role‘. ErrorCode: 3730解决方式:删除ranger库中所有的表,再重新执行./setup.sh
安装完成后最终会输出:
Installation of Ranger PolicyManager Web Application is completed.修改配置文件,配置数据库连接密码和jdbc url时区参数:
[root@hadoop /usr/local/ranger-1.2.0-admin]# vim conf/ranger-admin-site.xml
...
<property>
<name>ranger.jpa.jdbc.url</name>
<value>jdbc:log4jdbc:mysql://192.168.1.11/ranger_test?serverTimezone=Asia/Shanghai</value>
<description />
</property>
<property>
<name>ranger.jpa.jdbc.user</name>
<value>root</value>
<description />
</property>
<property>
<name>ranger.jpa.jdbc.password</name>
<value>123456a.</value>
<description />
</property>
...修改审计存储相关配置:
[root@hadoop /usr/local/ranger-1.2.0-admin]# vim conf/ranger-admin-default-site.xml
...
<property>
<name>ranger.jpa.audit.jdbc.url</name>
<value>jdbc:log4jdbc:mysql://192.168.1.11:3306/ranger_test?serverTimezone=Asia/Shanghai</value>
<description />
</property>
<property>
<name>ranger.jpa.audit.jdbc.user</name>
<value>root</value>
<description />
</property>
<property>
<name>ranger.jpa.audit.jdbc.password</name>
<value>123456a.</value>
<description />
</property>
...启动命令如下:
[root@hadoop /usr/local/ranger-1.2.0-admin]# ranger-admin start
Starting Apache Ranger Admin Service
Apache Ranger Admin Service with pid 21102 has started.
[root@hadoop /usr/local/ranger-1.2.0-admin]# 检查端口和进程是否正常:
[root@hadoop /usr/local/ranger-1.2.0-admin]# jps
21194 Jps
21102 EmbeddedServer
[root@hadoop /usr/local/ranger-1.2.0-admin]# netstat -lntp |grep 21102
tcp6 0 0 :::6080 :::* LISTEN 21102/java
tcp6 0 0 127.0.0.1:6085 :::* LISTEN 21102/java
[root@hadoop /usr/local/ranger-1.2.0-admin]# 使用浏览器访问6080端口,进入到登录页面,默认用户名和密码均为admin:
登录成功后,进入到首页,如下:
解压hdfs plugin的安装包到合适的目录下:
[root@hadoop ~]# mkdir /usr/local/ranger-plugin
[root@hadoop ~]# tar -zxvf /usr/local/src/apache-ranger-1.2.0/target/ranger-1.2.0-hdfs-plugin.tar.gz -C /usr/local/ranger-plugin
[root@hadoop ~]# cd /usr/local/ranger-plugin/
[root@hadoop /usr/local/ranger-plugin]# mv ranger-1.2.0-hdfs-plugin/ hdfs-plugin进入解压后的目录,目录结构如下:
[root@hadoop /usr/local/ranger-plugin/hdfs-plugin]# ls
disable-hdfs-plugin.sh enable-hdfs-plugin.sh install install.properties lib ranger_credential_helper.py upgrade-hdfs-plugin.sh upgrade-plugin.py
[root@hadoop /usr/local/ranger-plugin/hdfs-plugin]# 配置安装选项:
[root@hadoop /usr/local/ranger-plugin/hdfs-plugin]# vim install.properties
# 指定ranger admin服务的访问地址
POLICY_MGR_URL=http://192.168.243.161:6080
# 配置仓库名称,可自定义
REPOSITORY_NAME=dev_hdfs
# 配置hadoop的安装目录
COMPONENT_INSTALL_DIR_NAME=/usr/local/hadoop-2.8.5
# 配置用户和用户组
CUSTOM_USER=root
CUSTOM_GROUP=root执行如下脚本开启hdfs-plugin:
[root@hadoop /usr/local/ranger-plugin/hdfs-plugin]# ./enable-hdfs-plugin.sh 脚本执行成功后,会输出如下内容:
Ranger Plugin for hadoop has been enabled. Please restart hadoop to ensure that changes are effective.重启Hadoop:
[root@hadoop ~]# stop-all.sh
[root@hadoop ~]# start-all.sh到Ranger Admin上添加hdfs service,这里的Service Name需与配置文件中的配置所对应上:
填写相应信息: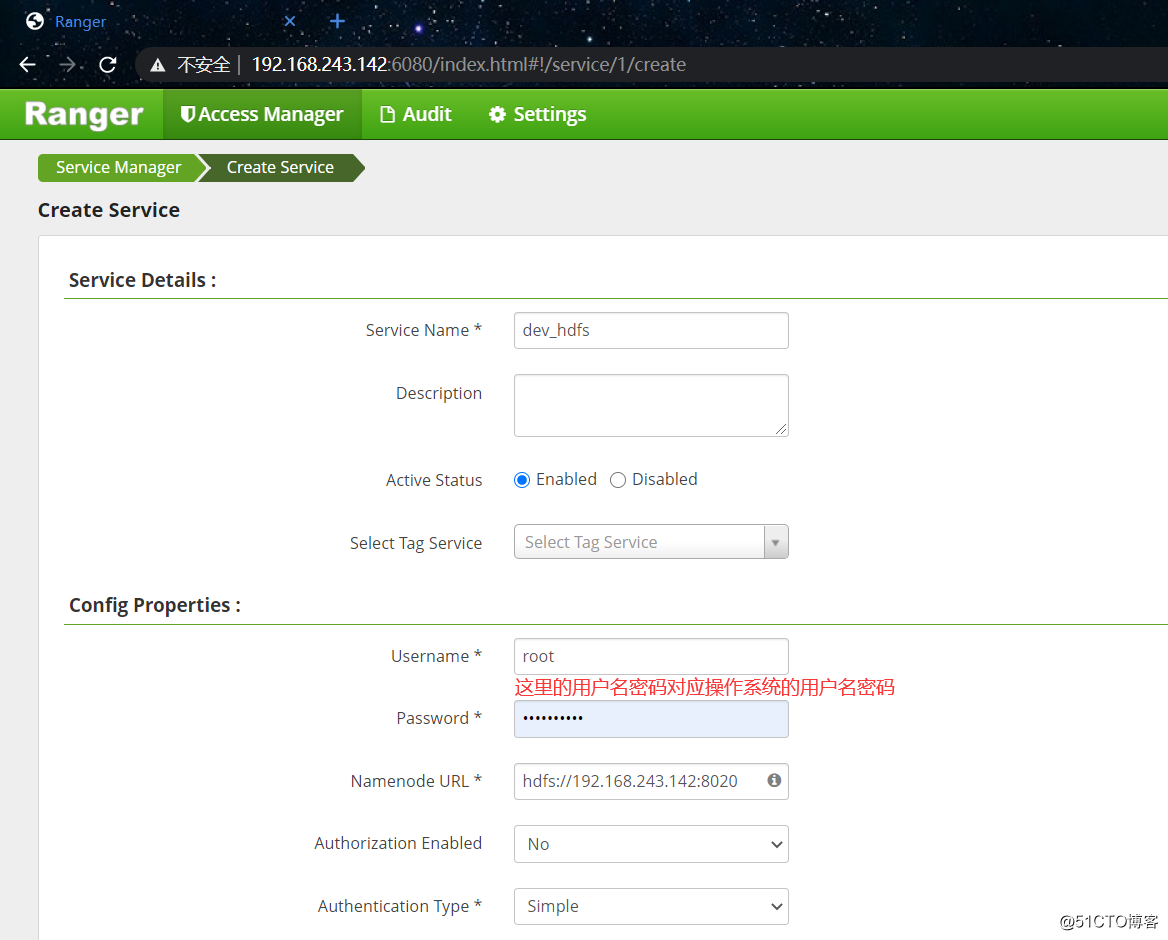
填写完成后,到页面底部点击“Test Connection”测试能否正常连接,确认可以正常连接后点击“Add”完成新增:
等待一会后,到 “Audit” -> “Plugins” 页面查看有没有发现hdfs插件,如果没有的话代表插件没有启用成功。正常情况如下: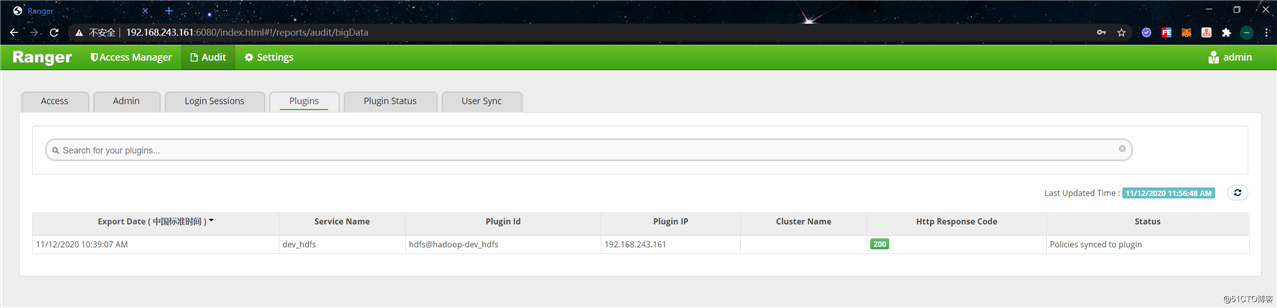
确认hdfs插件整合成功后,在hdfs中创建一些测试目录和文件:
[root@hadoop ~]# hdfs dfs -mkdir /rangertest1
[root@hadoop ~]# hdfs dfs -mkdir /rangertest2
[root@hadoop ~]# echo "ranger test" > testfile
[root@hadoop ~]# hdfs dfs -put testfile /rangertest1
[root@hadoop ~]# hdfs dfs -put testfile /rangertest2然后到Ranger Admin上添加Ranger的内部用户,“Settings” -> “Add New User”,填写用户信息: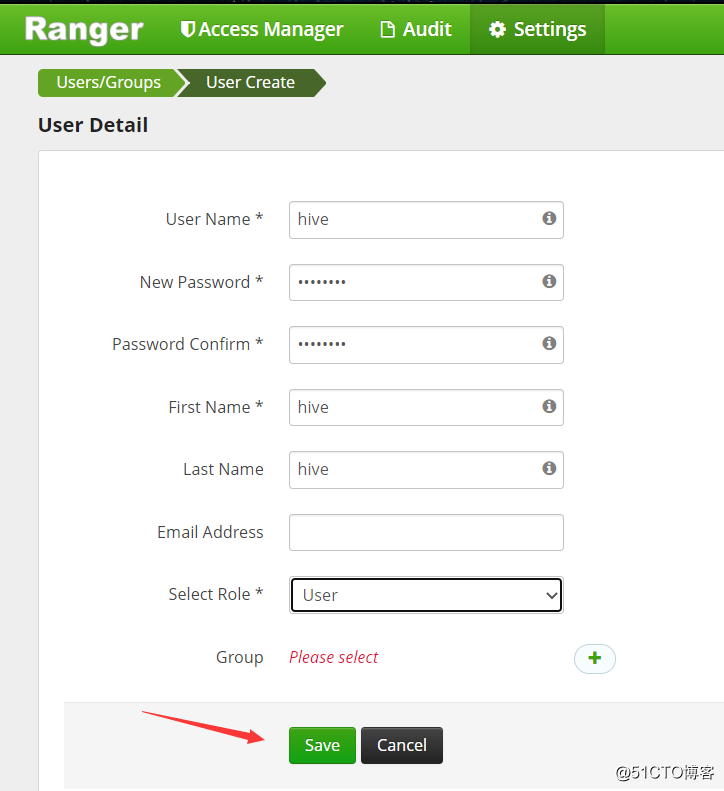
接着添加权限策略,“Access Manager” -> “dev_hdfs” -> “Add New Policy”,配置权限策略所作用的用户、目录等信息: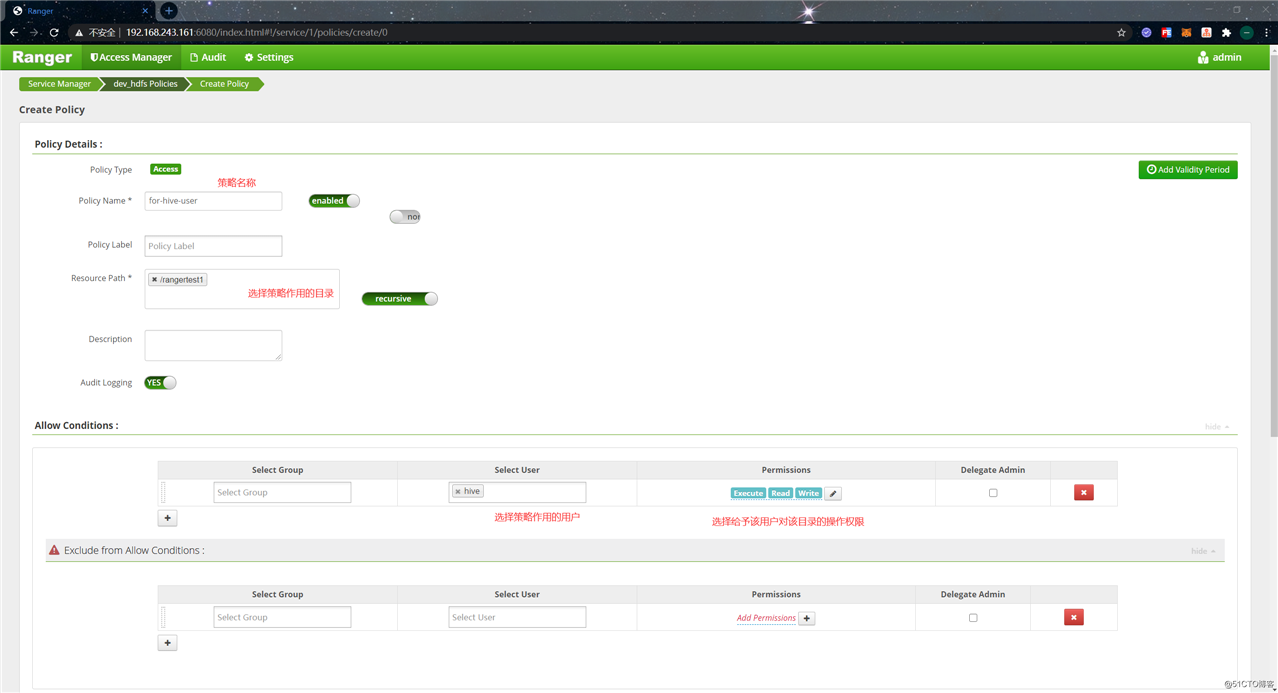
拉到底部点击“Add”完成添加后,可以看到新增了一条策略配置: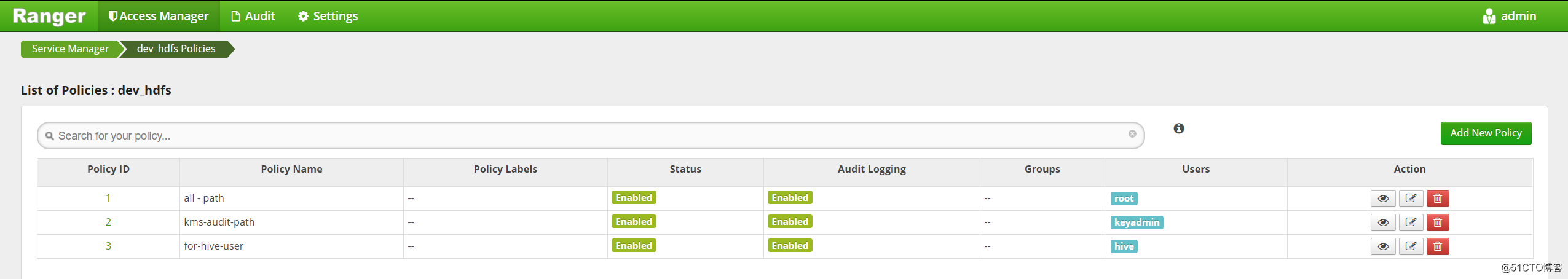
回到操作系统,添加并切换到hive用户,测试能否正常读取目录、文件:
[root@hadoop ~]# sudo su - hive
[hive@hadoop ~]$ hdfs dfs -ls /
Found 2 items
drwxr-xr-x - root supergroup 0 2020-11-12 13:48 /rangertest1
drwxr-xr-x - root supergroup 0 2020-11-12 13:48 /rangertest2
[hive@hadoop ~]$ hdfs dfs -ls /rangertest1
Found 1 items
-rw-r--r-- 1 root supergroup 12 2020-11-12 13:48 /rangertest1/testfile
[hive@hadoop ~]$ hdfs dfs -cat /rangertest1/testfile
ranger test
[hive@hadoop ~]$ hdfs dfs -ls /rangertest2
Found 1 items
-rw-r--r-- 1 root supergroup 12 2020-11-12 13:48 /rangertest2/testfile
[hive@hadoop ~]$ 通过查看目录信息可以看到rangertest1和rangertest2目录的权限位是:drwxr-xr-x,也就说除root外的用户是没权限对这两个目录进行写操作的。
但此时测试写操作,会发现hive用户能够正常往rangertest1目录添加文件,但往rangertest2目录添加文件就会报错,因为在Ranger中我们只赋予了hive用户对rangertest1目录的读写权限:
[hive@hadoop ~]$ echo "this is test file 2" > testfile2
[hive@hadoop ~]$ hdfs dfs -put testfile2 /rangertest1
[hive@hadoop ~]$ hdfs dfs -put testfile2 /rangertest2
put: Permission denied: user=hive, access=WRITE, inode="/rangertest2":root:supergroup:drwxr-xr-x
[hive@hadoop ~]$ 如果我们想禁止hive用户对rangertest2目录的所有操作,那么就可以新增一条拒绝策略,“Resource Path”选择rangertest2目录,并且在“Deny Conditions”一栏中勾选需要deny的权限即可: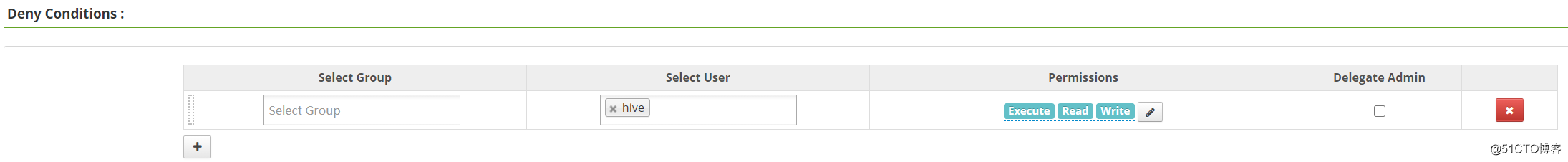
策略生效后,此时hive用户访问rangertest2目录就会提示权限拒绝了:
[hive@hadoop ~]$ hdfs dfs -ls /rangertest2
ls: Permission denied: user=hive, access=EXECUTE, inode="/rangertest2"
[hive@hadoop ~]$ hdfs dfs -cat /rangertest2/testfile
cat: Permission denied: user=hive, access=EXECUTE, inode="/rangertest2/testfile"
[hive@hadoop ~]$ 至此,Ranger对HDFS的权限控制也验证通过了。除此之外,你也可以进行其他的测试。
首先需要搭建好Hive环境,可以参考下文:
为了与Hadoop和Ranger版本保持兼容,本文使用的Hive版本是2.3.6:
[root@hadoop ~]# echo $HIVE_HOME
/usr/local/apache-hive-2.3.6-bin
[root@hadoop ~]# 解压hive plugin的安装包到合适的目录下:
[root@hadoop ~]# tar -zxvf /usr/local/src/apache-ranger-1.2.0/target/ranger-1.2.0-hive-plugin.tar.gz -C /usr/local/ranger-plugin/
[root@hadoop /usr/local/ranger-plugin]# mv ranger-1.2.0-hive-plugin/ hive-plugin进入解压后的目录,目录结构如下:
[root@hadoop /usr/local/ranger-plugin]# cd hive-plugin/
[root@hadoop /usr/local/ranger-plugin/hive-plugin]# ls
disable-hive-plugin.sh enable-hive-plugin.sh install install.properties lib ranger_credential_helper.py upgrade-hive-plugin.sh upgrade-plugin.py
[root@hadoop /usr/local/ranger-plugin/hive-plugin]# 配置安装选项:
[root@hadoop /usr/local/ranger-plugin/hive-plugin]# vim install.properties
# 指定ranger admin服务的访问地址
POLICY_MGR_URL=http://192.168.243.161:6080
# 配置仓库名称,可自定义
REPOSITORY_NAME=dev_hive
# 配置hive的安装目录
COMPONENT_INSTALL_DIR_NAME=/usr/local/apache-hive-2.3.6-bin
# 配置用户和用户组
CUSTOM_USER=root
CUSTOM_GROUP=root执行如下脚本开启hive-plugin:
[root@hadoop /usr/local/ranger-plugin/hive-plugin]# ./enable-hive-plugin.sh 脚本执行成功后,会输出如下内容:
Ranger Plugin for hive has been enabled. Please restart hive to ensure that changes are effective.重启Hive:
[root@hadoop ~]# jps
8258 SecondaryNameNode
9554 EmbeddedServer
8531 NodeManager
13764 Jps
7942 NameNode
11591 RunJar
8040 DataNode
8428 ResourceManager
[root@hadoop ~]# kill -15 11591
[root@hadoop ~]# nohup hiveserver2 -hiveconf hive.execution.engine=mr &到Ranger Admin上添加hive service,这里的Service Name需与配置文件中的配置所对应上:
填写相应信息,并点击“Add”完成新增: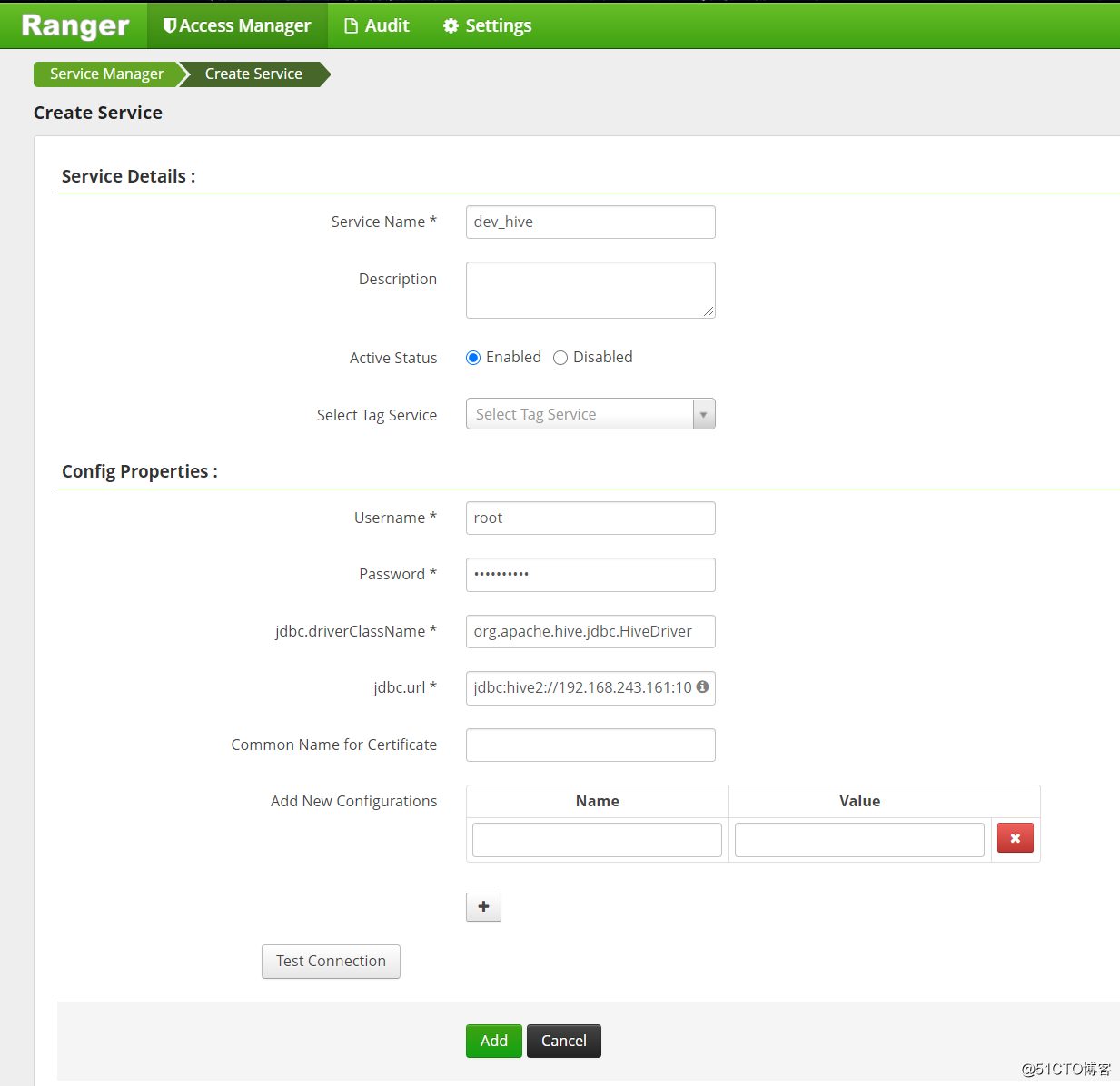
等待一会后,到 “Audit” -> “Plugins” 页面查看有没有探测到该hive插件,如果没有的话代表插件没有启用成功。正常情况如下: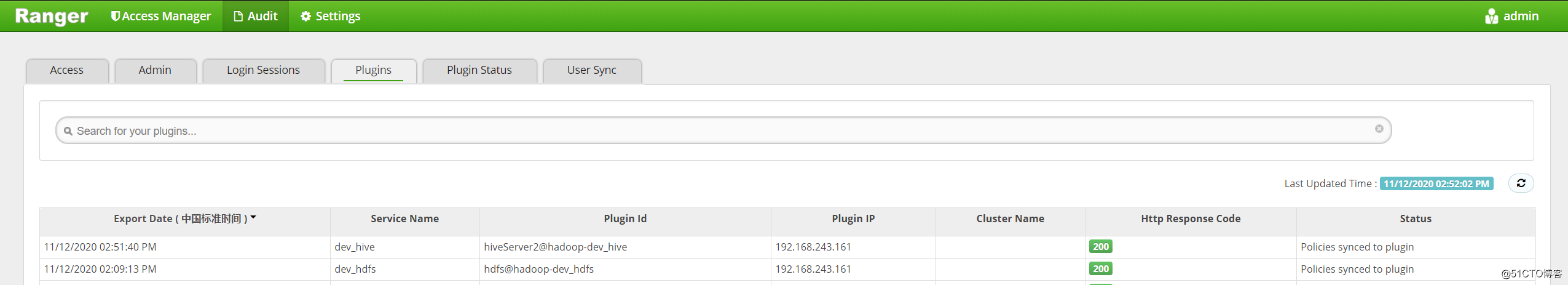
确认hive插件整合成功后,添加权限策略,“Access Manager” -> “dev_hive” -> “Add New Policy”,配置权限策略所作用的用户、库、表、列等信息: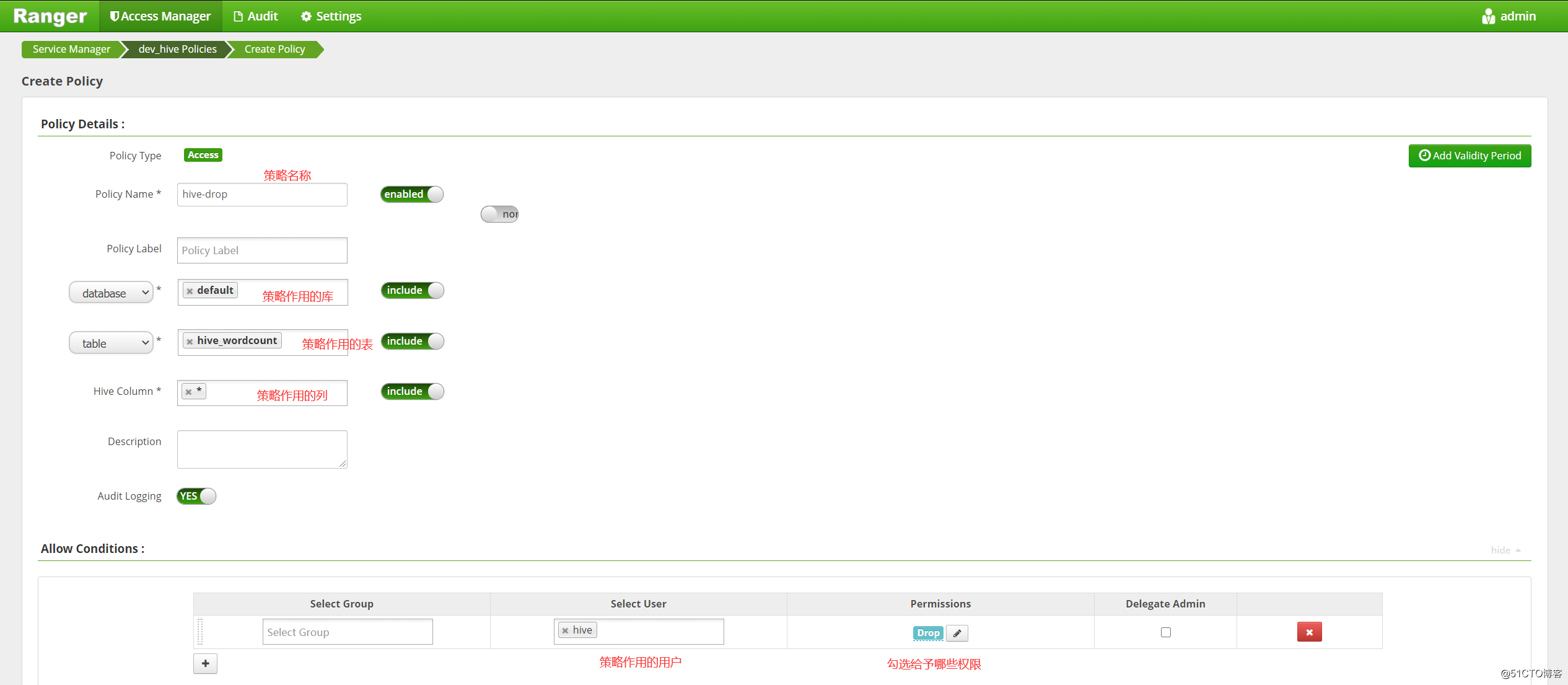
回到操作系统上,切换到hive用户,并通过beeline进入Hive的交互终端:
[root@hadoop ~]# sudo su - hive
上一次登录:四 11月 12 13:53:53 CST 2020pts/1 上
[hive@hadoop ~]$ beeline -u jdbc:hive2://localhost:10000 -n hive测试权限,可以看到除了show tables外的操作都被拒绝了:
0: jdbc:hive2://localhost:10000> show tables;
+-----------------+
| tab_name |
+-----------------+
| hive_wordcount |
+-----------------+
1 row selected (0.126 seconds)
0: jdbc:hive2://localhost:10000> show databases;
Error: Error while compiling statement: FAILED: HiveAccessControlException Permission denied: user [hive] does not have [USE] privilege on [*] (state=42000,code=40000)
0: jdbc:hive2://localhost:10000> select * from hive_wordcount;
Error: Error while compiling statement: FAILED: HiveAccessControlException Permission denied: user [hive] does not have [SELECT] privilege on [default/hive_wordcount/*] (state=42000,code=40000)
0: jdbc:hive2://localhost:10000> 因为我们只给予了hive用户drop hive_wordcount表的权限:
0: jdbc:hive2://localhost:10000> drop table hive_wordcount;
No rows affected (0.222 seconds)
0: jdbc:hive2://localhost:10000> 标签:second https hat release pat plugin radmin solr except
原文地址:https://blog.51cto.com/zero01/2550035